White Papers
Securing AWS with Saner Cloud
Securing AWS with Saner Cloud Managing AWS cloud security is...
Read MoreQ2 2025 Vulnerability Report
Q2 2025 Vulnerability Report This report analyzes over 5,700 CVEs,...
Read MoreImplementing CIS CyberSecurity Framework with Saner CVEM Platform
Implementing CIS CyberSecurity Framework with Saner CVEM Platform Center for...
Read MorePrevention-First Cloud Security
Prevention First Cloud Security Detection-focused cloud security fails against advanced...
Read MoreModernize the Vulnerability Management Program of Your Bank
Modernize the Vulnerability Management Program of Your Bank A Rapid...
Read MoreSecPod ‘Entrepreneurial Company of the Year’ Award Write-up
SecPod ‘Entrepreneurial Company of the Year’ Award Write-up SecPod is...
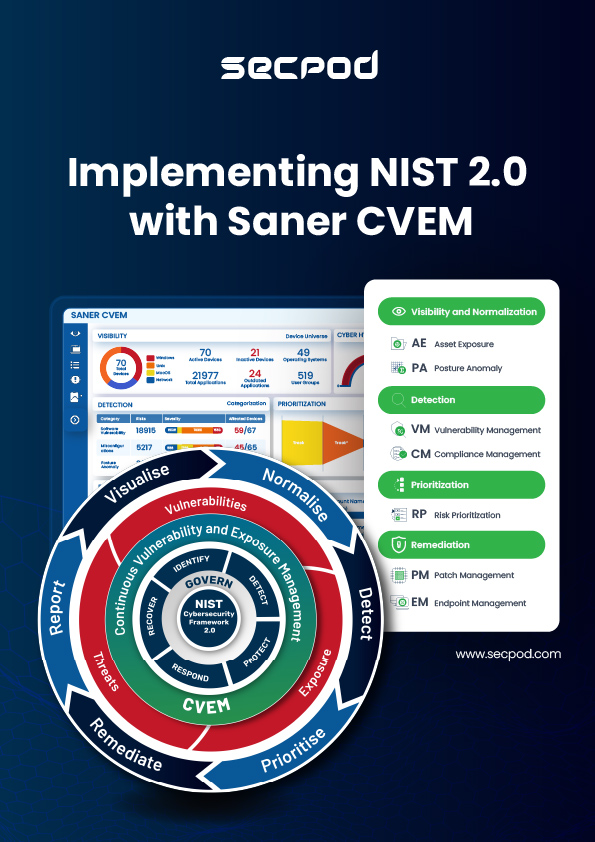
Read MoreImplementing NIST 2.0 with Saner CVEM
Implementing NIST 2.0 with Saner CVEM The National Institute of...
Read MoreCVEM: A New Dimension to Cybersecurity
CVEM: A New Dimension to Cybersecurity Is your Vulnerability or...
Read MoreThe Ultimate Guide to Building an Unstoppable IT with Unbreachable Security
The Ultimate Guide to Building an Unstoppable IT with Unbreachable...
Read MoreImplementing NIST CyberSecurity Framework with Saner CVEM Platform
Implementing NIST CyberSecurity Framework with Saner CVEM Platform The National...
Read MoreImplementing STIG using Saner CVEM
Implementing STIG using SanerNow STIG stands for “Security Technical Implementation...
Read MoreRemediate Risks Rapidly
Remediate Risks Rapidly Cyber-villains are getting smarter, and their tactics...
Read MoreA Guide to System Hardening
A Guide to System Hardening System hardening, sometimes known asconfiguration...
Read MoreAnnual Vulnerability Report – 2024
Annual Vulnerability Report – 2024 The year 2024 saw a...
Read More