Microsoft Edge and Mozilla Firefox browsers have been identified to have a severe bug that can allow remote attackers to steal the data of the users. If a user visits a malicious website, the website can steal the sensitive content of the user’s online accounts from other websites where the user have logged-in the same browser. The vulnerability dubbed as “WAVETHROUGH” has been discovered by Jake Archibald developer advocate for Google Chrome. This vulnerability resides in the way browsers handle cross-origin requests to video and audio files. This bug allows a malicious website to retrieve content from other sites by playing audio files in a malformed manner that produces unintended consequences.
Microsoft Edge and Mozilla Firefox browsers have been identified to have a severe bug that can allow remote attackers to steal the data of the users. If a user visits a malicious website, the website can steal the sensitive content of the user’s online accounts from other websites where the user have logged-in the same browser. The vulnerability dubbed as “WAVETHROUGH” has been discovered by Jake Archibald developer advocate for Google Chrome. This vulnerability resides in the way browsers handle cross-origin requests to video and audio files. This bug allows a malicious website to retrieve content from other sites by playing audio files in a malformed manner that produces unintended consequences.
WAVETHROUGH:
The vulnerability has been named as WAVETHROUGH as it involves wave audio so that data is allowed through. The attacker can use this loophole by a malicious website which uses an embedded malicious media file on its web-page, which if played, only serves partial content from its own server and asks the browser to fetch rest of the file from a different origin, forcing the browser to make a cross-origin request. This second part of the request will be successful as mixing visible and opaque data is allowed for a media file and thus allows one website to steal content from the other.
Technical Minutiae:
Modern web browsers don’t allow websites to make cross-origin requests to a different domain unless any domain explicitly allows it because of Cross-Origin Resource Sharing. Which is, if a user visits a website on his browser it can only request data from the same origin the site was loaded from and the browser cannot make any unauthorized request to steal your data from other sites.
However, same is not true for web browsers while fetching media files hosted on other origins. Media elements make use of ‘no-cors’ requests. If a user makes a no-cors request to another origin, a request is sent with cookies and a user gets back an ‘opaque’ response. If valid image data is returned, it’ll display on the site. Web Browsers thus allow a website to load audio/video files from different domains without any restrictions.
Websites use service workers API to load multimedia content from a remote site, while also using the range parameter to load just a specific section of that file. Browsers allow websites to serve partial content of a large media file via range header and partial content responses mainly for pause and resume ability for playing a large media or downloading files. Thus, web browsers via media elements have ability to join pieces of multiple responses together and treat it as a single resource.
According to researcher, Mozilla Firefox and Microsoft Edge allowed media elements to mix visible and opaque data or opaque data from multiple sources together, leaving a sophisticated attack vector open for attackers. Bugs started when browsers implemented range requests for media elements, which wasn’t covered by the standard. These range requests were genuinely useful, so all browsers did it by copying each others behavior, but no one integrated it into the standard.”
Typical Attack Scenario:
- An attacker sets up a website that makes use of an embedded malicious media file in its web-page.
- Attacker uses various tricks to make victims to visit the website and play a malicious video.
- On playing, the server provides some content to the browser and asks the browser to fetch rest of file from a different origin.
- Browser will make cross-origin request and it will be successful because mixing visible and opaque data are allowed for a media file.
- The browser will display content from the requested different origin.
- If a user is logged into any website like Gmail, Facebook etc and the malicious website requests this logged-in website, the malicious website will be able to fetch user’s private content from website.
Among modern browsers, Chrome and Safari already have a policy in place to reject such cross-origin requests and so are not affected by this vulnerability. Firefox and Edge browsers were found vulnerable to this issue. Firefox was affected by this vulnerability only in its beta and nightly versions while as Edge was affected till recently when Microsoft released the patch to address this vulnerability during June Security Updates.
Proof-of-Concept;
The researcher has published a proof-of-concept site to demostrate the vulnerability. Below figures demonstrate WAVETHROUGH where bug exposes content-length or content from another website just by playing an audio file on malicious site.
