Cisco has released updates for a set of vulnerabilities. These vulnerabilities include six high severity and six medium severity vulnerabilities. The main highlight for this set of Cisco updates is the patching of a recently discovered vulnerability in Wi-Fi Access points and routers, widely known as Kr00k Vulnerability.
Getting rid of the Kr00k Vulnerability
Kr00k vulnerability (CVE-2019-15126) that can be used to intercept Wi-Fi network traffic. This bug is known to affect devices operating on Broadcom or Cypress Wi-Fi chipsets and was disclosed at the RSA 2020 security conference in San Francisco by ESET researchers.
The Kr00k vulnerability lies in the implementation of the wireless egress packet processing of certain Broadcom Wi-Fi chipsets. This bug allows an unauthenticated adjacent attacker to decrypt Wi-Fi frames without any information about the Wireless Protected Access (WPA) or Wireless Protected Access 2 (WPA2) Pairwise Temporal Key (PTK) used to secure the Wi-Fi networks.
A disassociation event in an affected device triggers the deletion of a user-configured PTK as part of a sequence of cleanup operations. This also causes several Wifi frames to get lined up in the hardware egress queue. These Wi-Fi frames are encrypted with a static, weak PTK. To acquire these frames, an attacker can either trigger the disassociation event by injecting malicious packets into the wireless network and then capture the frames sent after the event; or intercept the traffic from the Wifi network and capture the frames after a disassociation event occurs. An attacker who acquires these frames can decrypt them with the static PTK thus leading to information disclosure.
The hardware egress buffer contains only the frames with weak encryption and accepts no further frames. This feature, as a blessing in disguise, limits the information that can be obtained in case of successful exploitation. Also, the attacker is restricted from controlling the content or number of frames in the buffer.
This bug is known to affect at least 14 products in Cisco’s wireless devices. Cisco is currently investigating the issue to find the other products which could be affected and will update the advisory as and when information is available.
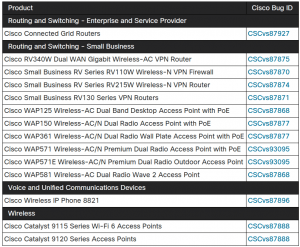 Source: Cisco Advisory for CVE-2019-15126
Source: Cisco Advisory for CVE-2019-15126
Cisco has also released security updates for the following products:
- Cisco UCS Manager Software
- Cisco Nexus 1000V Switch for VMware vSphere
- Cisco MDS 9000 Series Multilayer Switches
- Cisco FXOS Software
- Cisco NX-OS Software
High Severity Vulnerabilities
- CVE-2020-3173 – A command injection vulnerability in local management CLI of Cisco UCS Manager Software could allow an authenticated, local attacker to execute arbitrary commands on the underlying operating system.
- CVE-2020-3168 – A denial of service vulnerability in the Secure Login Enhancements capability of Cisco Nexus 1000V Switch for VMware vSphere could allow an unauthenticated, remote attacker to cause an affected Nexus 1000V Virtual Supervisor Module (VSM) to become inaccessible to users through the CLI.
- CVE-2020-3175 – A denial of service vulnerability in the resource handling system of Cisco NX-OS Software for Cisco MDS 9000 Series Multilayer Switches could allow an unauthenticated, remote attacker to cause unexpected behaviors such as high CPU usage, process crashes, or even full system reboots of an affected device.
- CVE-2020-3167 – A command injection vulnerability in the CLI of Cisco FXOS Software and Cisco UCS Manager Software could allow an authenticated, local attacker to execute arbitrary commands on the underlying operating system.
- CVE-2020-3171 – A command injection vulnerability in the local management CLI of Cisco FXOS Software and Cisco UCS Manager Software could allow an authenticated, local attacker to execute arbitrary commands on the underlying operating system.
- CVE-2020-3172 – An arbitrary code execution and denial of service vulnerability in the Cisco Discovery Protocol feature of Cisco FXOS Software and Cisco NX-OS Software could allow an unauthenticated, adjacent attacker to execute arbitrary code as root or cause a denial of service (DoS) condition on an affected device.
Medium Severity Vulnerabilities
Cisco addressed five medium severity vulnerabilities in Cisco NX-OS and FXOS Softwares:
- CVE-2020-3165 – An authentication bypass vulnerability in the implementation of Border Gateway Protocol (BGP) Message Digest 5 (MD5) authentication in Cisco NX-OS Software could allow an unauthenticated, remote attacker to bypass MD5 authentication and establish a BGP connection with the device.
- CVE-2020-3174 – An invalid ARP vulnerability in the anycast gateway feature of Cisco NX-OS Software could allow an unauthenticated, adjacent attacker to populate the ARP table with incorrect entries, which could lead to traffic disruptions.
- CVE-2020-3170 – A denial of service vulnerability in the NX-API feature of Cisco NX-OS Software could allow an unauthenticated, remote attacker to cause an NX-API system process to unexpectedly restart.
- CVE-2020-3166 – A vulnerability in the CLI of Cisco FXOS Software could allow an authenticated, local attacker to read or write arbitrary files on the underlying operating system.
- CVE-2020-3169 – A command injection vulnerability in the CLI of Cisco FXOS Software could allow an authenticated, local attacker to execute arbitrary commands on the underlying Linux operating system with root privileges.
Impact
Attackers can abuse these vulnerabilities to execute arbitrary code and commands, bypass authentication, disclose sensitive information, read and write arbitrary files, populate ARP tables with incorrect entries and also cause a denial of service.
Solution
We recommend installing the necessary Cisco security updates at the earliest to stay protected.

