Vulnerability Management Essentials
Vulnerability Management Benefits
Cyber security threats are continuously evolving in today’s information world. It is affecting sensitive business data and devices. Identifying the security flaws in assets and exploiting them is a well-known attacking method for hackers. Therefore, discovering these weak spots in a computing network and protecting them against exploits is one of the main objectives for an enterprise. This can be done by using a vulnerability management software.
Generally, small and middle-sized companies are the ideal targets for hackers because they have fewer resources to protect their IT networks. Hackers look for vulnerabilities that grant them access to the network and business data they want. Detailed scanning by using a vulnerability scanner of all assets in an organization provides a list of extensive reports on security flaws; however, it is a long way to go before you start remediating them. As a result, risk-based vulnerability management tool should be an integral part of business organizations. It helps to make informed IT security decisions with optimal solutions.
Top Vulnerability Management Benefits
Enhanced Security:
Security flaws in applications offer an opportunity for hackers to enter into the computing network. It is vital to identify these weaknesses to secure the entire asset and business data. Then, these issues are assessed and prioritized as per the severity level. The assessed report helps to remediate the flaws in network scanning and protect them from cyber-attacks, resulting in security breaches in the network.
In addition, IT security teams can identify vulnerabilities remotely without needing physical presence in the computing environment. It helps also helps them handle high-risk issues with minimum IT resources.
Immediate Fix of Vulnerabilities:
Every year, organizations discover thousands of new cybersecurity flaws that require patching applications, operating systems and reconfiguring network security settings. These issues need immediate solutions to prevent attackers from exploiting security flaws in the IT network.
Some of the real-time vulnerability manager offers integrated patch remediation solutions. It helps businesses automate the remediation of the vulnerabilities that repeatedly appear in their network. It also enhances the effective utilization of the resources on new ones.
Operational Efficiencies:
The assessment of the vulnerability list helps IT security experts remediate the most critical IT security issues first and address the minor ones later. If the impact of the possible threats to the business is determined, it eliminates the confusion during the remediation process. Organizations can also automate and manage vulnerabilities remotely. As a result, it reduces the burden of owning and maintaining hardware and software updates, saving time and increasing operational efficiency.
A comprehensive vulnerability management platform minimizes the security team’s efforts to a great extent. There will be limited IT resource required to mitigate the possibilities of cyber-attacks and strengthen the security posture.
Visibility and Reporting:
Compiling the vulnerability reports manually across hundreds of assets will create havoc on the visibility of the security teams. Using traditional techniques, showing the vulnerability data from one scan to another is difficult. Therefore, a comprehensive vulnerability management solution with an actionable dashboard is essential. It offers severity level of the security flaws, charts, recommendations solutions, and generates customized reports, which helps make a compelling case for new security initiatives.
As a result, an IT team makes better-informed security decisions in securing their computing environment. Also, they can start the remediation process right after every report. It increases productivity, reduces team fatigue, and enables them to eliminate guesswork.
Features of Vulnerability Management tools
Choosing the best vulnerability management tool is vital for maximum output while remediating cybersecurity flaws. Understanding the tools’ vulnerability management benefits and essential features is very important. Some of the features are as follows:
- Automated Scanning
- Assessment & prioritization
- Integrated patch remediation
- Insightful reporting
- Cloud-based solutions
Automated Scanning:
The purpose of scanning IT assets is to identify vulnerabilities. Several automated vulnerability scanning tool can perform on-demand and scheduled scans without interrupting end-user performance. It helps assess and prioritize the risks based on the patches’ severity level, age, and availability.
Assessment and Prioritization:
This stage helps gather details on the security flaws in the network and prioritize the vulnerable assets as per the severity level. Some data matrices used here are the CVSS score, exploit data, asset information, and many more. This data helps establish and maintain computing networks secured from many attack variants.
Integrated Patch Remediation:
The patches are deployed automatically to the respective vulnerabilities with integrated patch remediation. The feature helps deploy patches on different OSs and third-party applications. It also offers information that an attacker may use to exploit. As a result, critical security issues are easily patched before being exploited.
Insightful Reporting:
The entire effort to secure the IT network becomes futile if companies fail to obtain insightful reports. Security experts need insights on critical risks, remediation progress, assessment data, security regulations, etc., to meet the evolving information security standards. It should also offer unified visibility and better tracking from detection to closure of all issues from a single console.
Cloud-based Solutions:
The best vulnerability management practices are implemented and managed remotely using dedicated cloud-enabled tools. It offers complete visibility into both on-premises and cloud environments. It facilitates businesses to function in a secure and protected cloud with an agent and sever model.
How Vulnerability Management Tools Prioritize Threats
Business organizations use various methods to handle vulnerable assets. It ranges from defining the best practices to filtering out the most critical security flaws in the IT assets.
