Saner Cloud
Cloud Workload Protection Platform Solution (CWPP)
Comprehensive Workload Protection for Secure and Scalable Cloud Operations

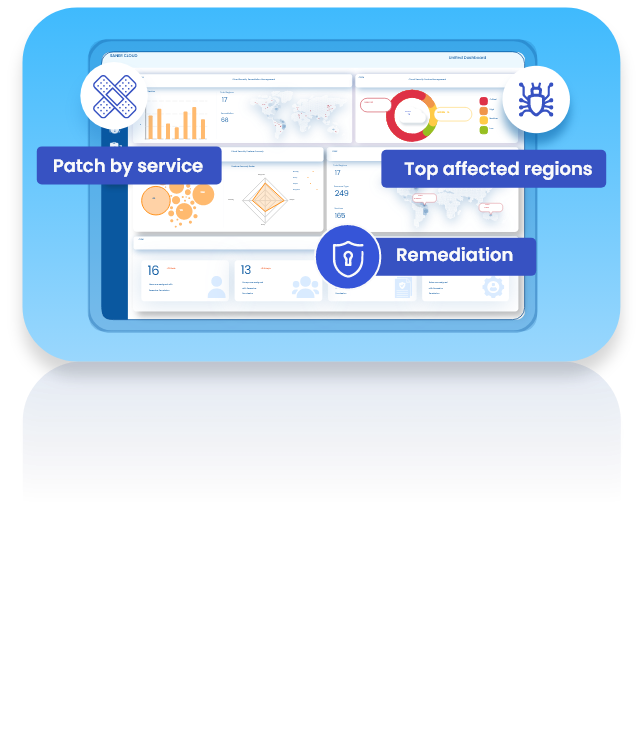


Unifying Security, Compliance, and Efficiency for Cloud Workload Protection
Organizations require integrated approaches to effectively manage security challenges, operational complexities, and compliance mandates. Saner Cloud delivers a Cloud Workload Protection Platform (CWPP) designed to address these needs through a unified framework combining seven advanced capabilities.
The CWPP solution bundle allows teams to manage and protect cloud workloads with precision while maintaining efficient operations across cloud environments.
Addressing Cloud Workload Challenges
01
Dynamic ecosystems
Sophisticated threats
02
03
Compliance mandates
Operational overload
04
Simplifying Cloud Compliance and Exposure Management
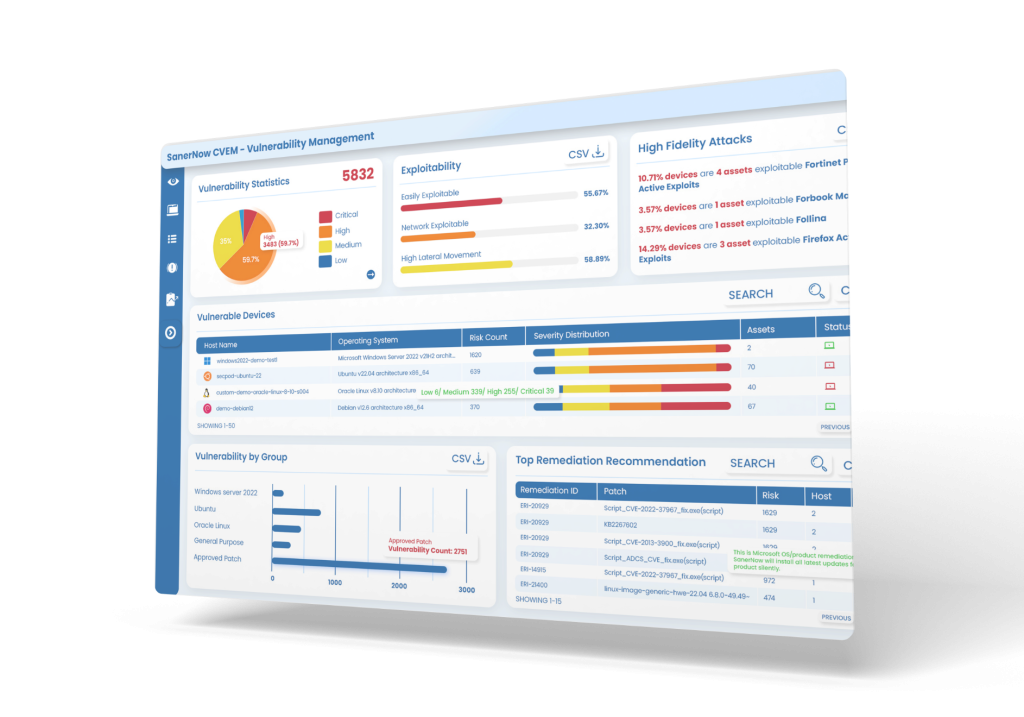
CSAE complements compliance management with tools designed to help you better manage asset exposure, prioritize remediation, and maintain an up-to-date inventory of all your cloud resources across geographies.
Why Choose Saner Cloud’s CWPP Bundle?
Saner Cloud brings together workload protection, compliance, and operational management in one platform. Our approach simplifies complex processes while providing actionable insights into risks, compliance gaps, and operational inefficiencies.
AI-powered insights
Risk analysis is prioritized based on both technical and business contexts.
Streamlined operations
Automated processes reduce manual workloads for security teams.
Comprehensive oversight
Continuous monitoring improves visibility across multicloud environments.
Adaptable solutions
Supports diverse infrastructures, from virtual machines to containerized applications.
Getting Started with Saner Cloud’s CWPP Solution Bundle
01
Setup
Agents or agentless scanning can be deployed within minutes.
The platform integrates with major cloud providers like AWS and Azure.
02
Monitoring:
Scans can be scheduled for continuous updates on vulnerabilities and compliance statuses.
Dashboards present live data for quick and informed decision-making.
03
Remediation:
Step-by-step workflows guide teams through resolving identified issues.
Patches and configuration updates can be applied instantly for optimal results.

