Saner Posture Anomaly Management
Detect Anomaly Before
You Are One
Get Holistic Visibility Over Your IT, Spot the Obvious Anomalies, and Eliminate them.
Measure Risk with
Detect Anomalies in
Exponentially Enhance by
Attain Holistic Cyber-awareness with Intelligent
Visibility over your IT
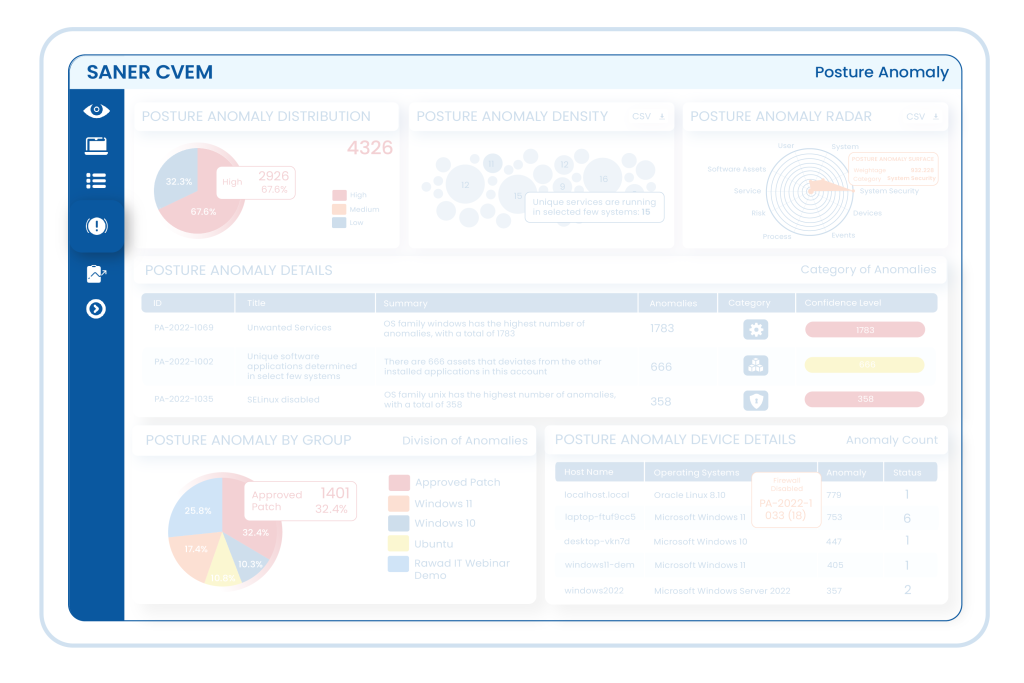
Saner Posture Anomaly Management discovers the aberrations, deviations, and outliers in your IT by holistically assessing your devices. By monitoring 100s of parameters across devices through statistical analysis, machine learning, and deviation computations, Saner CVEM uncovers potential risks and anomalies in your network.
SANER CVEM
Implement the Most Obvious Cyberhygiene Measure and Gain Rapid Security Mileage
Just gaining visibility over all the IT assets in your network is not enough to deal with sophisticated cyberattacks today. Saner CVEM’s Continuous Posture Anomaly Management allows you to go a step beyond and holistically assess your network to discover any deviations or aberrations that might lead to a potential attack. Spot a plethora of anomalies in your network from unusual services & processes, abnormal events in event logs, unwanted ports, unsigned applications, unusually executed commands, and much more hidden risks that threaten your organization’s security.

Improve Operational Efficiency with Comprehensive and Insightful Intelligence
More than 50% of cyberattacks today are due to unnoticed radical changes in your IT infrastructure. By identifying the most significant and noticeable deviations in your IT infrastructure, Saner CVEM’s Continuous Posture Anomaly Management provides intelligent insights which otherwise would have remained an unnoticed security loophole in the network. With intelligent insights, you can act upon these obvious security risks and prevent a wide range of cyberattacks even before implementing robust security measures.
Identify Anomaly Loopholes through Machine Learning, Statistical Analysis, and Deviation Computations
Saner CVEM’s Continuous Posture Anomaly Management comprehensively assesses the IT infrastructure and identifies the devices that are different than others. Through machine learning, statistical analysis, and deviation computation, the differentiation factors are comprehended, and security posture anomalies are detected in the network. Saner CVEM also provides the remediation measures to fix the anomaly instantly to help you build a solid cyberattack prevention foundation in your network.

