Most of the Linux distributions have the pkexec binary. The vulnerability (CVE-2021-4034) lies in that binary. The pkexec is a part PwnKit Linux vulnerability Jan-2022, which affects the Polkit open-source application framework used for interaction between privileged and unprivileged processes. Furthermore, the affected binary can also allow executing commands with elevated privileges. A patch management software can help deploy the patches more efficiently.
The vulnerability has existed for about 12 years since the release of version 0.113 of the pkexec component. Almost all of the popular Linux distros are affected, including RHEL, Fedora, Debian, CentOS, and many unknown Linux distros, along with the uneven versions of those distros. Moreover, having a fast scanning vulnerability management tool can be a benefit most of the times.
Vulnerability Details of PwnKit Linux vulnerability Jan-2022
The pkexec command in Polkit has a memory corruption vulnerability that leads to local privilege escalation. This vulnerability allows a regular user to elevate to root. A remote attack is not possible with this particular flaw. Any person having access to a non-privileged user in a system can exploit this vulnerability to gain the privileges of a root user.
Could you look at the PwnKit Linux vulnerability Jan-2022 code snippet from the pkexec binary?
———————————————————————–
534 for (n = 1; n < (guint) argc; n++) { ….. }
610 path = g_strdup (argv[n]);
629 if (path[0] != ‘/’) {
632 s = g_find_program_in_path (path);
639 argv[n] = path = s;
640 }
————————————————————————
- The binary pkexec expects an argument (A command will be passed as an argument). If pkexec command is executed without an argument, in the main program, at line 534, argc value will be 0.
- But the ‘for loop’ is initiated with n=1.
- So the argv[n] in line 610, will read out-of-bounds value from argv[1].
- The out-of-bounds argv[1] points to the first environment variable, “value.”
- The obtained path, “value” is passed to a function g_find_program_in_path(path) in line 632, because “value” is not starting with ‘/’ (as per the condition in line 629).
- The g_find_program_in_path function searches the binary “value” path in the PATH environment variables. As a result, the ‘s’ variable will have the full path of the executable binary, if and only if the binary exists, and at last, the full path of the “value” binary is written out-of-bounds to argv[n] (i.e., argv[1]).
Moreover, the above part of the snippet allows the attacker to craft malicious environment variables and run it as a command using pkexec to attain the privilege escalation which will remove the PwnKit Linux vulnerability Jan-2022
Exploit Snippet
SecPod Security Research Team exploited this vulnerability to gain further technical details.
$ ls -l /usr/bin/pkexec
-rwsr-xr-x 1 root root 23376 Mar 27 2019 /usr/bin/pkexec
- Give front on what is suid.
$ id
uid=1001(secpod) gid=1001(secpod) groups=1001(secpod),4(adm),27(sudo),113(lpadmin),128(sambashare)
- Logged in with a user with less privileges named “secpod” having uid “1001.”
$ ./cve-2021-4034
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),27(sudo),113(lpadmin),128(sambashare),1001(secpod)# whoami
root
- As soon as secpod user performs the exploit, we get access to the root shell.
Publicly available Exploits of PwnKit Linux vulnerability Jan-2022
Individuals coined many exploits as soon as the technical details of the PwnKit Linux Vulnerability Jan-2022 (CVE-2021-4034) became public. Some of the links for the exploit are as follows:
https://github.com/Ayrx/CVE-2021-4034
https://github.com/berdav/CVE-2021-4034
https://github.com/arthepsy/CVE-2021-4034
Impact
Meanwhile, successful exploitation of this vulnerability could allow any non-privileged user to gain root access.
Mitigation
You can use SanerNow to detect and mitigate this vulnerability. (PwnKit Linux vulnerability Jan-2022)
All major vendors have published fixes for their respective OS. In addition, Ubuntu has provided an update for PolicyKit to address the vulnerability in versions 14.04 and 16.04 ESM (extended security maintenance) and more recent versions of ubuntu, such as 18.04 20.04, and 21.04.
Red Hat also released a security update for PolicyKit on Workstation and Enterprise products and extended life cycle support, AUS, and TUS.
SUSE and Debian also have released fixes for this vulnerability for most of their supported versions.
Other Workarounds and Mitigation
For systems that cannot use SanerNow or if the security update of the specific vendor has not published a fix, you can use the following walkaround to mitigate this vulnerability temporarily.
# chmod u-s /usr/bin/pkexec
The above command will remove SUID-bit from pkexec command.
SanerNow can also mitigate the PwnKit Linux vulnerability Jan-2022 by using the attached mitigation_script.
