Since the inception of the Internet, cyberattacks have been a major concern globally. Due to the global pandemic, there is an 81% increase in cyberattacks. Further, making the year 2021 incur record-breaking cyberattacks. Attacks on businesses and organizations increased to 29% in the US alone.
When businesses transitioned to the Work-From-Home and Hybrid working model, cybercriminals also had to move their overall mode of operations. All the more reason why in 2021, cyberattacks made their way to networks and supply chains to disrupt the functionality of organizations. As the technology keeps on getting sophisticated, hacking groups also began to step up in their game by leveraging technology to carry out large-scale attacks.
Cyberattacks 2021 are Devastating in Numbers!
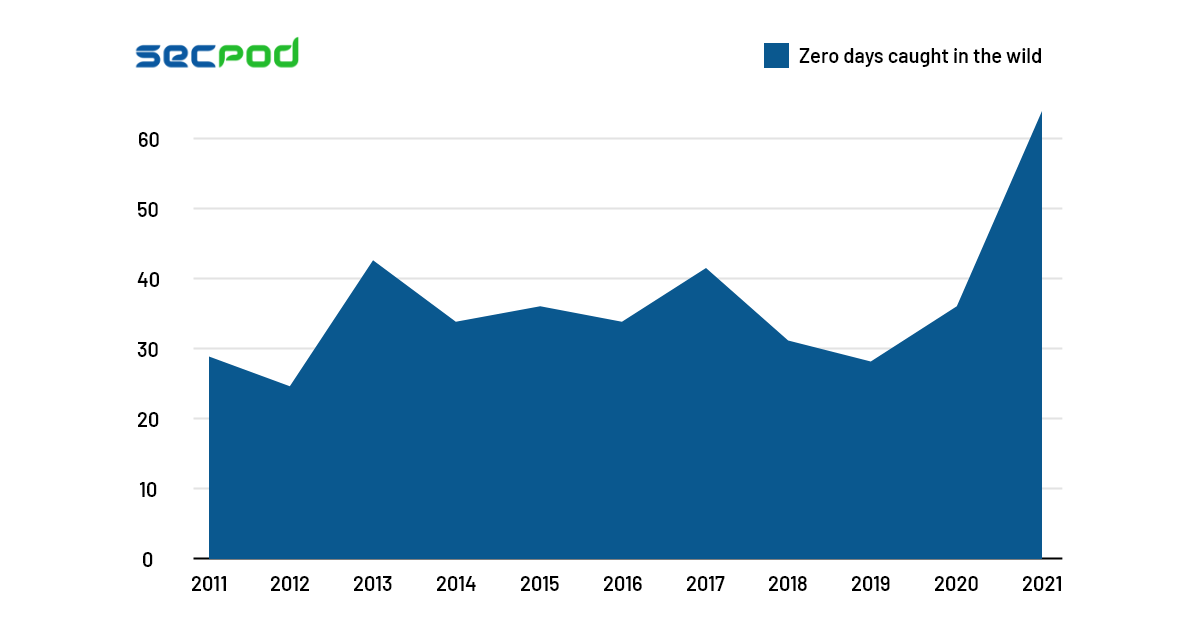
Over the years, zero-day vulnerabilities have become a significant concern for security admins. Experts noted 66 zero-day vulnerabilities among numerous notorious cyberattacks in 2021 alone. The record-breaking data does grab the attention of security admins in cyberspace. However, what does the finding indicate? Does it mean there are numerous zero-days used significantly by bad actors now? Or does it signify that defenders are doing an excellent job keeping the attacks at bay?
For instance, with RaaS or ransomware-as-a-Service becoming a conventional norm, security admins desperately need new techniques/tech to counter the challenges of cyberattacks.
Whatever you might conjecture from the above data, a massive increase in attacks is visible. With hacking tools becoming more sophisticated and accessible, hackers are reaping the rewards by conducting these criminal activities. Governments are employing hacker groups to breach and steal trade secrets. Without digressing further, let’s look at the top cyberattacks of 2021 and why these attacks took place?
Kaseya
The large-scale ransomware attack on Kaseya by REvil, aka Sodinokibi, is currently the greatest cyber-attack of all time. As one of the notable cyberattacks 2021, the ransomware affected 800-1,500 businesses that leverage Kaseya’s VSA, a SaaS-based IT management & remote monitoring solution.
A Ukrainian-based hacker, Yaroslav Vasinskyi, distributed ransomware in the Vector Signal Analysis on July 2, 2021, exploiting numerous vulnerabilities in the tool. Further, this gave the attacker the prowess to infect different businesses, causing a supply chain attack. Upon investigation, it was unveiled that 1 million endpoints were jeopardized in the massive cyberattack of 2021. Alongside Vasinskyi, the Dept. of Justice, USA, seized $6.1 million that was tracked to another Russian national Yevgeniy Polyanin.
It took Kaseya 9 days, i.e., June 11, 2021, to bring about a patch to address and remediate vulnerabilities for all its VSA customers.
FireEye
FireEye has been a synonym to the epitome of cyber security for years now. The Silicon Valley company usually receives the first call from government agencies and top-notch companies worldwide due to their prowess to tackle cyber attacks in 2021. FireEye fears that some of the most talented attackers have rendered them vulnerable in an unexpected turn of events. A ‘country backed up by top-notch cyberattack capabilities initiated a state-sponsored attack was brought down to FireEye.’
Attackers targeted and accessed some of the Red Team assessment tools. Generally, FireEye uses these tools to test the security of its customers. The assessment tools can mimic the functioning of several cyberattacks and further initiate diagnosis for their customers. The only silver lining in this scenario is that none of the tools features zero-day exploits.
