August’s Patch Tuesday has arrived! This month, Microsoft has released patches for 107 flaws, including 13 critical bugs and one zero-day.
The chart below displays the types of flaws that have been patched today.
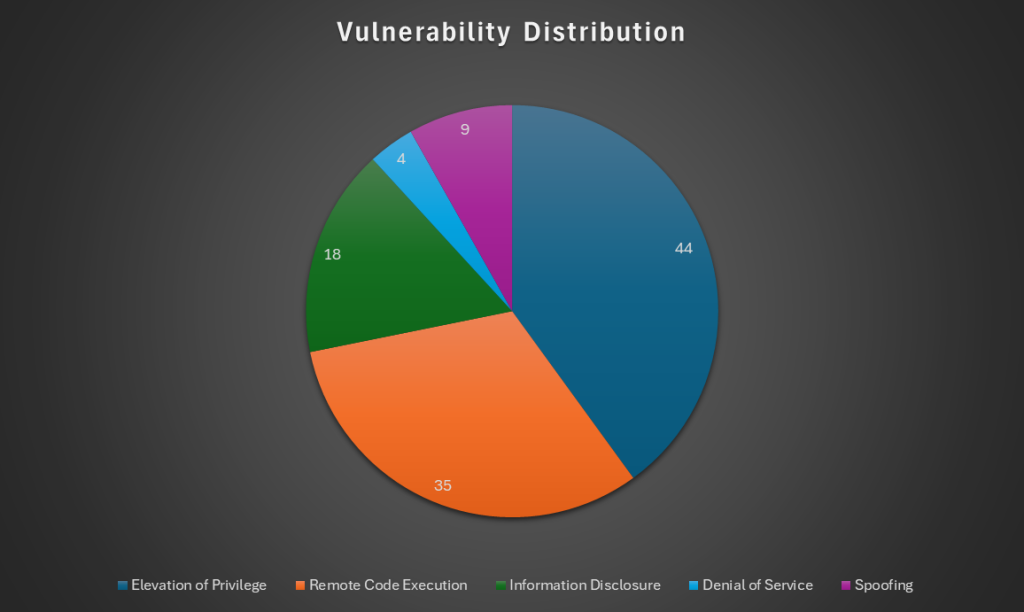
Elevation of Privilege appears to be the most common vulnerability type with 44 patched flaws, and Remote Code Execution is a close second with 35.
Vulnerability Details
CVE-2025-53779: The only zero-day to be fixed this month is a high-severity Windows Kerberos vulnerability. This flaw could let a determined insider escalate privileges to the coveted domain administrator level, posing a serious threat to enterprise networks. It stems from a relative path traversal issue that can be abused if an attacker already holds elevated permissions to specific dMSA-related attributes.
By manipulating msds-groupMSAMembership and msds-ManagedAccountPrecededByLink, an attacker could grant a managed service account the ability to impersonate high-value users, effectively taking control of the domain. Originally detailed in a technical report by Akamai’s Yuval Gordon, the exploit highlights how subtle misconfigurations in identity systems can translate into full network compromise if left unpatched.
CVE-2025-50165: A critical Windows flaw has emerged with a formidable CVSS score of 9.8, offering attackers a pre-authentication remote code execution path without requiring any user interaction. The vulnerability lies in the Windows Graphics Component, where a maliciously crafted JPEG file can trigger code execution through an untrusted pointer dereference. This attack vector could be delivered through Office documents, image files, or potentially even by luring a target to a malicious website – a dangerous combination given the SYSTEM-level execution this flaw may allow.
While it’s not confirmed to be wormable, its exploitation potential is high, echoing past image-parsing vulnerabilities like MS13-096. Notably, only Windows 11 24H2 and Windows Server 2025 are affected, suggesting it’s a relatively new bug. With the possibility of chaining this flaw into larger attack campaigns, prompt patching is essential to block what could become a powerful entry point for threat actors.
CVE-2025-53766: This flaw is a critical remote code execution vulnerability lurking in Windows’ GDI+ component, the graphics subsystem responsible for rendering most two-dimensional visuals. It stems from how GDI+ processes metafiles – vector graphic containers that, when maliciously crafted, can trigger a buffer overflow leading to code execution without any privileges or user interaction. While wormability appears unlikely, the exploitation path is disturbingly simple: an attacker could compromise a system merely by uploading a booby-trapped metafile to a vulnerable Windows host running certain web services.
This puts custom applications (such as ASP.NET sites with file upload features) at significant risk, even if Microsoft’s advisory doesn’t list platforms like SharePoint, Exchange, or Office. Fortunately, the Preview Pane can’t be abused here, but the absence of a fix for Server 2012, despite coverage for Server 2008, raises eyebrows. Given the broad and potentially unpredictable attack surface, applying the available patch without delay is critical to shutting down this vector before it becomes a favored weapon in attacker toolkits.
Affected Products and Solution
If you have any of the following products installed, update them! Microsoft’s Security Update Guide details mitigations and patches for each vulnerability. You can also use tools to help you apply said patches.
- Azure File Sync
- Azure Stack
- Azure Virtual Machines
- Desktop Windows Manager
- GitHub Copilot and Visual Studio
- Graphics Kernel
- Kernel Streaming WOW Thunk Service Driver
- Kernel Transaction Manager
- Microsoft Brokering File System
- Microsoft Dynamics 365 (on-premises)
- Microsoft Edge for Android
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Teams
- Remote Access Point-to-Point Protocol (PPP) EAP-TLS
- Remote Desktop Server
- Role: Windows Hyper-V
- SQL Server
- Storage Port Driver
- Web Deploy
- Windows Ancillary Function Driver for WinSock
- Windows Cloud Files Mini Filter Driver
- Windows Connected Devices Platform Service
- Windows DirectX
- Windows Distributed Transaction Coordinator
- Windows File Explorer
- Windows GDI+
- Windows Installer
- Windows Kerberos
- Windows Kernel
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Media
- Windows Message Queuing
- Windows NT OS Kernel
- Windows NTFS
- Windows NTLM
- Windows PrintWorkflowUserSvc
- Windows Push Notifications
- Windows Remote Desktop Services
- Windows Routing and Remote Access Service (RRAS)
- Windows Security App
- Windows SMB
- Windows StateRepository API
- Windows Subsystem for Linux
- Windows Win32K – GRFX
- Windows Win32K – ICOMP
Instantly Fix Risks with Saner Patch Management
Saner patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. Saner patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.

