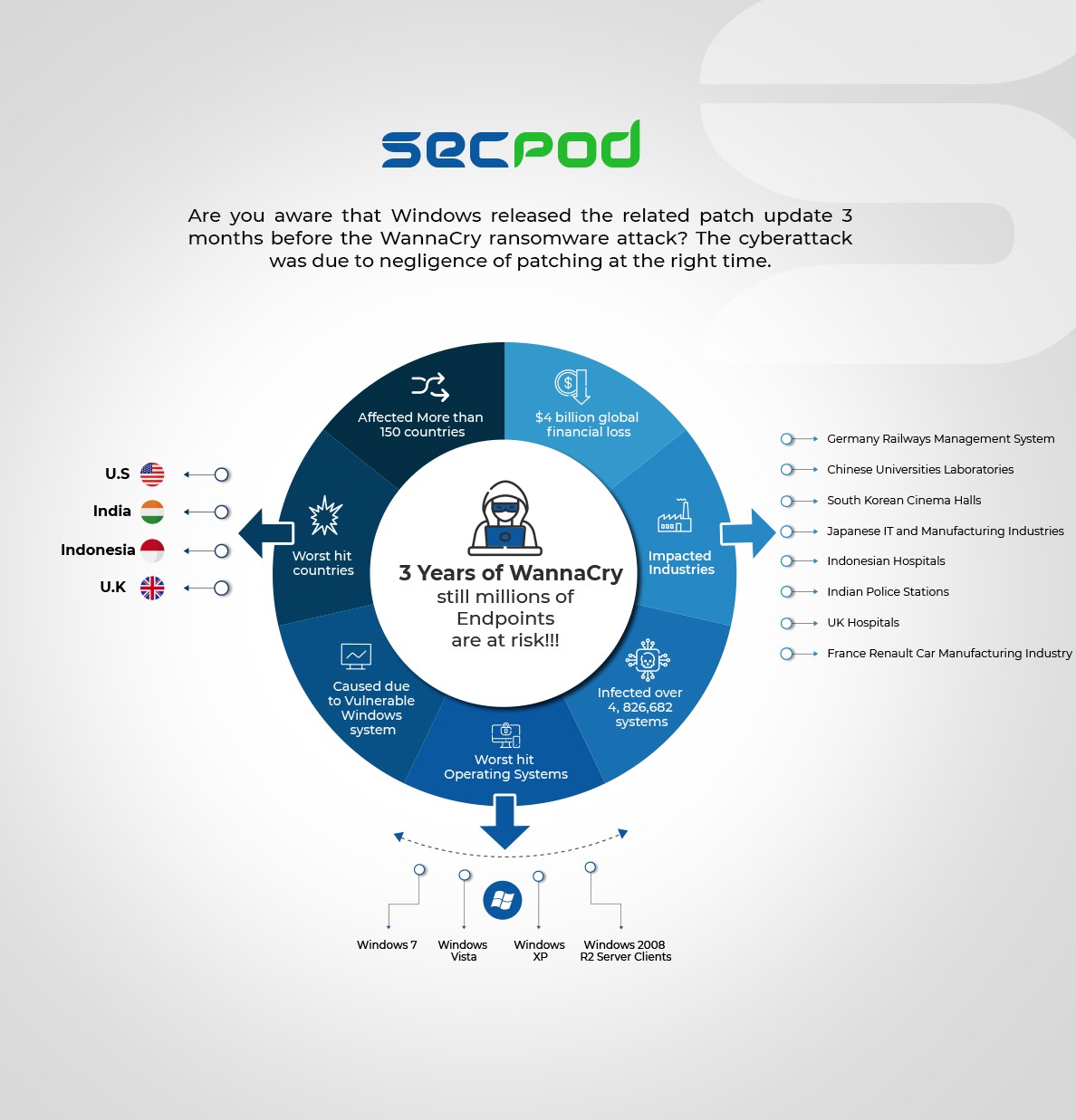
Are you aware of the worst cyberattack of 2017, the WannaCry ransomware attack? WannaCry was one of the worst-hit ransomware attacks that surfaced around May 2017 in Asia. The malware spread like wildfire and infected more than 230,000 computers in a day. The WannaCry attack mainly affected the Windows Operating System, and more than $4 billion in losses were reported. It’s still considered one of the most threatening ransomware attacks that ever occurred. Therefore, a Vulnerability Management Tool can prevent these attacks.
The ransomware attack was immediately regarded as a worldwide digital epidemic. In Microsoft Windows OS, files of users were held hostage and the hackers demanded ransom in Bitcoin. A good Vulnerability Management Tool can resolve these issues.