Eliminate Uncertainties and Take Control of your IT Security Measures
With a holistic view of the IT infrastructure, you are more aware of the security risks that were once hidden. Saner CVEM’s Continuous Posture Anomaly Management allows you to discover the obvious attack vectors in the network and implement more effective security measures that will reduce risk exposures significantly. Along with managing vulnerabilities, misconfigurations, and other security risks, you now have control over the security posture anomalies that could have unleashed massive attacks.
Unparalleled Differentiators for an Unbreachable Defense
SanerNow Vulnerability Management software is built for your modern enterprise to fight the growing risk landscape
with advanced capabilities to scan, assess, prioritize, and remediate vulnerabilities on devices.
World’s Largest Built-in Vulnerability Database
World’s Largest Built-in Vulnerability Database
World’s Largest Built-in Vulnerability Database
World’s Largest Built-in Vulnerability Database
Discover and Remediate the Most Obvious Attack Vectors with Saner CVEM’s Out-of-box Capabilities
Run Daily Automated Scans and Discover Anomalies
Saner Posture Anomaly Management allows you to run daily scans to discover the anomalies in the IT infrastructure. You can schedule and automate these scans according to your organization’s requirements.
Identify Anomalous Posture through Statistical Anomaly Computation
Spot anomalous configurations and behavioural changes like vulnerable processes making outbound connection, unusual command execution, atypical firewall configuration, and much more by performing statistical anomaly computation.
Analyze Array of Security Controls and Spot Deviations
From disabled firewall, poorly configured WiFi security, enabled autologon, outdates OSs and software, to disabled BitLocker, analyze an array of security controls and spot the deviation in the settings that will harm the security posture.
Remediate all Anomalies with Built-in- actions
Saner provides an array of built-in-actions to remediate the discovered anomalies. You can also create your own detection rules to identify the anomalies and remediate them instantly from the same console to secure your IT environment.
Get Deeper Visibility and Fetch Intelligent Insights of your IT
Get deep visibility to over 100+ device parameters across your enterprise computing infrastructure. Fetch insightful information about your organization’s security posture with over 75+ anomaly computation rules.
Whitelist Necessary IT and Make it Known Good
Upon getting holistic visibility over your IT infrastructure, verify and whitelist the devices and configurations in your environment by assessing various parameters. Identify the posture anomalies and make your IT known-good.
Prioritize the Anomalies Based on Confidence Score
Saner analyses the discovered anomalies and determines a confidence score to prioritize the anomalies that needs immediate attention. Through this, you can remediate the high-priority anomalies quickly and reduce risk exposure to a large extent.
Examine your Security Posture with Insightful Dashboard and Reports
Understand your organization’s security posture through insightful visualizations. Perform outlier analysis of the gathered data and uncover interesting posture facts. Generate posture anomaly report and utilize 100s of report APIs to create custom visibility.

“Saner CVEM’s patch management capabilities stand out from the competition since it can patch all the discovered vulnerabilities and perform other system-hardening actions. Even if no direct remediation is available, Saner CVEM applies security controls that provide workarounds for the vulnerabilities.”
– Swetha Krishnamoorthy,
Senior Industry Analyst, Cybersecurity,
Frost & Sullivan






Intelligent Visiblity & Anomaly Normalization
Understand how Saner CVEM’s Posture Anomaly Management can provide intelligent visbility into security anomalies and rapidly normalize them.

