Overview
Microsoft has re-released a patch for CVE-2017-8529 to fix a print issue related to this vulnerability. The patch is not fully applied unless certain registry keys are set even after installing the respective Operating System patches. This article describes the steps to update registry settings to be fully protected from CVE-2017-8529. A vulnerability management software can detect these vulnerabilities and keep your security posture secure.
Affected OS
All supported Microsoft Windows except Windows 10 1709 and Windows 10 1803 are affected by CVE-2017-8529.
Solution for CVE-2017-8529
1. Install the patches recommended in the Microsoft advisory CVE-2017-8529.
2. Create the following registry entries.
These attacks can be prevented by using a sound vulnerability management tool.
Here are the Steps to Update Your Registry Settings
By following these steps you can avoid vulnerabilities such as CVE-2017-8529 in the future.
For 32-bit and 64-bit systems:
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\ - Right-click FeatureControl, point to New, and then click Key.
- Type FEATURE_ENABLE_PRINT_INFO_DISCLOSURE_FIX, and then press Enter to name the new subkey.
- Right-click FEATURE_ENABLE_PRINT_INFO_DISCLOSURE_FIX, point to New, and then click DWORD Value.
- Type “iexplore.exe” for the new DWORD value.
- Double-click the new DWORD value named iexplore.exe and change the Value data field to 1.
- Click OK to close.

For 64-bit systems only:
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Internet Explorer\Main\FeatureControl\ - Right-click FeatureControl, point to New, and then click Key.
- Type FEATURE_ENABLE_PRINT_INFO_DISCLOSURE_FIX, and then press Enter to name the new subkey.
- Right-click FEATURE_ENABLE_PRINT_INFO_DISCLOSURE_FIX, point to New, and then click DWORD Value.
- Type “iexplore.exe” for the new DWORD value.
- Double-click the new DWORD value named iexplore.exe and change the Value data field to 1.
- Click OK to close.
CVE-2017-8529 can be prevented by updating these registry settings.
Please refer to the below image for registry changes:
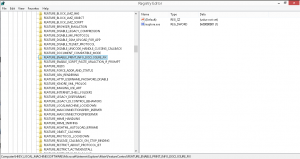
Automate Patching with SanerNow:
CVE-2017-8529 can be prevented by utilizing patch automation. Saner can automate the above patching across the organization with ease. Click here to explore patching steps using Saner.
SanerNow Personal Users:
Follow the below steps to patch the vulnerability CVE-2017-8529 fully:
1. Download the sp_cve-2017-8529_print_info_dis_reg_fix.zip zip file and unzip to get sp_cve-2017-8529_print_info_dis_reg_fix.exe
2. Open the cmd.exe as an ‘administrator’
3. Go to the path where sp_cve-2017-8529_print_info_dis_reg_fix.exe is extracted
4. Run the below command with “/S” silent option to patch this vulnerability fully.
C:\>sp_cve-2017-8529_print_info_dis_reg_fix.exe /S
By running this command CVE-2017-8529 can become less of a hassle.
These steps will resolve this vulnerability completely. SanerNow Advanced Vulnerability Management will stop reporting this vulnerability from the following manual or scheduled scan.
Have any questions on how to fix CVE-2017-8529 specific to your IT? Let’s discuss.

