Artificial intelligence and computer vision fall in the category of top 10 buzzwords of modern day computing. An opensource platform helping industries build a new era of real-time visual processing is OpenCV, a library of programming functions with over 2500 optimized computer vision and machine learning algorithms.
Two< critical vulnerabilities were discovered in OpenCV libraries which allow an attacker to execute arbitrary code. The impact of the exploitation of these vulnerabilities could be huge considering the wide usage of this library in real-time processing applications such as facial recognition technology, robotics, motion tracking, etc. Vulnerability Management Software can prevent such attacks. OpenCV has been adopted by Google, Yahoo, Microsoft, Intel, IBM, Sony, Honda, Toyota, etc. OpenCV has C++, Python, Java and MATLAB interfaces and supports Windows, Linux, Android, and Mac OS.
The vulnerabilities were discovered by Dave McDaniel of Cisco Talos. CVE-2019-5063 and CVE-2019-5064 are buffer overflow vulnerabilities which can be potentially exploited to cause heap corruption and ultimately code execution. Mitigating these vulnerabilities will be easier with a patch management tool.
Delving into the details:
The flaw resides in the data structure persistence functionality of OpenCV, which can be remotely exploited using a crafted XML file(CVE-2019-5063) or a crafted JSON file (CVE-2019-5064) to corrupt the heap structure and cause code execution. These vulnerabilities have been classified as classic buffer overflow (CWE-120), where the program writes data beyond the boundaries of a buffer causing an overflow. The persistence mode functionality in OpenCV allows developers to store and restore various data structures in XML/YAML or JSON format. Arbitrarily complex data structures and primitive data types can also be stored and loaded.
CVE-2019-5063
While parsing an XML file, if an ampersand is encountered, the data till the next semicolon in the XML file is copied into a buffer using memcpy. memcpy is a function which copies data from source to the destination. Here, the size of the buffer is fixed, but, the memcpy size is calculated as the length of the entire XML entity element, where there is no check on the boundary of the buffer.
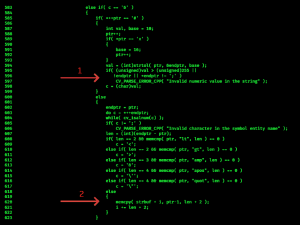 fig1. buffer overflow during the parsing routine in
fig1. buffer overflow during the parsing routine in persistence_xml.cpp
The value of memcpy size is calculated at 1(fig1) and the buffer overflow occurs at 2(fig1). Consider an arrangement where the heap object is located at 0x91c350, the buffer is located at 0x91c380 and the next object in the heap is located at 0x91d390 which is exactly 0x1040 (4160) bytes away.
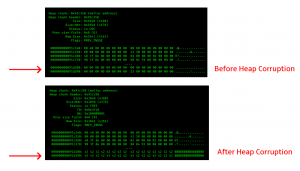 fig2. heap object corruption in 0x91d390
fig2. heap object corruption in 0x91d390
The size of memcpy exceeds the size of the buffer which leads to an overflow into subsequent heap objects and code execution. This variant of the attack can trigger an access violation as data is copied beyond the heap segment.
CVE-2019-5064
While parsing a JSON file, data is copied until a null byte is encountered. This leads to a buffer overflow as the size of the buffer is not taken into consideration while copying the data and the entire contents of the JSON value field is taken into account for calculating memcpy size.
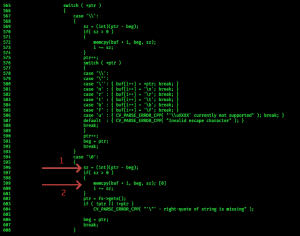
fig3. buffer overflow during the parsing routine in persistence_json.cpp
The value of memcpy size is calculated at 1(fig3) and the buffer overflow occurs at 2(fig3). Consider an arrangement where the heap object is located at 0x91c350, the buffer is located at 0x91c380 and the next object in the heap is located at 0x91d780 which is exactly 0x1400 (5120) bytes away.
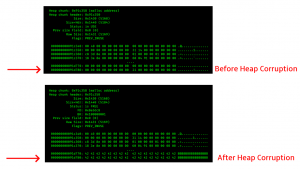
fig4. heap object corruption in 0x91d780
The size of memcpy exceeds the size of the buffer which leads to an overflow into subsequent heap objects and code execution. This variant of the attack can trigger an arbitrary free() if it is allowed to run continuously.
Affected Products
OpenCV version 4.1.0
Impact
An attacker can use a specially crafted JSON or an XML file to overflow the buffer and execute malicious code on the affected system.
Solution
OpenCV has released updates to fix the vulnerabilities. Please upgrade to version 4.2.0 at the earliest.

