Oracle has addressed a critical Remote Code Execution (RCE) vulnerability in the rare out-of-band patch in numerous versions of Oracle WebLogic Server. The vulnerability is assigned CVE-2020-14750, which has a CVSS base score of 9.8 out of 10 and is remotely exploitable without authentication or user interaction. A good Vulnerability management tool can solve these issues. According to Eric Maurice, director of security assurance at Oracle, in a Sunday advisory.
Due to the severity of this vulnerability, Oracle strongly recommends that customers apply the updates provided by this Security Alert as soon as possible after applying the October 2020 Critical Patch Update. A Vulnerability Management Software can prevent these attacks.
CVE-2020-14750 Details :
Specific details of the vulnerability were not disclosed; Oracle’s alert mentions that the flaw exists in the console component of the Oracle WebLogic Server and can be easily exploited via HTTP protocol. Oracle said this vulnerability is related to CVE-2020-14882, a similar remote code execution flaw in the oracle weblogic vulnerability console component and can be exploited via a single crafted HTTP request.
As per the Oracle Security Alert Advisory,
It is remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password.
This critical vulnerability is “low” complexity by Oracle. Due to the “low” complexity of the exploit, attackers require no user interaction and no privileges to exploit the vulnerability. The vulnerability tracking as CVE-2020-14750 was addressing in Sunday’s Oracle Advisory; Moreover researchers believe it to be a patch bypass for CVE-2020-14882 CVEs fix.
There is already a patch bypass for CVE-2020-14882 sharing on the internet.
Patch Details
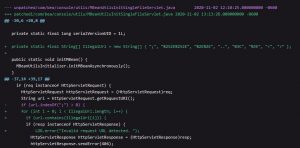
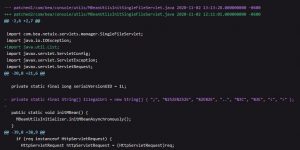
The original patch adds an IllegalUrl blocklist that is easily bypassing by simply changing the case of the input string or using various forms of double encoding. As per Rapid7 researchers below are the details of the code which has gone through variation.
In the latest patch, however the developer replaced the blocklist with allowlist, which appears to be a good approach.
We urge users of Oracle WebLogic Server to update their server’s at the earliest.
Affected Oracle WebLogic Versions :
- 10.3.6.0.0
- 12.1.3.0.0
- 12.2.1.3.0
- 12.2.1.4.0
- 14.1.1.0.0
Impact :
This issue allows attackers to execute arbitrary code on the affected system.
Solution :
SanerNow security content is finally publishing to detect this vulnerability. Oracle has already released a security update this month and these patches are available only for Oracle customers. Please be in advisement to download the patch from the Oracle portal and install it. Therefore, SanerNow software deployment capability can be of use to install executables/scripts.