The year is almost coming to an end. We’ve been practicing personal best cyber hygiene practices at home, offices, and everywhere else to protect our loved ones. While we’ve been confined to our homes, crossing our fingers, and hoping the pandemic comes to an end, the dark underbelly of cyberspace has quietly grown its reaches far wide.
The United Nations has reported a 600% increase in cyber-crime since the onset of the COVID-19 pandemic. Cybercriminals are using the opportunity to meet their objectives way faster and easier than before.
Organizations are experiencing increased cyber-attacks and data breaches in 2020. Obviously, even though healthcare is the targeted industry. There is a breach in businesses in almost all industries are actively breached and are held for ransom. To prevent such breaches, utilizing a vulnerability management software will be crucial.
This cybersecurity awareness month, we at SecPod want to make sure every hardworking organization takes an effort to protect what it creates.
Cyberhygiene best practices are a set of security practices you carry out as a routine to keep your endpoints safe from vulnerabilities and threats. Put cyber hygiene on the front seat and secure your endpoints before it’s too late with the top 10 cyber hygiene best practices as shown.
10 best practices to orchestrate cyber hygiene
We recommend you follow these best practices to secure and manage your endpoints effectively.
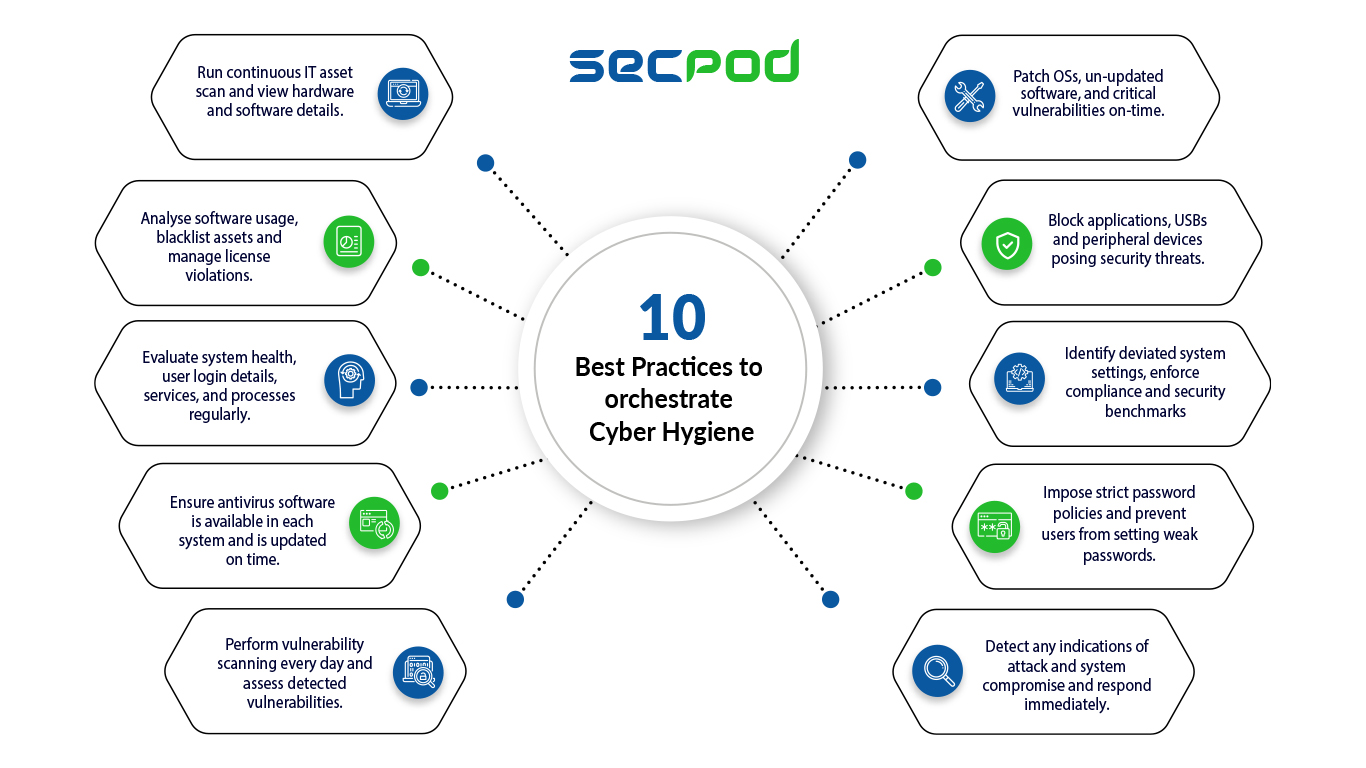
- Run continuous IT asset scans and monitor hardware and software
- Perform vulnerability scans every day, assess detected vulnerabilities, and remediate them
- Patch OSs, un-updated software, and critical vulnerabilities on time
- Ensure you install antivirus software and update regularly in all endpoints
- Impose strict password policies and prevent users from setting weak passwords
- Identify deviated system settings and harden endpoints to meet security compliance standards
- Evaluate system health, user login credentials, services, and processes regularly
- Analyze software usage, blacklist rogue assets, and manage license violations
- Block rogue applications and unwanted USB devices that pose security threats
- Detect and respond to indications of attacks and compromise immediately
To learn more in detail about these best practices, read our free eBook on “Cyber hygiene Best Practices for Orchestrating, Prioritizing the Cyber Hygiene”.
In a world where personal hygiene is helping us fight this pandemic, let’s start practicing cyberhygiene to secure our digital world.
Let’s get through this together.