Machine Learn Your IT Collectively and Identify Aberrations Through Statistical Analysis
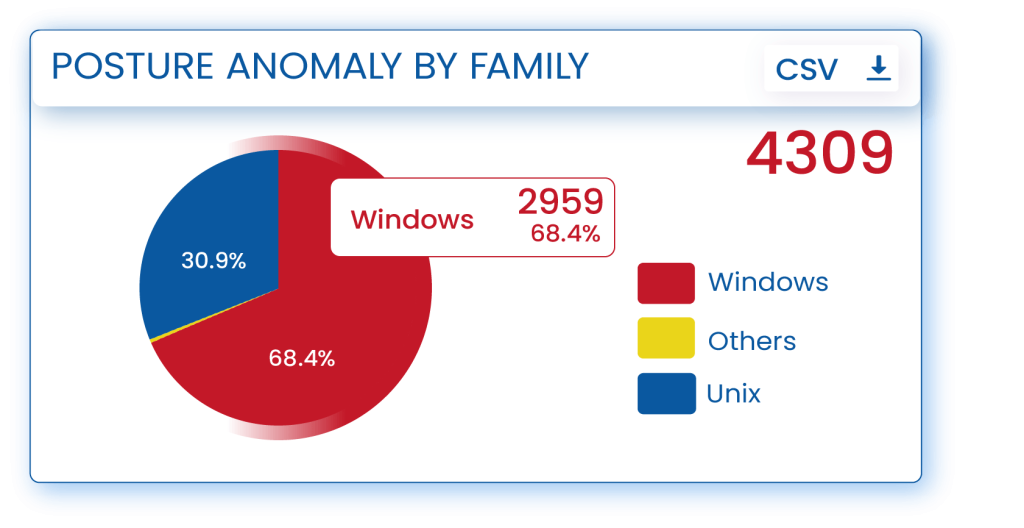
Using Machine Learning Concepts and Statistical analysis, Saner CVEM Continuous Posture Anomaly Management collectively assesses your IT infrastructure and discovers outliers or aberrations in the network. Saner CVEM identifies unfamiliar and unique applications that are installed, unusual services and processes that are running, atypical kernel versions, kernel modules or kernel parameters, irregular IP mapping, abnormal events, oddly executed commands, unwanted outbound connections to network ports, strange entries in task scheduler, autorun configurations, uncommon environment variables, and much more hidden risks in your IT network.Declutter your IT Infrastructure, Eliminate the Unnecessary Assets and Control Your SBOM (Software Bill of Material)
Let only known-good assets inside your IT infrastructure and eliminate the unwanted ones. Saner CVEM Continuous Posture Anomaly Management allows you to identify the unwanted applications, services, processes, and network ports; inspect scheduled tasks, run level programs and environmental variables; detect the number of VPN tools used in the network, discover cloud applications and file transfer apps, apps from unknown publishers, and unsigned executables. By discovering all these outliers, you can easily declutter your IT infrastructure, allow only the essential assets, and manage your SBOM (Software Bill of Material).Get a Microscopic View of Your IT and Discover the Unknown Security Risks
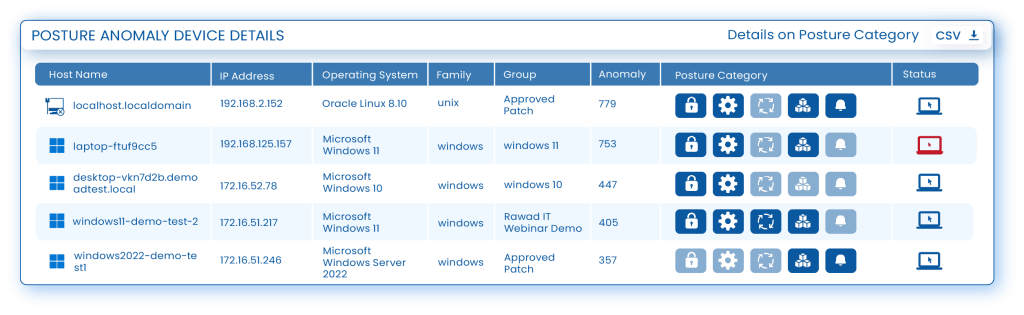
