Exploit kits are automated malicious software programs which target client-side application vulnerabilities like Web Browsers, Add-ons, Adobe Flash Player, Adobe Reader, Java Runtime Environment, etc. Therefore, Vulnerability Management Software can help you prevent these.
Exploit kits are easy to use and do not require in-depth technical knowledge. Hence it can be used by inexperienced hackers as well. Cybercriminals sell exploits as a service and they can be rented for a day, week, month, or year according to the need and are easily affordable. A good Vulnerability Management tool can avert this exploitation.
Working:
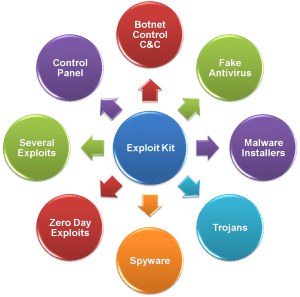
Exploit kits can create Botnet Command & Control (C&C), Fake Anti-virus, Malware installers, Trojans, and Spyware. Few exploit kits provide a nice and user-friendly web interface with a powerful control panel that attackers can configure according to their attack plan.
However, Exploit kits are very sophisticated and can bypass detection mechanisms from security products by changing evasion and obfuscation techniques.
How to exploit kits work in general:
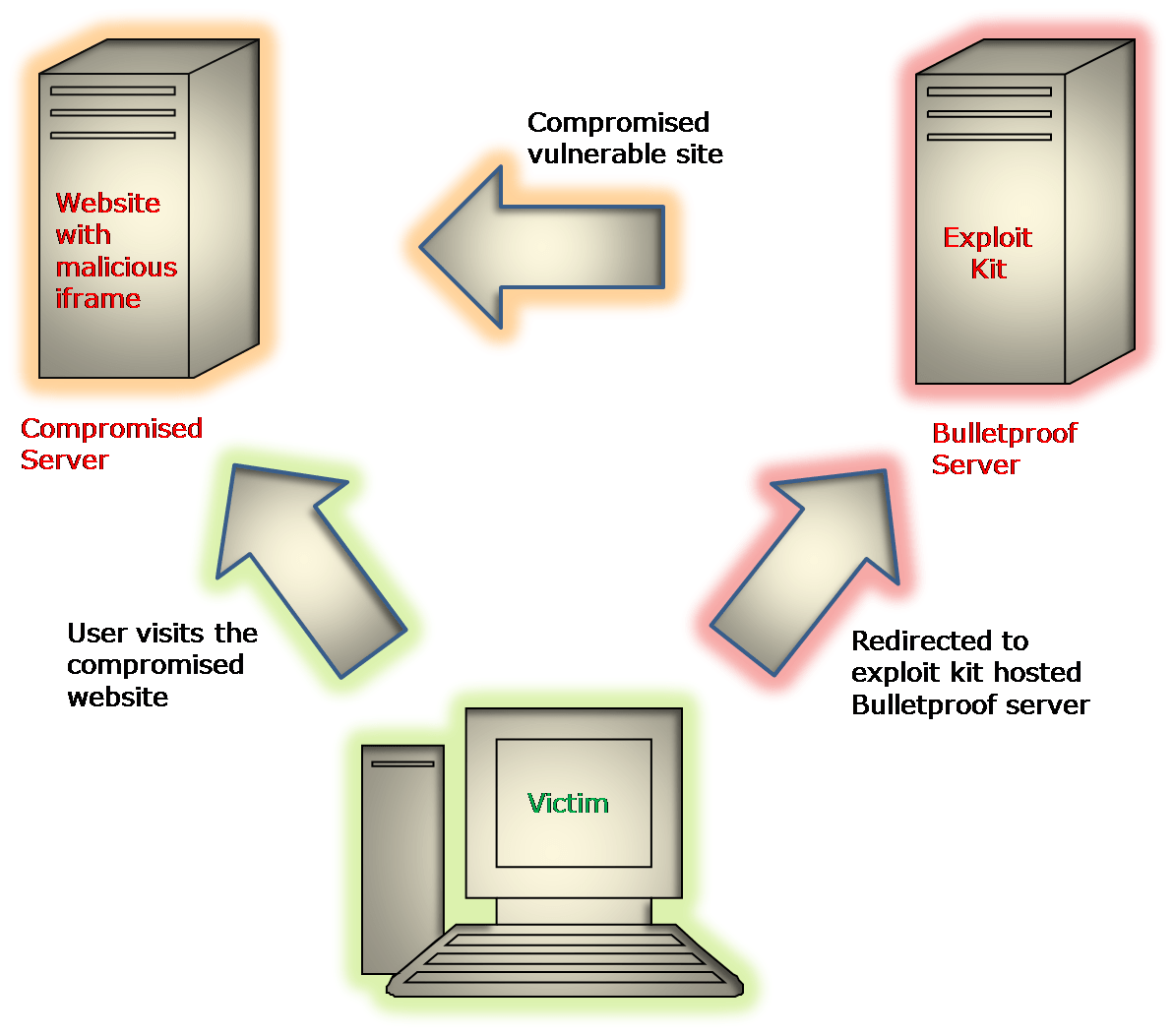
First, attackers exploit server-side vulnerabilities and add malicious hidden iframe in legitimate websites. Then, attackers convince users to visit a compromised website. Once the victim visits the site, the page gets redirected to the exploit kit hosted on the Bulletproof site. Bulletproof hosting is a service provided by domain/web hosting providers which allow their customers to upload anything, including malicious content. Exploit kits collect various information such as browser version and installed add-ons, Adobe Flash, Adobe Reader, JRE version, etc. Based on the collected information, they determine and deliver exploit/malicious code by exploiting vulnerable software. If the exploit succeeds, it can download and installs Malware, Trojans, Spywares, etc.
Cybercriminals blacklist IP addresses to keep researchers and security vendors from analyzing the exploits/attacks. If a victim visits a malicious website, the victim’s IP address is in check with the back-end database server. Moreover, It already exists in the DB; the exploit kit will respond differently. Finally, the exploit kit will allow access if the IP address does not exist in the DB. Few of the exploit kits get the blacklisted IP address as an update.
Some popular exploit kits are:
– Blackhole
– Redkit
– Neutrino
– Magnitude
– Phoenix
– CRIMEPACK
– White hole
– Cool Pack
– Crime Pack
– Neo Sploit
– Nuclear
Exploit kits mainly take advantage of vulnerable software to get into the system. However, the best way to stay safe is to install applications/add-ons only from trusted authors and keep your browsers and other applications up-to-date to avoid attacks. Never click on emails from unknown sources, and avoid suspicious websites.
Download Saner and therefore keep your systems updated and secure.
– Veerendra GG
