Vulnerability Remediation Best Practices
Vulnerability Remediation Best Practices
A growing number of businesses understand the importance of patch management software. In an extensive IT network of organizations, the complexity of the devices is constantly growing. As the number of devices, applications, and other IT assets increases, they become vulnerable to attacks, negatively impacting business revenue and operations. It is hard to monitor large computing environments constantly and remediate security flaws. Therefore, proven methods or practices in remediating vulnerabilities using a vulnerability management tool is necessary for organizations.
What is Vulnerability Remediation
Vulnerability remediation is one of the crucial steps to eliminate the threats in the vulnerability management process. It depends on various other stages like identifying, assessing, and prioritizing the flaws in devices and applications. Monitoring several measures as part of the vulnerability remediation process is necessary to enhance the outcomes.
How does the Vulnerability Remediation Process work
The first step of the remediation process is to identify the risks involved in the IT network. It is performed through on-demand or scheduled scanning for vulnerabilities. However, the most complex part is to figure out the severity level of the thousands of vulnerabilities. It is addressed during the assessment stage. Then, the vulnerability remediation process is initiated as per the severity level.
Ways to Remediate Vulnerabilities:
One of the preferred ways to remediate vulnerabilities is by deploying patches to the relevant vulnerabilities. Firstly, a vulnerability management software assesses the scanned vulnerability reports and ranks them from the most critical ones to the least. Furthermore, the patches for high-risk vulnerabilities are obtained from respected software vendors and deployed immediately. The less critical ones are mitigated later, depending on their impact on the business. The various stages involved in the remediating process avoid IT teams being overwhelmed by the sheer volume of possible threats.
Here are a few Vulnerability Remediation Best Practices
An inefficient and outdated practice of vulnerability remediation will fail to deal with the increasing need for securing the modern IT network. Today’s business organizations need the best vulnerability management tool and practices to organize better and ensure their computing network is secure. Some of them are as follows:
Perform Continuous scan
Performing scans once a month or quarter will not deliver real-time vulnerability data. Since vulnerabilities are discovered daily, a continuous scan is essential to get real-time data of the entire IT network.
Establish a Strong Set of Key Performance Indicators (KPIs)
A vulnerability manager is monitored and optimized constantly by setting up strong KPIs. Moreover, these indicators help IT security teams gauge the program’s effectiveness and identify the challenging issues that need an immediate fix. Some of them are:
- Scanning Frequency
- Scanning Duration
- Coverage of the Scan
- Average remediation time
- Age of Vulnerabilities
Understand your IT Infrastructure
Large organizations are equipped with hybrid IT infrastructure. The traditional vulnerability management tool has become outdated to fulfill a hybrid network’s needs.
Due to the pandemic, employees have started working remotely, which resulted in more personal devices and tools connecting to their company’s IT infrastructure. It has increased the attack surface of enterprise IT networks. The applications and devices have become interconnected, borderless, and dynamic. Therefore, organizations should always understand their entire IT network and attack surface.
The vulnerability remediation process should effectively cover the hybrid network and detect security flaws faster for quick remediation.
Leverage the Large Database of Vulnerability Checks
Enterprises need to attain perfection while detecting vulnerabilities in the network. The accuracy of the vulnerability scanning process depends on the vastness of the available security checks database. The scanner compares security flaws in all assets against the database. Therefore, it is evident that the larger the vulnerability database, the higher the accuracy of the report.
It is important to leverage the large and updated vulnerability database to ensure that the scanner detects all security issues accurately. If the database is fed periodically with the latest security checks, the IT team can feel safe knowing that the scanner doesn’t give you a false positive report.
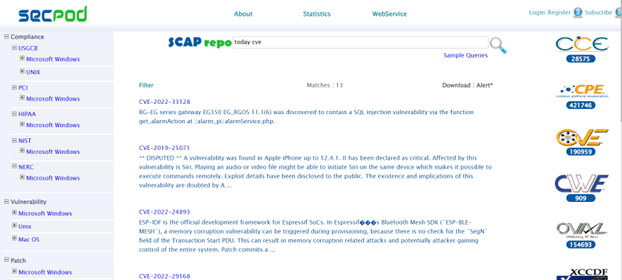
Prioritization of Scanned Vulnerability Report
The risk level of a vulnerability differs in each network. The same vulnerability present in a different network of organizations might pose a different level of risk. Several factors contribute to the risk of vulnerability in your environment.
After obtaining the scanned vulnerability report, IT admins prioritize them as per the risk level. Various factors contribute to the risk level in the computing environment. The severity level varies depending on the organization’s IT infrastructure. Vulnerability prioritization is an important step before the vulnerability remediation process. Some of the matrices involved in prioritizing the vulnerability report are as follows:
- CVSS scores
- Exploit data
- Number of assets reported with the same vulnerability
- Impact of the vulnerability
Timely Remediation
Remediating a vulnerability on time makes a lot of difference to an enterprise’s real-time security risks management. Cyber attackers may easily exploit old vulnerabilities faster if it remains hidden in the IT network. To prevent such future threats, timely remediation of the issues is essential. Identifying vulnerabilities and remediating them is crucial. And it works well if both processes are integrated into a single vulnerability remediation tool. It should perform scans, assess, prioritize and remediate the issues in one go.