Automated vulnerability scanning continuously assesses workloads and cloud assets for weaknesses. A vast and constantly updated database ensures up-to-date security intelligence.
Scans both internal and external workloads across multicloud environments, including perimeter-less setups where traditional security tools might fail. Such an approach to cloud security guarantees a full spectrum of protection, from cloud-native workloads to traditional assets.
Distributed network scanners provide deep insights into asset vulnerabilities, including hard-to-reach external endpoints, enabling comprehensive risk evaluations.
AI-based models prioritize vulnerabilities by combining exploitability, severity, and the business impact of affected workloads, allowing security teams to focus on what matters most.
Detailed remediation instructions are included for each detected vulnerability, complemented by automated workflows that apply fixes at scale, reducing operational overhead.
Organizations can automate compliance checks and maintain alignment with diverse regulatory frameworks, reducing the effort required to adhere to various industry mandates.
Pre-built checks cover widely recognized standards, such as NIST, PCI DSS, and HIPAA. For unique organizational needs, users can define and enforce custom policies, ensuring tailored compliance oversight.
Misconfigurations and violations of compliance policies are automatically detected, flagged, and corrected without delays, maintaining a proactive approach to compliance.
Audit-ready reports are generated automatically, consolidating information on compliance status, violations, and remediation actions, simplifying external audits and internal assessments.
Posture Anomaly Management enables the detection of security gaps, misconfigurations, and behavioral deviations in near real-time, helping to secure cloud environments against advanced threats.
Uses machine learning (ML) algorithms to analyze deviations from baseline configurations, touching upon risks such as unauthorized software installations or deviations in workload behavior.
Posture is evaluated daily with over 75 rule-based checks, covering critical areas such as network policies, configuration errors, and workload behaviors, ensuring issues are caught early.
Automated alerts notify teams of potential risks, such as privilege escalations, lateral movements, or data exfiltration attempts, providing actionable insights for mitigation.
Detected anomalies can be resolved directly through the platform, using automated workflows to apply fixes or isolate problematic workloads immediately.
A unified inventory of cloud resources provides visibility into all assets, enabling organizations to minimize risks associated with shadow IT and exposed endpoints.
Identifies unmanaged or unauthorized assets — such as workloads spun up without IT approval — that pose a security risk, enabling teams to take corrective action.
Pinpoints publicly accessible endpoints and outdated resources that could become entry points for attackers. AE includes identifying vulnerable APIs, unused ports, and misconfigured storage buckets.
Assets are grouped based on their type, usage patterns, and criticality, helping teams quickly understand the context of their cloud resources and prioritize actions.
Tracks the usage of resources to identify redundancies, reduce waste, and improve the efficiency of cloud expenditures while eliminating unnecessary attack surfaces.
Advanced risk prioritization ensures that security teams address the most impactful vulnerabilities first, based on AI-driven insights and industry-standard frameworks.
Vulnerabilities are analyzed for their likelihood of being exploited, allowing security teams to focus efforts where they are most needed and reduce unnecessary remediation.
Threats are aligned with real-world attack tactics and techniques, enabling security teams to address risks within the context of known adversarial behaviors.
Provides an easy-to-understand representation of how vulnerabilities connect to potential exploits, helping teams quickly identify optimal mitigation strategies.
Identifies and prioritizes risks associated with workloads or resources that are of high business importance, ensuring the protection of mission-critical assets.
Patch Management automates the deployment of updates across cloud environments, reducing vulnerability windows and operational disruptions.
Patches are applied across operating systems, software dependencies, and container images through a centralized process that reduces manual intervention and accelerates updates.
High-profile vulnerabilities, including zero-day exploits, are addressed with one-click emergency patches, minimizing exposure while maintaining operational continuity.
Supports advanced patching scenarios with pre- and post-patch scripts that empower organizations to implement specific workflows for seamless integration into existing processes.
Tracks and documents patching activities to make sure all updates align with organizational policies and regulatory requirements, making it easy to demonstrate compliance.
Workload Management simplifies the monitoring and control of workloads across multicloud environments.
Security teams can define which application are permitted to run on workloads, restricting unauthorized software from executing and reducing potential attack vectors.
Compromised workloads can be isolated instantly to prevent lateral movement and further compromise of the cloud environment.
Custom workloads allow automatic resolution of performance or security issues, reducing downtime and the burden on IT teams.
Workloads are kept in line with organizational policies by enforcing configuration such as firewall rules, kernel settings, runtime permissions, maintaining both security and performance standards.
Pricing and Packages

FAQs and Support Information


