With just a week gone by after Patch Tuesday, an anonymous researcher identified as SandboxEscaper found this to be the apt time to promulgate an exploit in Windows systems. This simple yet efficient exploit could elevate privileges on a machine to allow modification of certain restricted files which are accessible only with administrator privileges. A good Vulnerability management tool can solve these issues.
The flaw exists in the way Microsoft Windows Task Scheduler handles legacy tasks. Task Scheduler utility imports .job files with arbitrary DACL(discretionary access control list). In the absence of a DACL, complete access to the files is grant to any user. However, an attacker must have the username and password details to exploit the vulnerability. And hence, this is classified as a Local Privilege Escalation Vulnerability. A Vulnerability Management Software can prevent these attacks.
Getting our hands dirty
A proof of concept for the exploit was publishing on github. We were successful in reproducing the exploit on a Windows 10 machine, as shown below.
1) Windows 10 System installed with the latest patches from May 2019,
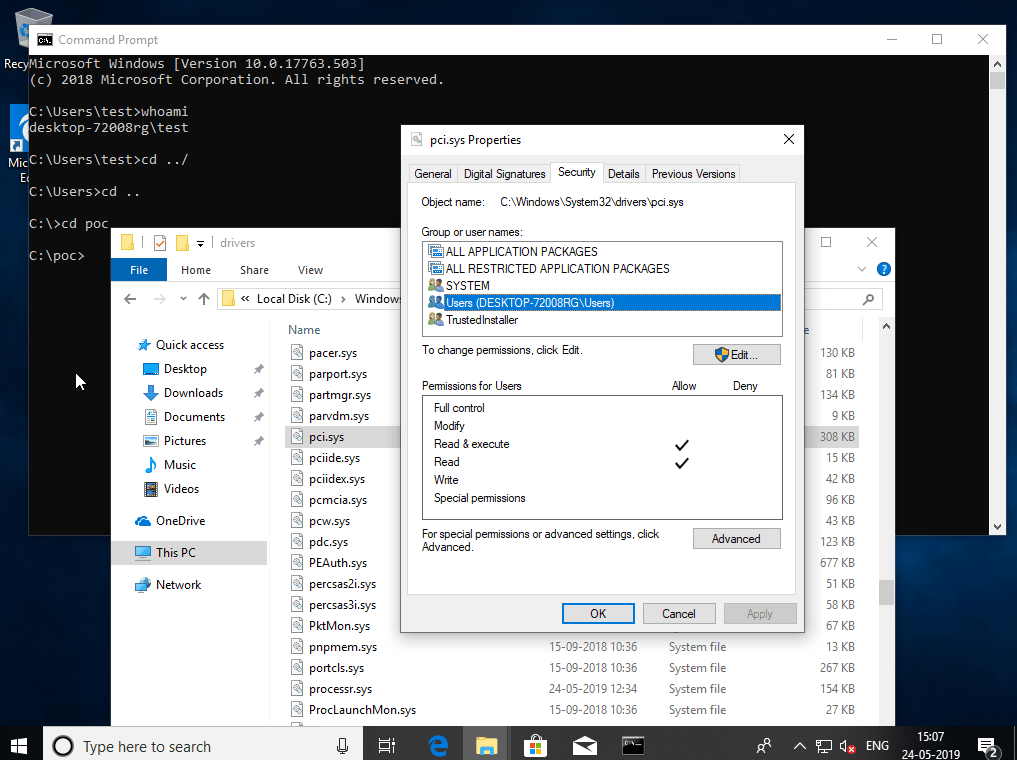
2) File pci.sys has read & execute permissions only before we run the exploit,
3) After running the exploit, file pci.sys has read, write, execute and modify permissions with full control,
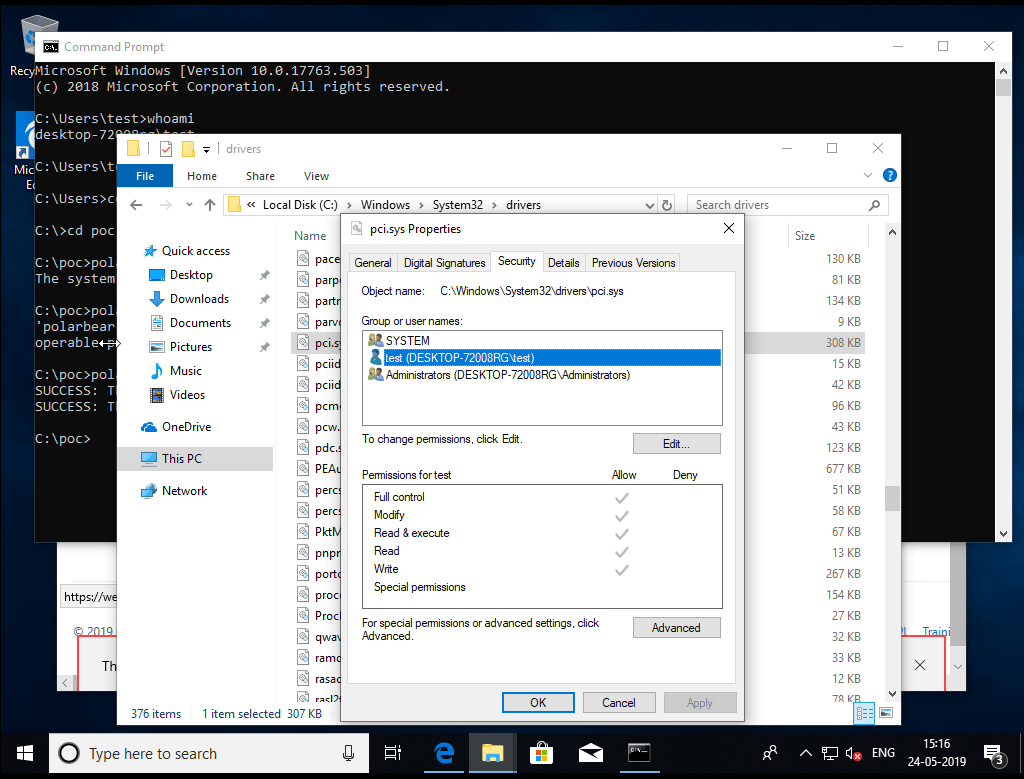
The main goal of the sandboxescaper exploit is to grant complete control over the files, which restrict any modification by a user with low privileges. A dangerous fact to note here is that even the machines installed with the latest patches have fallen prey to this vulnerability.