Explore and learn about your environment in a way you haven’t seen before, and be surprised by what you find. Track the changes in IP, HOST, and MAC addresses; analyze why so many VPN client applications are in use; find out the aberration in firewall configurations in specific systems; identify why a signed application is unapproved in certain systems; discover inactive users and different user privileges, and a lot of obvious hidden risks, and safeguard your network from a potential cyberattack.Monitor Security Controls and Identify Deviations in Functioning
Security controls are essential to be up and always running to protect the network from security mishaps. With Saner CVEM Continuous Posture Anomaly Management, ensure Endpoint Protection Software is always functioning, WiFi security configuration is analyzed and strengthened, user identity is configured properly, BitLocker is enabled, DEP/ASLR/SELinux enabled for threat protection, Device Firewall settings are appropriately configured, Gate Keeper and UEFI boot is enabled, Time synchronization issue is detected, and Device shares are determined. By ensuring all these Security Controls are functioning without deviation, you establish a robust security posture in your network.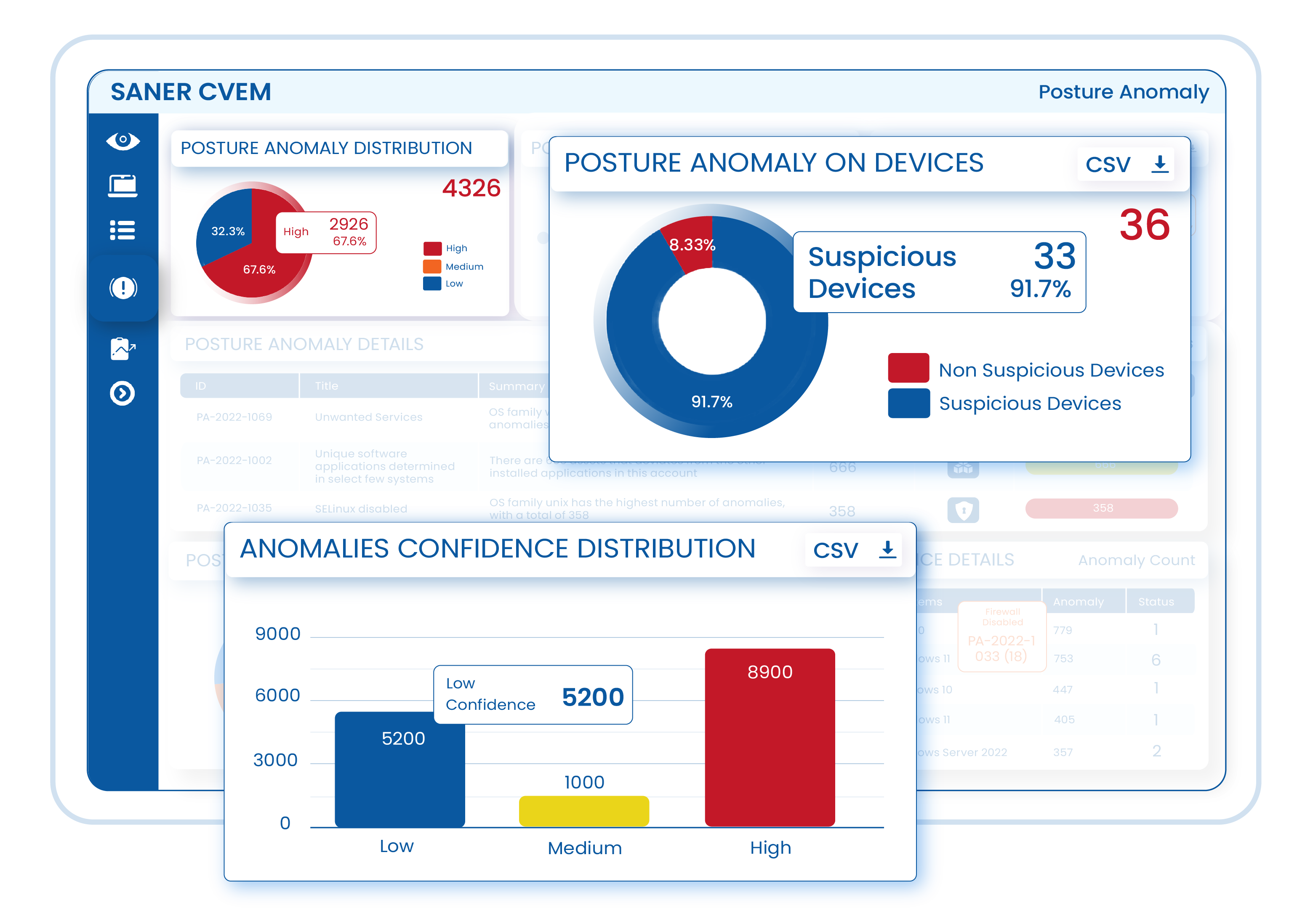
Global Enterprises trust Saner CVEM to Secure their Dynamic IT Environment
A great endpoint security & management platform
Founder & CTO
Large Enterprise, BFSI Sector
Best value in vulnerability and patch management
Chief Security Officer
MSSP, IT Sector
Know your info security posture with Saner CVEM
Security Consultant
Large Enterprise, Healthcare Sector