Automate Vulnerability Remediation
Vulnerabilities in a hybrid enterprise network appear in large numbers. If the remediation process is manual, it fails to secure the network and increases the attack surface. Businesses can overcome such security concerns using an automated vulnerability management process. It fastens the entire cycle of the vulnerability management process, which involves detection, assessment, and remediation, saving a lot of IT resources to business organizations.
By following the above vulnerability remediation best practices, you can easily increase the overall efficacy of your vulnerability remediation process.
How to Remediate Vulnerabilities with SanerNow
SanerNow Vulnerability Management Platform is hosted on a cloud platform backed with a database of more than 175,000 security checks. SanerNow eases the overall vulnerability remediation process in four stages, and they are:
Identification
SanerNow runs the industry’s fastest scans and identifies vulnerabilities in less than 5 minutes. It allows IT admins to schedule and automate the scan every day using the agents installed on all endpoints.
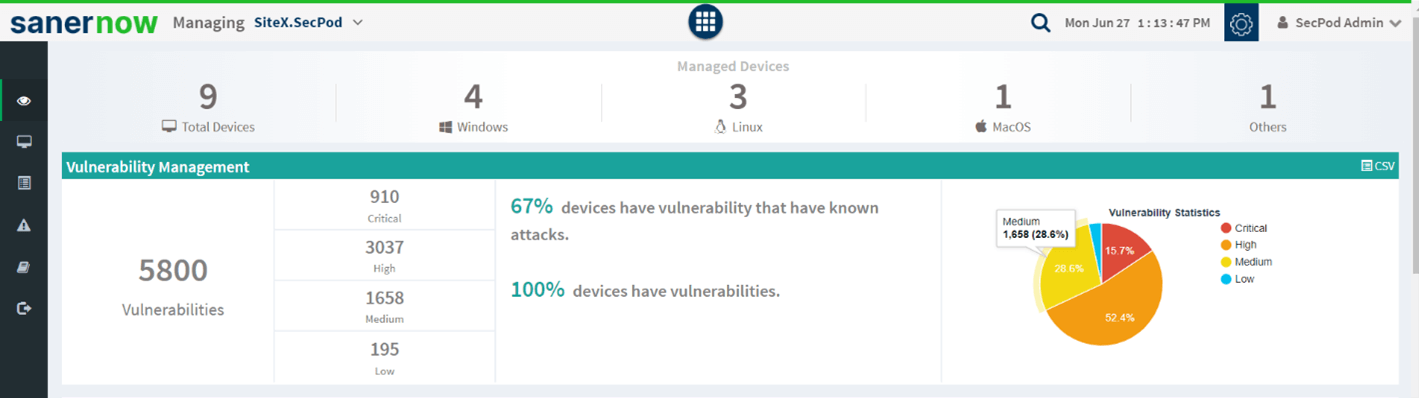
Assessment
The scanned report is assessed using various matrices such as CVSS score, exploit data, asset information, etc. The vulnerability is then assigned a score as per the exploit level.
Prioritization
SanerNow assesses the risks and prioritizes the vulnerabilities as per the severity level. It helps to determine the high-risk vulnerabilities that need vulnerability remediation immediately. IT security experts can use the risk data and employ their company’s resources during remediation.
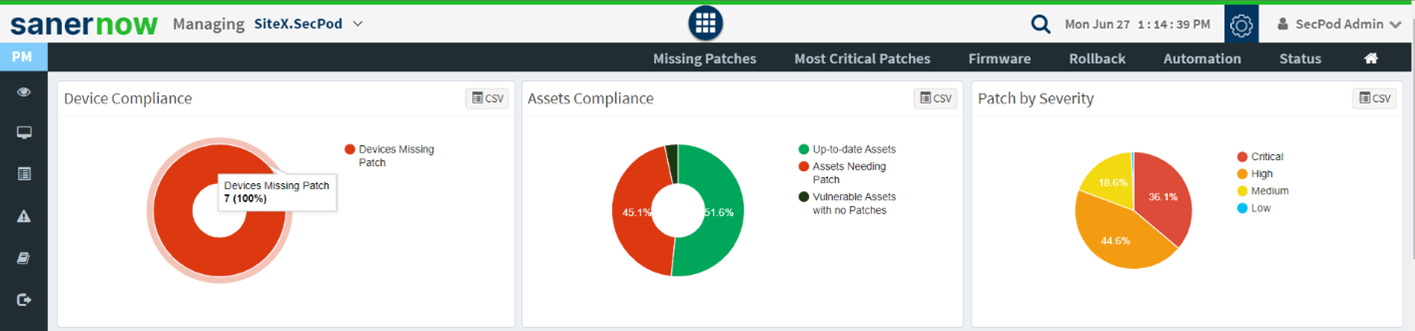
Remediation
SanerNow’s integrated patch management solution provides a rapid vulnerability remediation process. It supports patching for all major OSs and more than 450+ variety of third-party applications.
SanerNow is equipped with all the required features to orchestrate vulnerability remediation best practices to manage attack surfaces efficiently.

