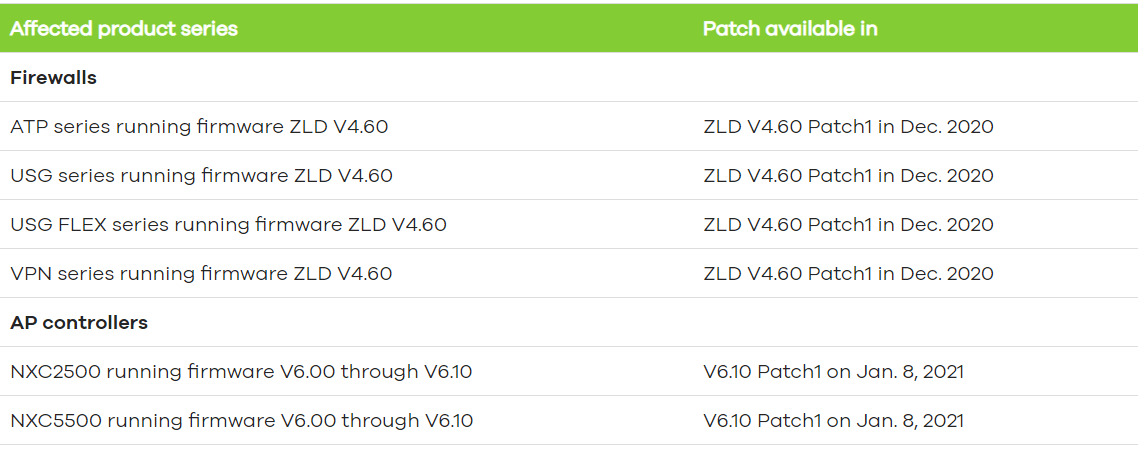
Niels Teusink of Dutch cybersecurity firm EYE has recently discovered a secret backdoor to Zyxel devices. More than 100,000 Zyxel Firewall and AP Controllers of version 4.60 patch 0 are affected by this vulnerability (CVE-2020-29583). A vulnerability management solution can be helpful here. It is due to a hardcoded administrative account.
Vulnerabilities Details (CVE-2020-29583)
A hardcoded credential vulnerability was in some Zyxel devices in the “zyfwp” user account. The account has the login name “zyfwp” with administrative privileges and a static plain-text password. The user account was created to address automatic firmware updates to connected access points through FTP. The vulnerability could allow remote attackers to have administrative access. This allows attackers to use the “zyfwp” user account to log in remotely and take over the Zyxel device. As a result, it could also allow attackers to intercept traffic, firewall settings, create VPN accounts to gain access to the network behind the device, and perform other administrative functions. To avoid such attacks, we can use a patch management solution and patch the vulnerabilities.
$ ssh [email protected] Password: Pr*******Xp Router> show users current No: 1 Name: zyfwp Type: admin (...) Router>
Teusink reported: “As SSL VPN on these devices operates on the same port as the web interface, a lot of users have exposed port 443 of these devices to the internet. Using publicly available data from Project Sonar, I was able to identify about 3.000 Zyxel USG/ATP/VPN devices in the Netherlands. Globally, more than 100000 devices have exposed their web interface to the internet.”
Attackers are actively scanning for the Zyxel backdoor. Recently cybersecurity GreyNoise detected that hackers are trying to exploit this backdoor, three different IP addresses actively scanning for SSH devices and trying to login using the Zyxel backdoor credentials. When it detects SSH, the attacker will try to brute force using Zyxel ‘zyfwp’ backdoor account.
Impact
The vulnerability could allow remote attackers to have administrative access. This allows attackers to use the “zyfwp” user account to log in remotely and take over the Zyxel device.
Affected Applications and Solutions