The vulnerability scanning process generates a detailed report on all the security flaws prone to cyberattacks. The data is then analyzed to prioritize issues based on their severity level. The IT security team first uses the final assessment data to remediate the critical security issues in the computing environment. This process of vulnerability scanning and prioritization of these vulnerabilities depends on the intricacy of the computing environment of enterprises.
CVSS Score:
One of the data matrices to determine the severity is the CVSS score. It has four different scales: critical, high, medium, and low. IT teams use these data and other matrices to initiate the remediation process. Most companies depend purely on the severity level of risks to mitigate or remediate them.
Asset and Business Types:
The functional value of each asset is different in a business. If vulnerabilities appear in the devices assigned to critical projects, IT teams should address such IT assets on a priority basis, irrespective of the severity level. Businesses can’t afford the risk of such an exploit as it would negatively impact their revenue.
Exploit data:
Information about the exploits in applications is stored in a database. The prioritization methods use these data in vulnerability management platform. The availability of the extensive database of security checks also decides the accuracy of the prioritization. The data explaining the ease of developing an exploit to a particular vulnerability also matters the most.
Age of vulnerability:
An old and less severe vulnerability has a higher risk of causing widespread ransomware attacks than new ones. It takes sufficient time to develop an exploit to the new ones. If the exploit is already available, it is easy to weaponize it and attack.
Importance of SanerNow Vulnerability Management
SanerNow Vulnerability Management is an integral part of the SanerNow Cyber-hygiene platform. It offers simplified vulnerability management solution, essential for today’s modern computing environment. The platform has all the important features needed to prevent threats. It helps to Scan, Assess, Prioritize, and Remediate vulnerabilities on various devices. Here are a few features of SanerNow:
Industry’s Fastest Scan
SanerNow’s intelligent scanning algorithm offers a rapid and continuous vulnerability scanning process, which runs on low network bandwidth. The fastest scans performed in less than 5 minutes is an important vulnerability management benefit.
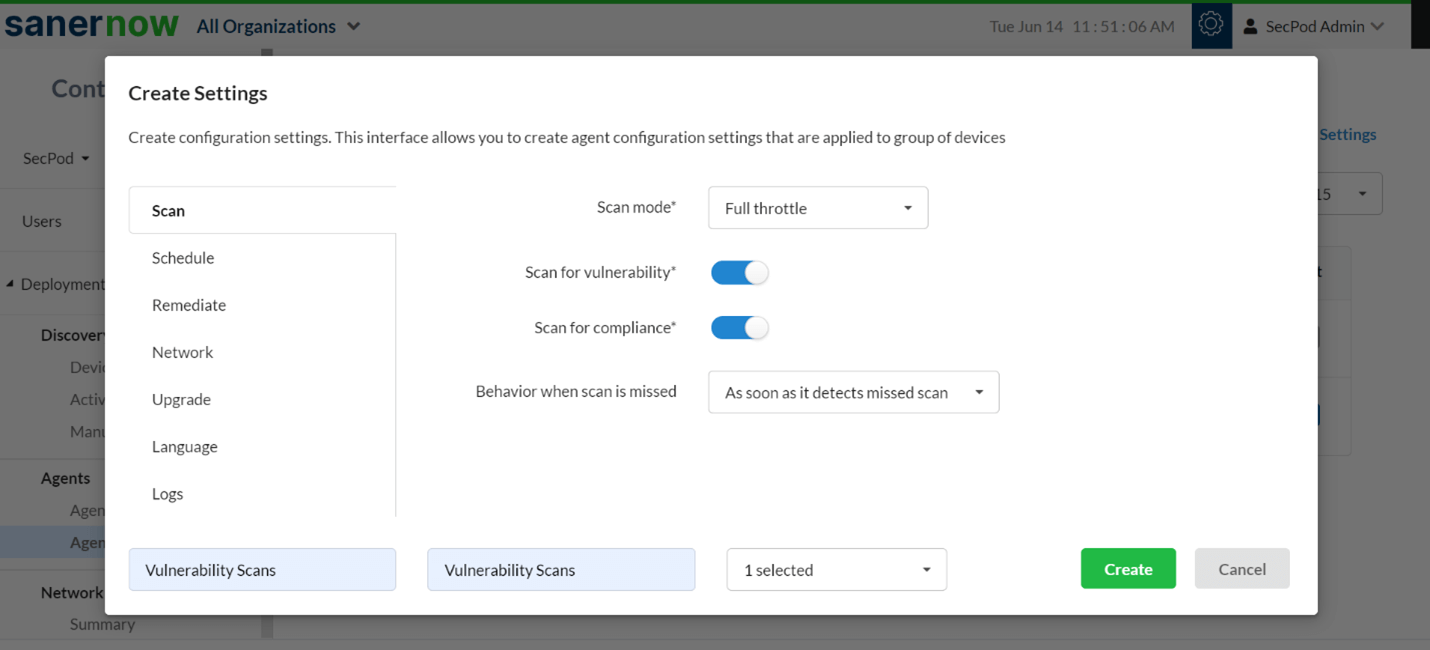
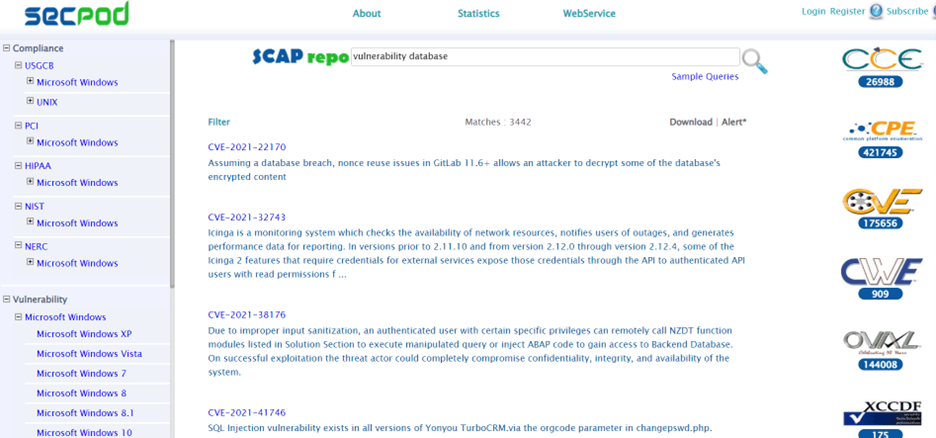
Powered by the World’s Largest Vulnerability Database
SanerNow vulnerability management software is backed by a home-grown, comprehensive vulnerability database of more than 175,000 vulnerability checks. The database is fed with new vulnerability information daily.
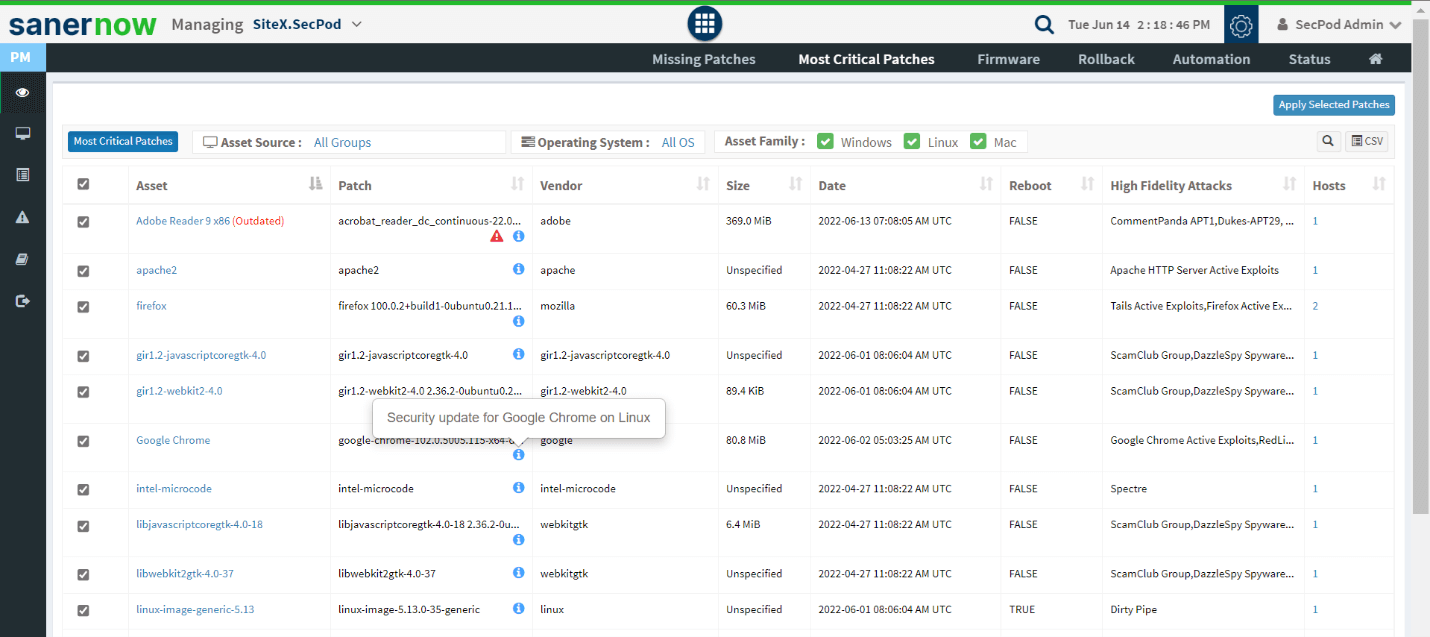
Automated Patch Remediation
SanerNow offers integrated and automated patch remediation solutions supporting all major OSs like Windows, Mac, Linux OSs, and 450+ third-party applications. Integrated patching is a crucial vulnerability management benefit that aids faster remediation.
