Prevent Tomorrow’s Attacks, Today.
Revolutionizing security with AI-powered, prevention-first solutions for every environment—cloud and on-premises. Stay ahead, stay secure.
Trusted by most popular brands



Join the Cyberattack Prevention Movement
Why SecPod?
Stop Attacks
Before They Start
Traditional cybersecurity waits for threats. We don’t. At SecPod, we believe in eliminating vulnerabilities before attackers find them.
![]()
![]()
Cyber threats evolve rapidly, and manual security processes can’t keep up. SecPod believes in automation-driven cybersecurity, where AI and real-time analytics enable organizations to detect, remediate, and comply with security standards faster and more efficiently.
Prevent Cyber Attacks for a Safer Tomorrow
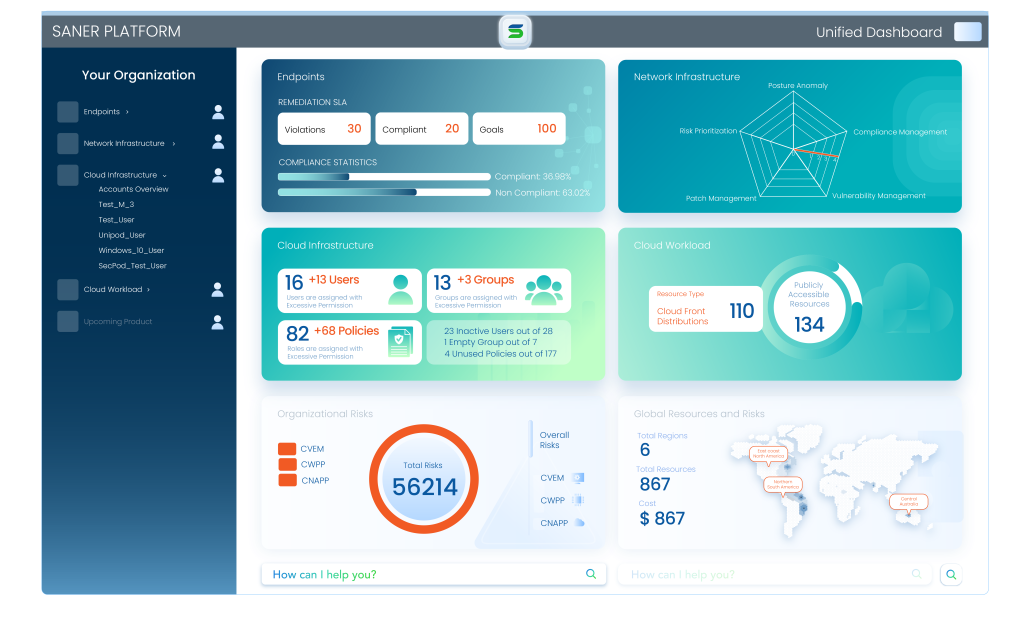
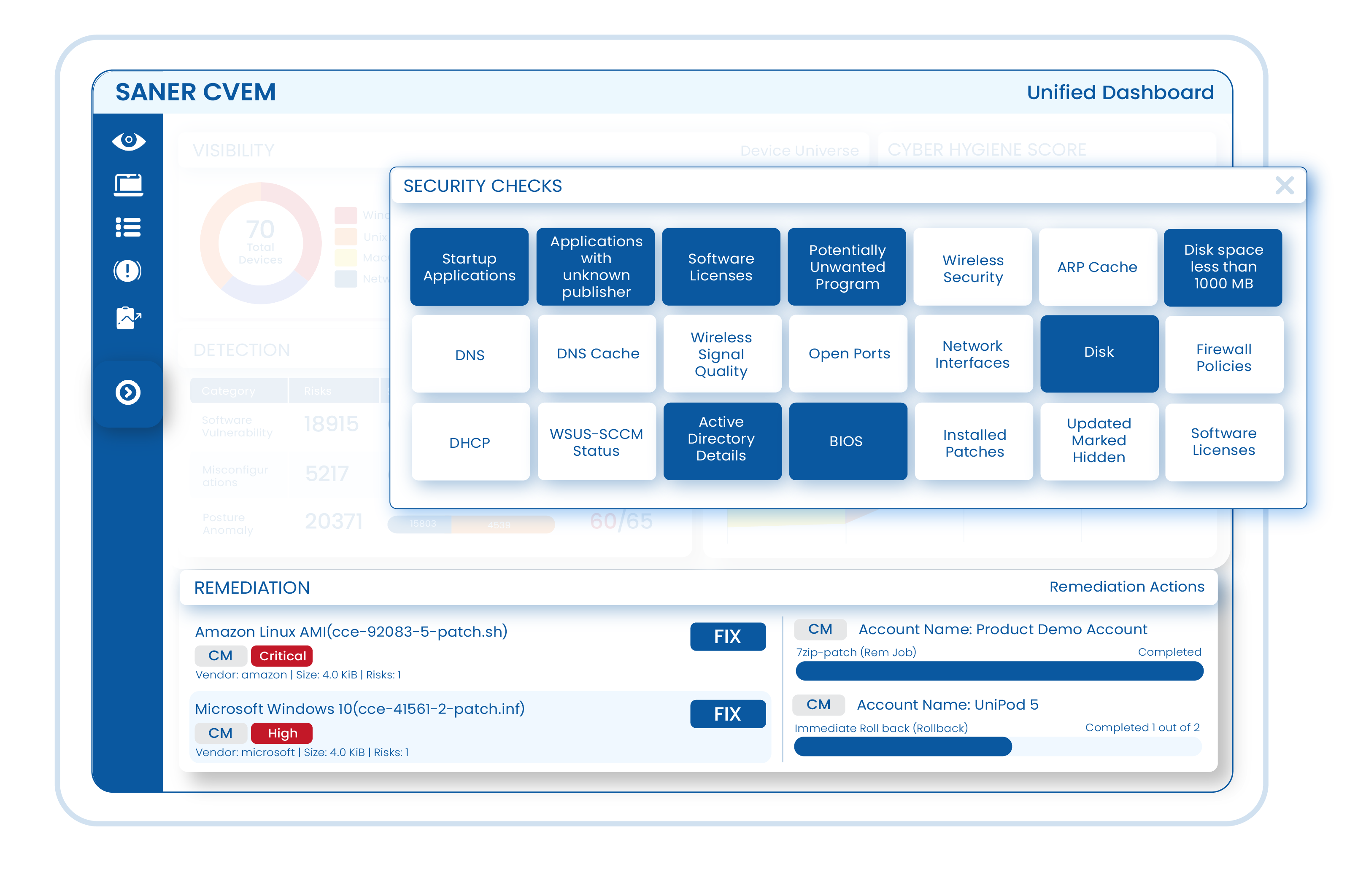
Saner CVEM
Continuous Vulnerability and Exposure Management
Intelligent. Automated. Continuous — Redefining Risk Management
Identify. Prioritize. Remediate. All in one platform, faster than ever before.
Lightning-Fast Discovery
Continuous scanning detects vulnerabilities and misconfigurations in minutes, not hours.
Smart Prioritization
AI-driven insights highlight the threats that matter most.
Regulatory Compliance
