A new zero-day vulnerability (CVE-2014-1776) in Internet Explorer is being used in targeted attacks, which was discovered by the security firm FireEye. Therefore, a good vulnerability management tool can prevent these attacks.
A memory corruption vulnerability exists in Internet Explorer that can be used to execute arbitrary code and according to the FireEye blog, this zero-day exploit can bypass both ASLR and DEP. Hence, Vulnerability Management System can resolve these issues.
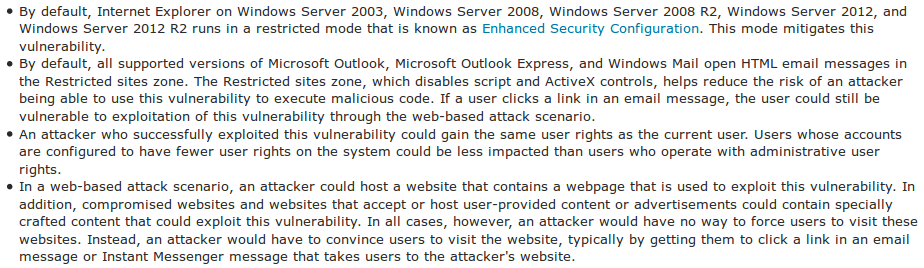
The flaw allows attackers to take complete control of the system remotely in the context of the current user within Internet Explorer.
An attack is conducted by convincing users to visit specially crafted website hosted by an attacker.
This vulnerability (CVE-2014-1776) affects Internet Explorer 6 – Internet Explorer 11.
According to Microsoft Security Advisory 2963983, limited targeted attacks are taking place that attempt to exploit this vulnerability (CVE-2014-1776). Currently Microsoft is working on an official security patch and may include security update in the upcoming Patch Tuesday or an out-of-cycle security update depending on customer needs.
Mitigating Factors:
Until Microsoft releases a security patch, follow the below workaround to block known attack vectors,
– Deploy the Enhanced Mitigation Experience Toolkit 4.1
– Set Internet and Local intranet security zone settings to “High” to block ActiveX Controls and Active Scripting in these zones.
– Configure Internet Explorer to prompt before running Active Scripting or to disable Active Scripting in the Internet and Local intranet security zone.
– Unregister VGX.DLL
– Modify the Access Control List on VGX.DLL to be more restrictive.
– Enable Enhanced Protected Mode For Internet Explorer 11 and Enable 64-bit Processes for Enhanced Protected Mode.
Complete information on workarounds found in Microsoft Advisory 2963983 “Suggested Actions” section.
SecPod Saner will have the facility to fix this vulnerability soon after the patch is releasing by Microsoft.
Veerendra GG



Thanks for the marvelous posting! I genuinely enjoyed reading it, you’re a great author.I will make certain to bookmark your
blog and will often come back in the future. I want to encourage you to ultimately continue your great job,
have a nice afternoon!