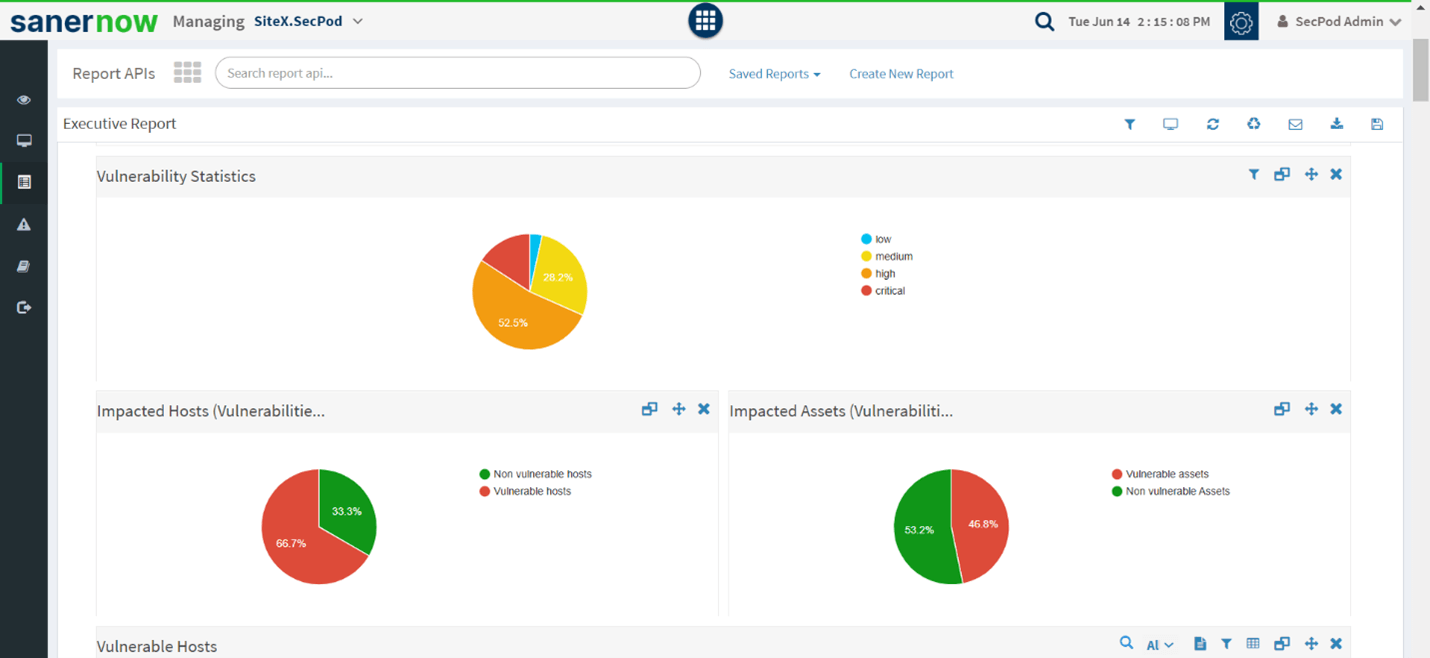
Assessment and Prioritization
IT teams can get assessment and prioritization data based on the severity level of the IT security flaws with the vulnerability management software. Generally, the process is carried out by detecting details, including historical occurrence and probability of recurrence, which reduces risk exposure.
Customizable Reports
Eliminate risks with insightful, actionable dashboards and tools with a detailed view. The tool also provides detailed end-to-end metrics regarding each vulnerability with comprehensive reports. It is complete in all aspects of securing the computing network.
Cloud-based Solutions
It enables cloud-based vulnerability management across your globally distributed organization. It can generate a comprehensive view of the vulnerabilities in the computing network. It works using the agent-sever model, which helps manage and remediate vulnerabilities in real-time. The lightweight multifunctional agents installed on all devices communicate with the cloud server to function accurately.
End-to-end Automation
SanerNow offers end-to-end automation for all the vulnerability management processes from vulnerability scanning to remediation. Security experts can automate and schedule the tasks from a single console according to the organization’s requirements.
Conclusion
Business organizations need to understand the significance of cyber security in today’s information security world, as they can’t afford the cost of a security breach.
Most importantly, understanding the feature and benefits of various vulnerability management software in the market is as important as adopting them. Adopting a tool with a good number of vulnerability management benefits will keep attackers at a distance from harming businesses and operations.