Stay audit-ready with benchmarks like PCI-DSS, HIPAA, and NIST.
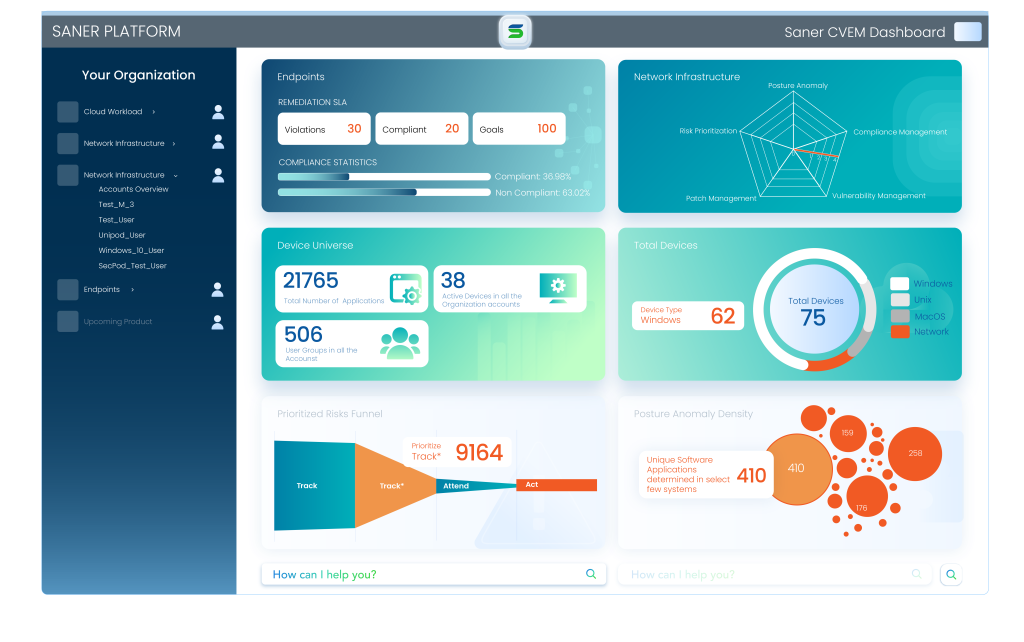
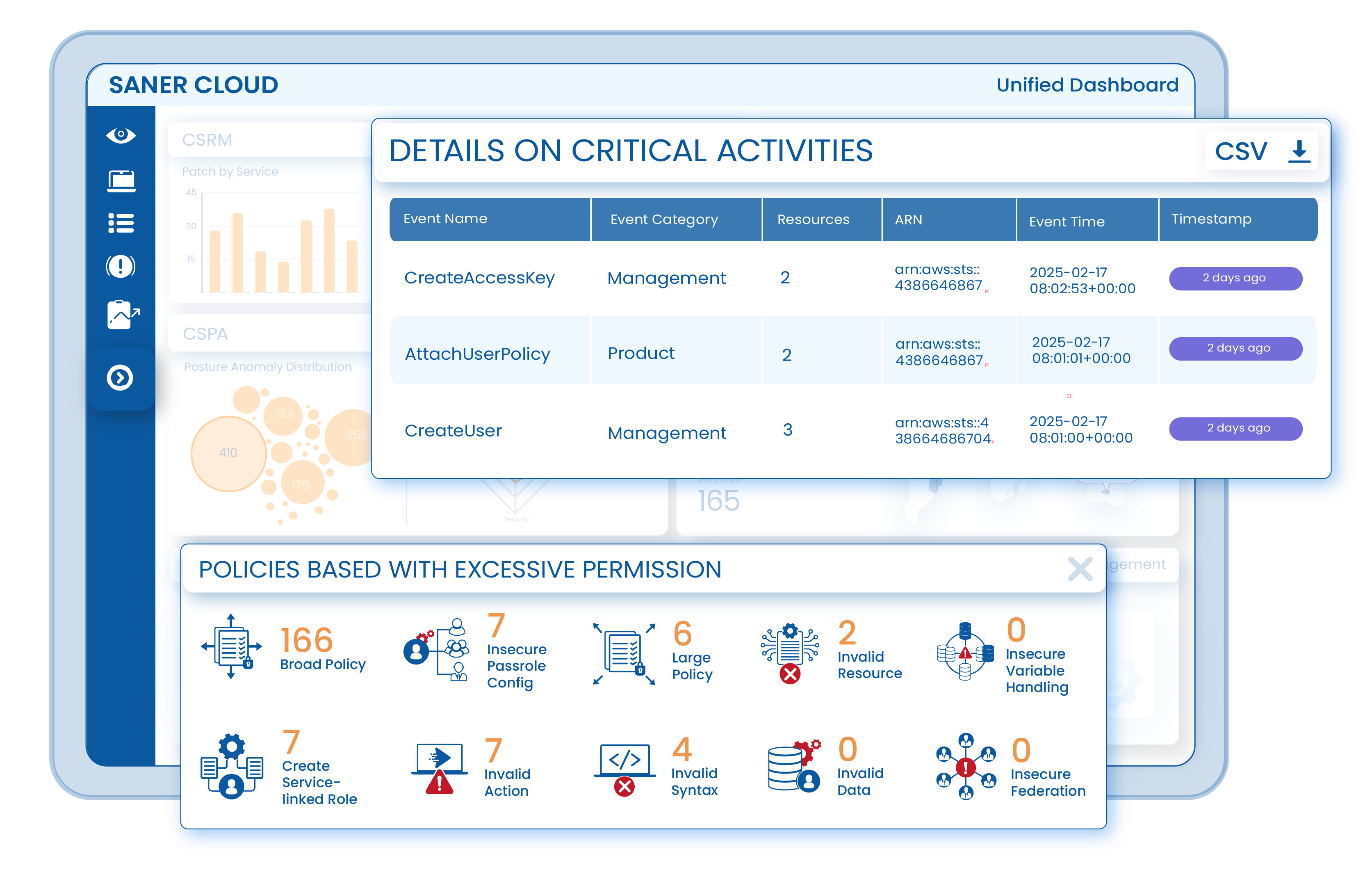
Saner Cloud
AI-Fortified Cloud Native Application Protection Platform
Unified Security, Continuous Compliance, Complete Control — All In One Platform
Built to prevent attacks, Saner Cloud empowers you to safeguard your cloud infrastructure, respond to threats faster, and maintain compliance with ease.
Comprehensive Security Posture Management
Continuously detect, assess, and remediate misconfigurations, vulnerabilities, and exposure risks across cloud and on-prem environments.
AI-Driven Posture Anomaly Detection
Leverage machine learning to identify deviations, enforce security baselines, and prevent breaches before they happen.
Automated Risk Remediation & Compliance
Instantly fix security gaps, streamline compliance with industry standards, and maintain a hardened security posture effortlessly.



























Featured Resources
The National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF) was published to help organizations make more effective...
With traditional vulnerability management programs severely struggling to cope with rapidly mutating and evolving cyber-attacks, there’s a desperate need to reinvent the existing process...
Cyber threats are evolving faster than ever, and relying on endpoint protection alone isn’t enough. Without built-in vulnerability management, even the most advanced EPP solutions leave gaps that attackers can exploit.
The chances of it effectively preventing cyberattacks are low, and the traditional method needs a significant revamp from the ground up.
What are the challenges and limitations of traditional vulnerability? Traditional vulnerability management has not changed or improved much in the last 20 years, leaving CISOs and IT security teams helpless.
A Leading Cloud Video Surveillance Software Manufacturer was in desperate need of a unified vulnerability management solution to handle their decentralized network and achieve SOC 2, Type 2 compliance.
Report 2024
The third quarter alone has reported a staggering 8596 vulnerabilities, marking a significant number of vulnerabilities. To help you be
Modern organizations are struggling to come up with and enforce effective patch management programs to combat increasingly complex cyberattacks.
A Leading Digital Banking Service provider was looking for a vulnerability management solution to transform their IT security from a traditional security approach.













