Oracle released the quarterly critical patch updates in April 2019. And in less than a week, a zero-day (CVE-2019-2725) was exploiting in the wild. A good vulnerability management system can prevent these attacks. However, the vulnerability exists in Oracle Weblogic Server, which has been targeted repeatedly due to its popularity and access to huge business-sensitive information.
What is the issue with CVE-2019-2725?
A remote code execution vulnerability exists in Oracle Weblogic Server. Moreover, this vulnerability identifies as CVE-2019-2725. This vulnerability was reported by KnownSec 404 Team. And, SANS ISC InfoSec Forums observed active attacks trying to install crypto coin miners. Hence, Vulnerability Management Tools can be helpful in resolving these issues.
Processing untrusted input is a major technique through which attackers find their way inside systems. The issue here is that of insecure deserialization. Moreover, the flaw exists in the wls9_async_response package. Hence, The components wls9_async and wls-wsat trigger the vulnerability. An attacker can input a serialized maliciously crafted file. Upon processing, this file deserializes and can execute the malicious content inside it with elevated privileges.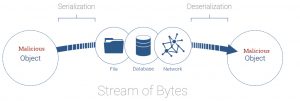
image credit: www.waratek.com
Affected Products:
The vulnerability affects these versions of the application:
- Weblogic 10.3.6.0.0
- WebLogic 12.1.3.0.0
Impact:
A remote attacker can execute arbitrary code on the target machine by inputting a specially crafted file.
Solution:
Oracle has released an out-of-band security update to deal with the vulnerability. Also, Oracle advises that the patches applied at the earliest due to the severity of the issue.