Even at the time of writing, experts at FireEye aren’t sure about the attackers’ intentions. Since the cyberattacks of 2021 are devastating, FireEye has curated over 300 countermeasures to protect its customers and community.
SolarWinds
The hackers launched a supply chain attack by targeting the organization’s systems. They skipped on hacking the networks by focusing on the devices. The malicious code made its way into the Orion system and led to a sophisticated attack. The attack led to compromising the whole of SolarWinds’ infrastructure. Around 425 Fortune 500 companies, ten telecom and five accounting firms in the US faced the repercussions of cyberattacks. In the telecommunications sector, addressing these cybersecurity challenges is crucial, and implementing bss transformation can significantly enhance security measures by updating business support systems to manage risks more effectively and safeguard sensitive data. Additionally, the Pentagon, US Military, and the State Dept., alongside several universities and colleges globally came into the clutches of attackers.
At first, attackers added malicious code in the software system, namely, “Orion” of the company. A backdoor to the IT systems of the customer was brought to life, which hackers then utilized to install a handful of malware. This led them to spy on other organizations and companies. This attack exposed the sensitive data of government agencies and the tech giant Microsoft. Out of 33,000 customers who rely on Orion, 18,000 installed the update, which led them to be prone to the attack.
CNA Financial
The Chicago-based Insurance company fell prey to “one of the revolutionary cyberattacks 2021.” The attack wreaked havoc on the CNA network and ultimately affected some of its core systems. The corporate email also took a hit during the attack. When the attack took place, the details weren’t much; however, CNA’s efficiency in handling this misfortune is commendable.
Upon revelation, Phoenix cryptolocker malware was used to carry out a ransomware attack. The malware encrypted the data on more than 15,000 machines spread through network CNA. Even those connected through WFH witnessed the infamous lock until CNA paid the ransom. As per reports, CNA had to pay $40 M to the hackers to resume operations.
The attack is proof that organizations, even those that host some of the cybersecurity industry’s remarkable experts aren’t entirely safe and sound!
JBS USA
JBS USA’s computer networks were compromised by a group of hackers earlier this year. The attack compromised operations and momentarily shut them down in the US, Australia, Canada, and several locations.
Among all cyberattacks 2021, hackers immediately installed malware to lock users out of their database until the ransom was paid. The system-freezing attack led the company to cease operations at 13 locations in the US.
JBS made the payment of $11 million using Bitcoin to get the plants up and running!
Brenntag
Brenntag, the notable chemical distribution company in Germany, was a recent victim of Ransomeware-as-a-Service called DarkSide. With the more than capable RaaS, the attackers seamlessly breached its North American division and stole 150GB of data back in April. The attackers stole birthdates, social security numbers, and individuals’ health data among the stolen data.
The fun aspect about DarkSide is the Ransomeware-as-a-Service is “exponentially moral.” It doesn’t breach or leverage government institutions’ data alongside medicine, education, and non-profit counterparts. Quite moral among most cyberattacks 2021.
Log4J Flaw
Apache’s Java logging library is tremendously vulnerable right now. As the critical vulnerability allows the Chinese origin attackers to exploit the Log4Shell, aka Log4J, hundreds of attacks occur every minute. Log4j is one of the greatest nightmares that security admins have come across in late 2021.
Attackers are already attempting to leverage Log4j vulnerabilities for installing cryptocurrency-mining malware; reports suggest that some are trying to make the most out of the vulnerability by using botnets. Some of the botnets found to have attempted are Tsunami, Kinsing, and Mirai. To add more rubble to this wreckage, Microsoft’s homegrown researchers came up with a revelation that ‘Cobalt Strike’ already made several attempts. Cobalt Strike is an infamous crypto-mining malware that allows bad actors to steal log-in credentials like usernames and passwords.
Among all the cyberattacks 2021, Log4J is nothing less than a calamity. If third-party vendors fail to fix this vulnerability, it will lead to dire scenarios. By the looks of it, the real damage hasn’t begun yet; with more than 1.8 million attempts since Friday, the Log4J flaw is like a ticking bomb.
Attackers have already found access by exploring the vulnerability into the open-source Java library. Even If third-party vendors patch the vulnerability, attackers will be lurking to wreak havoc.
For more details on the Log4J vulnerability, go through this blog – Discover The Extremely Critical Apache Log4J Vulnerability (CVE-2021-44228)
Conclusion
Cyber security has been a priority since the inception of the Internet. To safeguard the network from security nightmares like cyberattacks 2021, a healthy cyber-hygiene routine is necessary. An ideal cyber-hygiene practice detects and addresses security risks, preventing the network from cyber-attacks. Practicing healthy cyber-hygiene habits like continuous vulnerability scanning, time remediation, abiding by security benchmarks, and applying strong security controls will prepare you for uncertain times.
SecPod SanerNow offers a robust CyberHygiene platform to protect your digital infrastructure from attackers. SanerNow eliminates the need for a horde of security management tools as a unified platform by bringing a comprehensive state-of-the-art console for all of your cyber security needs.
SanerNow comes with a plethora of tools like Vulnerability Management, Asset Management, Patch Management, Compliance Management, and Endpoint Management on a single cloud-based console. SanerNow is built on top of the world’s largest security database with features more than 160,000+ security checks. With rapid techniques and end-to-end automation, SanerNow makes it simple to orchestrate cyber hygiene across your organization.
To experience the seamless implementation of CyberHygiene, schedule a demo today; click here!