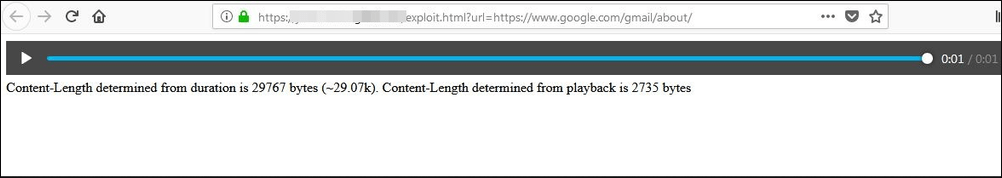
In case of Mozilla Firefox, we are able to leak the length of a resource. However, the content length may not seem a threat at first but it can be used for further attacks like timing attacks described here. Mozilla Firefox allowed the redirection and combination of the mixed responses, while exposed the duration of the audio through ‘mediaElement.duration’. The length of the cross-origin resource can be calculated from the audio length itself.
Mozilla Firefox Cross-Origin Security Bug
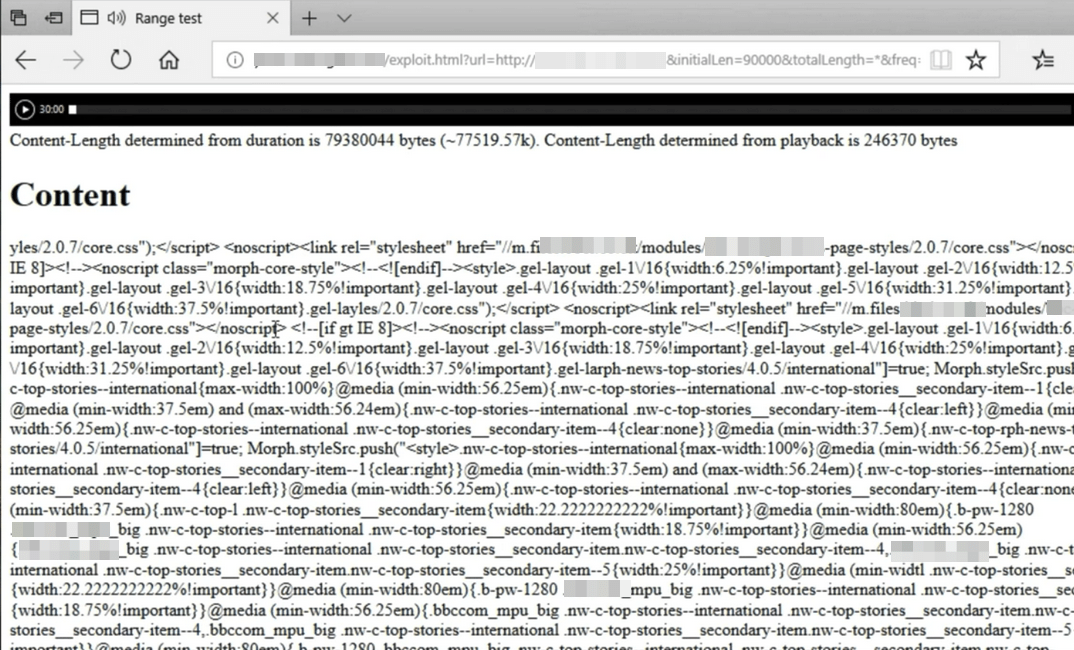
Microsoft Edge suffered the same kind of vulnerability and not only provides the content length but also the actual content as well. Below figure showing content from a genuine website just by playing a malicious audio file on malicious site.
Microsoft Edge Cross-Origin Security Bug
Impact:
Any user who visits a malicious website in the affected browser is potentially at risk of leaking his private sensitive data like email content, social networking sites feed etc.
Solution:
Firefox was affected by this vulnerability only in its beta and nightly versions. It was fixed immediately and the bug never made it to the stable release. However, patch for Microsoft Edge was released only recently in the June 2018 Patch Tuesday Updates. This vulnerability for Microsoft Edge has been assigned CVE-2018-8235.
All users are highly recommended to make sure that they are running the latest version of these browsers.
SecPod Saner detects these vulnerabilities and automatically fixes it by applying security updates. Download Saner now and keep your systems updated and secure.