Cloud Based Vulnerability Management
Cloud Based Vulnerability Management
What is Cloud Based Vulnerability Management
Cloud based vulnerability management tool offers a universal view of cloud-enabled IT infrastructure, which might be prone to vulnerabilities. It also helps to secure the devices distributed across various locations. It helps IT admins monitor vulnerabilities in the network at the comfort of their place. In terms of managing them, cloud vulnerability scanners allow enterprises to discover and report security gaps in their IT network. However, cloud scanners are just a part of a holistic vulnerability management platform.
In general, a full-fledged vulnerability management software should support all operations from detection to remediation. It aids in managing the vulnerabilities effectively in both on-premises and cloud environments.
How Does Cloud Based Vulnerability Management Work?
The cloud based vulnerability management cycle has four steps, and they are.
- Identification
- Assessment
- Prioritization
- Remediation
Identify: Cloud-based security identification process involves scanning for flaws in applications and devices available in the entire IT network. Cloud vulnerability scans help keep track of various IT security flaws without a physical presence in the computing environment. As a result, it saves an IT team’s precious time and resources in a company. Enterprises use cloud-enabled vulnerability management tools equipped with lightweight agents to perform continuous scans and detect vulnerabilities.
Assess: The next step after obtaining the scanned report is to assess the vulnerabilities and determine their severity. The entire scope of assessment in cloud vulnerability management platform depends on the scanned report. The assessed report explains the exploit potentials of the vulnerability and its type. According to the objectives of the assessment, the data collected from various devices are compared with the known vulnerability database. The vulnerability management tool helps IT admin import data to cloud servers and retrieve the final assessment report.
Prioritize: It is essential to determine the severity of the vulnerability in the context of each IT asset. The need to address the critical flaw in an application may not be the same in an IT asset of minor importance. IT security experts use CVSS scores to decide the actual risk of vulnerabilities.
Prioritization helps enterprises manage high risks effectively using limited resources. The method helps the IT team remediate high-risk vulnerabilities first and prevent cyber threats.
Remediate: The cloud-enabled network is different from the traditional on-premises computing environment. And the vulnerability remediation process differs as the cloud service providers also play the role of protecting the cloud network.
Cloud based vulnerability management platform do not use traditional patching methods to address the security flaws in applications. Here, IT experts integrate cloud-based vulnerability management tools with the cloud environments and get vulnerability data of their assets. The overview of the entire asset risk is assessed and remediated as per the severity level. Application vendors release the necessary patches to deal with the vulnerabilities in the cloud network, and it is deployed immediately as a part of effective remediation solutions.
Difference between On-Premises and Cloud Vulnerability Management
On-premises vulnerability management system is time-consuming and requires physical access to address any flaws in the network. Here, an enterprise secures its sensitive business data and assets. Also, it demands enormous resources to remediate or mitigate security issues whenever they arise in the network. Most small and medium-sized enterprises with on-premises environments face several challenges due to the massive remote work practices during the pandemic. The key priority in the fast deployment of the remote working space is an effective vulnerability management software. Before the pandemic, companies opposed remote working as it was tedious to secure all the devices on a distributed network. They were also unprepared for the upsurge in possible cyberattacks.
In some companies, employees’ personal devices have not complied with standard security protections while accessing any corporate data. There are more accessible and practical ways in cloud-based vulnerability management system that help companies implement security measures without interrupting the current working style of employees.
The cloud technology allows an IT admin to validate individual requirements on personal devices before allowing access to corporate data or applications.
In a cloud solution, data security is handled by the cloud server as it is backed by solid security teams, necessary tools, and technologies. The scanned vulnerability report is directly transferred to its respective cloud server, which houses the remediation solutions. It helps companies manage their entire network remotely using cloud-based vulnerability management.
SanerNow’s Cloud Based Vulnerability Management
SanerNow Cloud based Vulnerability Management Platform is an integral part of the Cyber-hygiene platform, hosted on the cloud. The SanerNow server is also hosted on a cloud platform to perform all vulnerability management tasks across the IT network.
SanerNow’s cloud vulnerability management platform works on a lightweight agent server model. The multifunctional agent is installed on all the devices to execute the tasks from detection to remediation. The agent also takes up the role of network scanner to scan other devices, saving investments on additional hardware. Some of the features of SanerNow are:
Industry’s Fastest Vulnerability Scanning and Accurate Detection:
SanerNow performs the industry’s fastest scan to detect vulnerabilities in less than 5 minutes. SanerNow leverages the home-grown world’s largest vulnerability feed with more than 175,000 security checks making vulnerability detection accurate. These scans can be scheduled and automated according to the organization’s requirements.