What is WannaCry Ransomware?
WannaCry is a class of malware that comprises several components. It had the power of self-propagating, as it falls under the worm category. The malware makes its way into a computer that is already infected as a dropper and then starts to extract application components that are already running in the system. The application components here are:
- Tor, open-source software used for encrypted communication
- Files featuring several encryption keys
- An application that ensures encryption and decryption of data
The scariest part is, it does not need any interaction with the victim to keep itself from spreading. Irrespective of all the devastation that WannaCry inflicted on over 200,000 PCs, security analysts were able to analyze the ransomware.
What made WannaCry Ransomware a success in Infecting PCs?
WannaCry infected only the Windows operating system. It all started when an exploit kit developed by the National Security Agency (NSA, USA) to infect computers having Eternal Blue exploit, leaked and fell in the hands of wrong people called “Shadow Brokers.” Shadow Brokers made the attack completely public which further resulted in creating chaos among the masses.
Prior to the attack, Microsoft already discovered the vulnerability a month ago and the tech giant immediately released a patch. However, there were several systems where patching didn’t occur due to human negligence and it gave rise to this global endemic. Microsoft, in the brink of this outbreak, criticized the U.S. government for not sharing the details regarding this vulnerability earlier.
Eternal Blue exploit, also known as the infamous CVE-2017-0144, discusses remote code execution in Microsoft Server Message Block (SMB) 1.0. Microsoft SMB is a protocol for network file sharing. Successful exploitation of this vulnerability enables attackers to target the server with unauthorized code execution by sending crafted packets to the SMB server.
How does WannaCry work?
Let’s say you have a PC that the ransomware, WannaCry was able to breach. Here, WannaCry ransomware will not simply start to encrypt the files just like that. Rather, the ransomware has to gain access to a massive gibberish URL before inflicting damage. Upon gaining access to the domain, WannaCry will simply shut down itself. The entirety of functionality is unexplainable even at the time of writing. Researchers believe that this step ensures pulling up the plug off the attack.
Did Microsoft release WannaCry Patch soon after the attack?
Preventing WannaCry ransomware was not difficult as Microsoft did come up with a patch prior to the attack that took the computers with Windows OS globally by storm. By the looks of it, the tech giant released Microsoft Security Bulletin MS17-010 on the 14th of March 2017. Further, Microsoft also updated the implementation to prevent any chance of infection from the bug. Given that the manufacturer did flag that the ransomware was a critical vulnerability, there were several systems across the world which didn’t update to the patch. Hence, the spread of the ransomware was seamless.
After the hackers took control of the unpatched systems, going back to restoring wasn’t an option. Since the attack people have begun to back up their important files and regularly update their Windows OS. Windows 10 onwards, Microsoft has introduced an automatic update option that covers the basic need of installing updates to fend off from cyberattacks.
What made WannaCry the Worst Event?
As the WannaCry ransomware spread widely, it infected several vulnerable endpoints running mostly outdated Windows 7, Windows XP, and several unpatched Windows 10 Operating Systems. This ransomware impacted various healthcare (like the U.K-based National Health Services) and motor industries. Some of the worst impacts include the erasure of several patients’ data and the cancellation of many vital surgery appointments. Similarly, in Japan, Honda had to temporarily close one of their plants as their important production files were completely out of their reach. Many such examples show how the ransomware attack has affected every industry and acted as an industry-threatening event.
With a vulnerability in the Windows operating system left to be tended, the attackers exploited the said vulnerability. Several security researchers from across the globe like Symantec and NSA linked the cyberattack to Lazarus Group, an infamous crime syndicate that has ties with the government of North Korea.
How a Ransomware like WannaCry Victimizes Organizations
The victim has to pay a ransom to unlock their important files and folders. In most cases, WannaCry demanded $300 to unlock the files. The ransom value doubles after seven days. In case the end-users do not pay the ransom, the attackers remove the files permanently.
Victims must use Bitcoins to pay for the ransom, as cryptocurrency transactions are hard to trace. WannaCry ransomware amounted to more than $4 billion. Some of the statistics suggest the huge financial losses that came after the global epidemic due to WannaCry are still under speculation.
WannaCry: Scenario so far
Why are Endpoints Affected even when a Patch is Available?
- Most of the organizations do not consider patching seriously and miss performing them on a daily basis. This negligence exposes their endpoints to some serious vulnerabilities.
- In some cases, organizations do not have an effective tool in place to detect and remediate vulnerabilities.