There are two folders present on a Windows system: c:\windows\tasks and c:\windows\system32\tasks. The former is in use to create legacy tasks imported from other systems. Windows 10 does not support task creation with .job files. But the researcher found a way out using Microsoft’s help forums. The .job files in Windows XP or older systems should initially be imported into c:\windows\tasks. Then, to create an RPC to ‘_SchRpcRegisterTask‘, a command is run using schtasks.exe and schedsvc.dll which are also copied from an old system. The function ‘_SchRpcRegisterTask’ registers a task with the server. The jobs are migrated to c:\windows\system32\tasks on modern platforms due to the presence of the legacy version of schtasks.exe.
The typical flow of the exploit involves copying the .job file to the task folder and creating a call without any modifications. Then the created file is deletion, and the native hard link is put in place and the command is rerun. This time the SetSecurityInfo function is called. At this juncture, the Task Scheduler has a SYSTEM security token. This allows it to grant full control to the files under the control of SYSTEM and other privileged accounts. The presence of SYSTEM security token, along with the hard link and the migration process of jobs, allows full permissions to be provided to the user to perform any action on a protected file.
But that’s not all; SandboxEscaper has released three more exploits for Windows systems. The anticipation for Microsoft to release a workaround or an emergency patch continues.
Affected Systems
A number of researchers tried the exploits on various Windows setups. The following systems are vulnerable:
- Windows 10 – 64 and 32 bit
- Windows Server 2016
- Windows Server 2019
Impact
Successful exploitation allows a locally authenticated user to gain full access permissions to the protected files. However, This can allow complete system compromise from a limited Windows user account.
Solution
While no workaround or remediation is currently available, we’ll continue to monitor this vulnerability and update as and when a fix is available. In the meantime, we recommend educating your teams about maintaining security hygiene.