Intact Assessment and Prioritization:
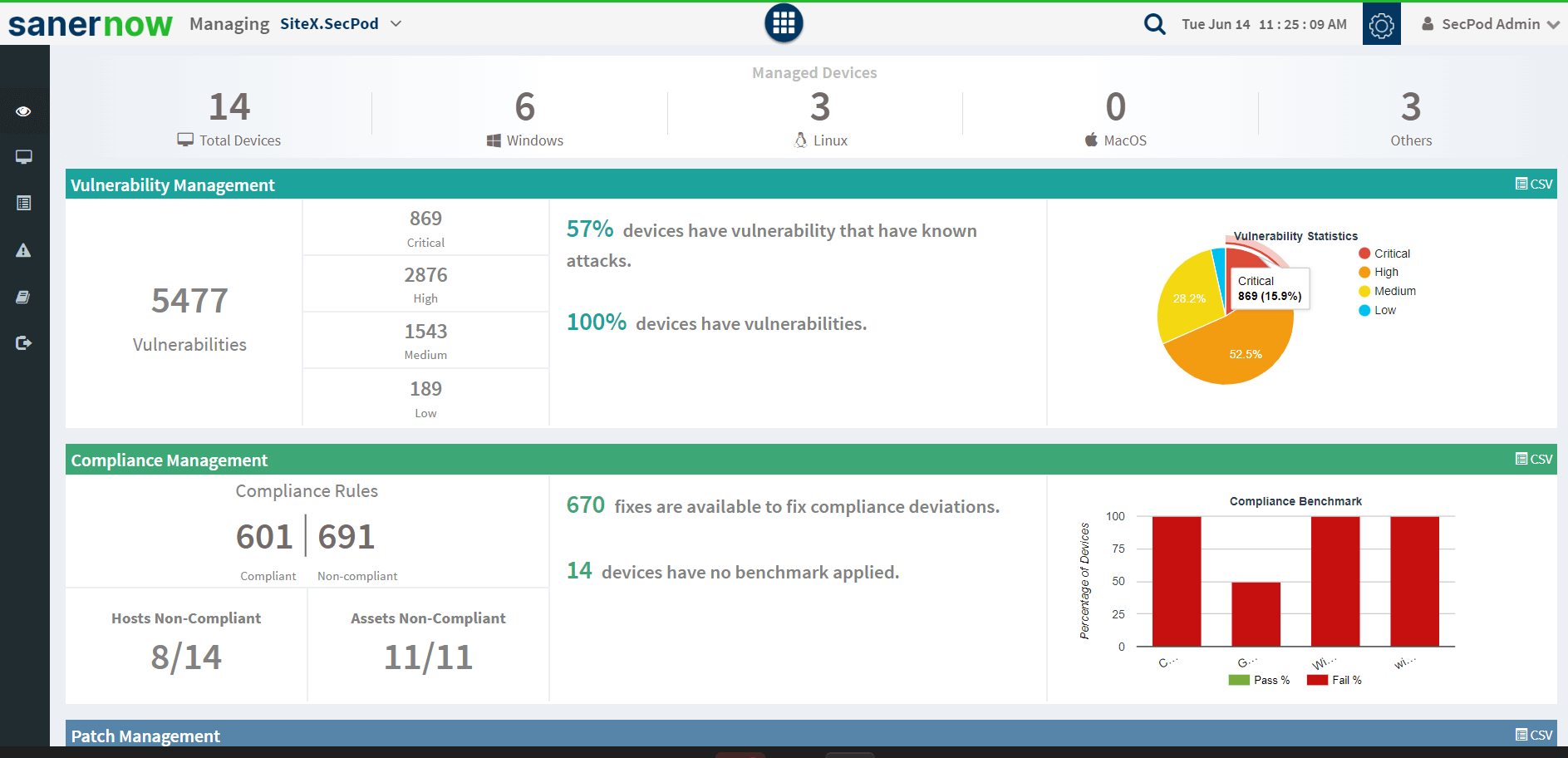
SanerNow’s cloud based vulnerability management tool assesses scanned vulnerability reports as per the exploit potential, types, and severity level. The accessed data is then prioritized to help the IT experts maximize their remediation efforts on high-risk vulnerabilities. SanerNow also helps enterprises obtain the report remotely at any time, as it is entirely built on a cloud platform.
Timely Remediation with Integrated Patching:
SanerNow helps IT experts manage all critical vulnerabilities using an integrated patch management tool and remediate them faster. SanerNow’s patch remediation supports all major operating systems and 450+ third-party applications.
Insightful and Customizable Reports:
SanerNow cloud-based vulnerability management offers a comprehensive report which involves various ways to represent vulnerability data. It is essential to remediate the security gaps in a computing network and evaluate the effectiveness of the vulnerability management platform. An enterprise can view these in-built reports in a single cloud-based console and find recommended solutions to various cyber security gaps.