Are Your Endpoints Safe from Potential Future Attacks like WannaCry?
There is always a possibility of a ransomware attack like WannaCry. If you are unaware of your cyber hygiene status, then there is a high chance that you become a victim of such attacks. Surprisingly, there are many organizations out there that are still using outdated software and operating systems. Even today, millions of devices have unattended vulnerabilities, which will invite more attacks like WannaCry in the future. Organizations must take preventive measures to secure their endpoints from attacks like this.
How Can SanerNow Help You Stay Ahead of Attacks Like WannaCry?
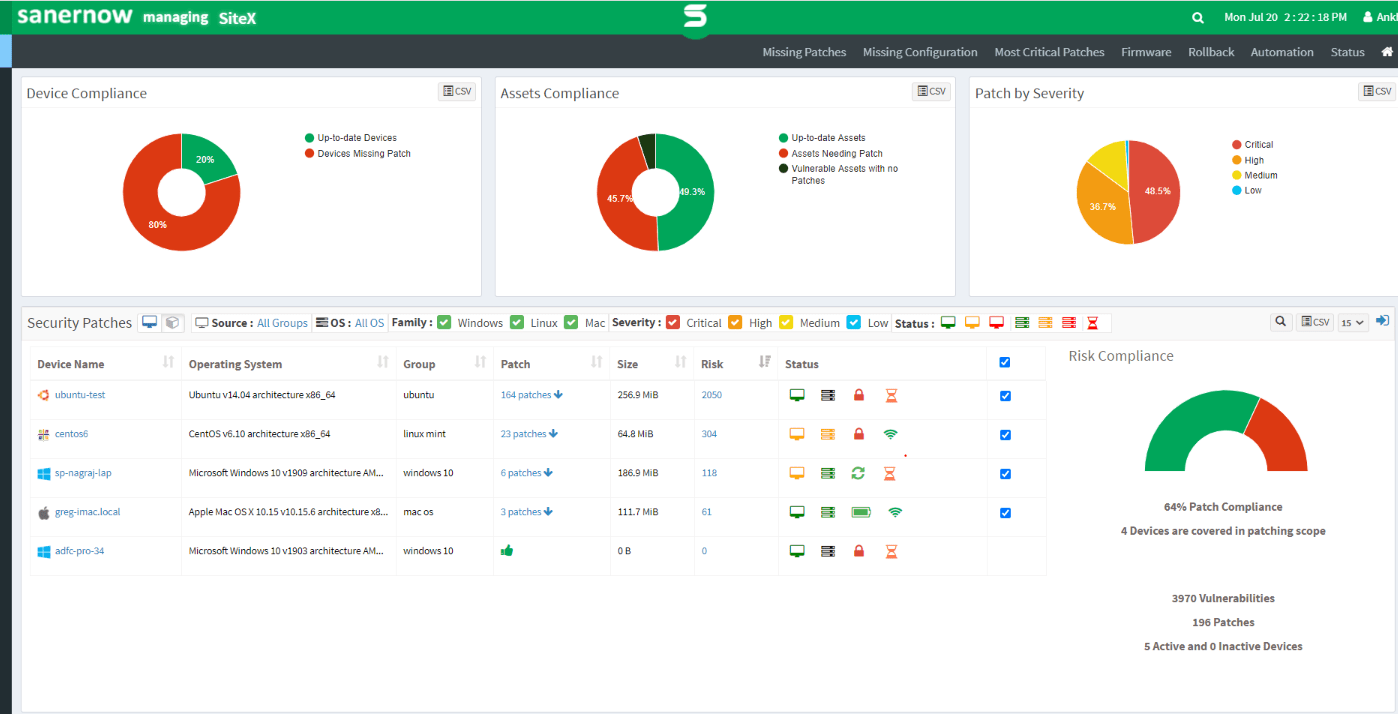
SanerNow comes with all the required features to manage and secure your endpoints under one roof. SanerNow’s vulnerability management and patching technique allows you to detect any vulnerabilities and instantly remediate them. With SanerNow, you can stay on top of your vulnerabilities by running continuous vulnerability scans, accurate vulnerability detection, intact prioritization based on severity, and remediation through integrated patching. This way, SanerNow continuously monitors your endpoints and secures your network from attacks like WannaCry.
SanerNow Patch Management
Check out this SanerNow’s eBook on “Best Practices of Orchestrating Cyber Hygiene” and keep your endpoints in check.
Take a Free Trial of SecPod SanerNow and stay ahead of the next cyberattack like WannaCry.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.