Note: The mitigation will remove SUID-bit from pkexec command. To roll back from the mitigation, use the attached rollback_script.
- First login to the SanerNow platform
- Switch to the account/site-specific view and Go to the ‘VM tool’.
- If your application is vulnerable, Saner lists the above CVE in ‘Top Vulnerabilities’ or ‘Recently Discovered Vulnerabilities’
- Search for this vulnerability in the VM tool. If you are affected, apply the workaround through EM -> Actions.
- Select ‘Software Deployment’ under Actions in EM tool as shown below:
- Next, we can select ‘Upload’ as shown below:
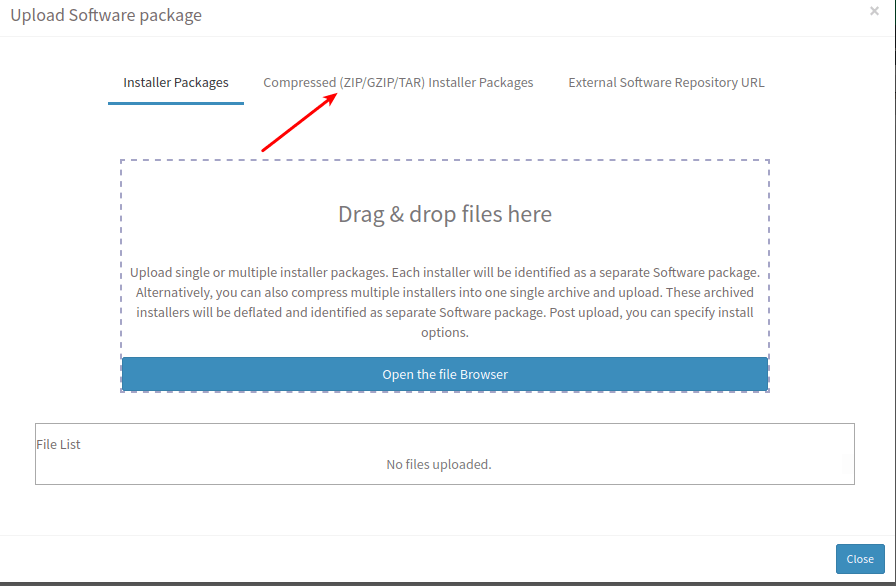
- This will prompt for uploading software package then select ‘Compressed Installer Packages’ and upload the compressed file.
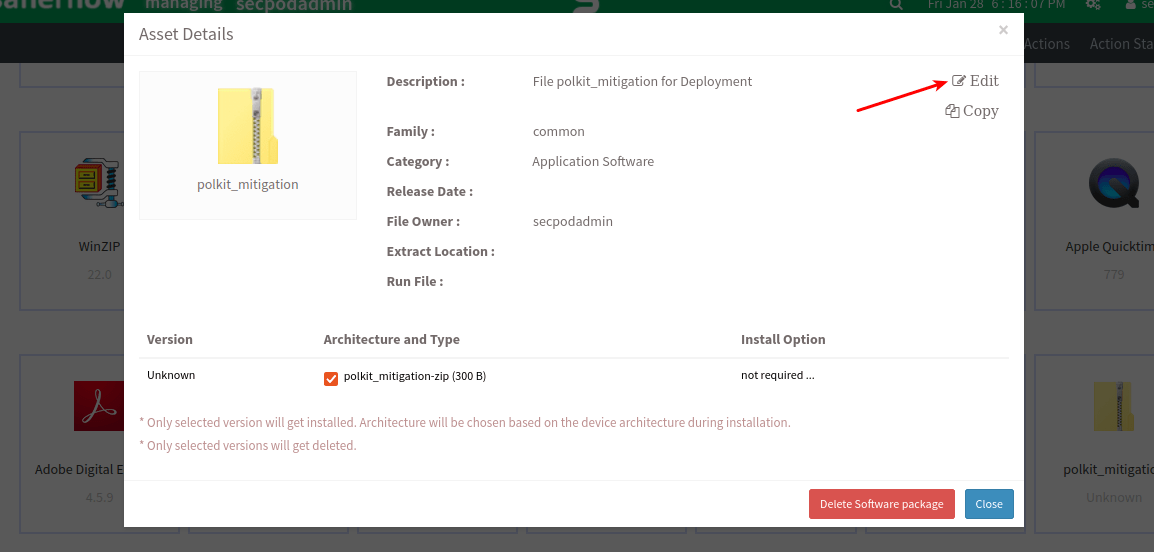
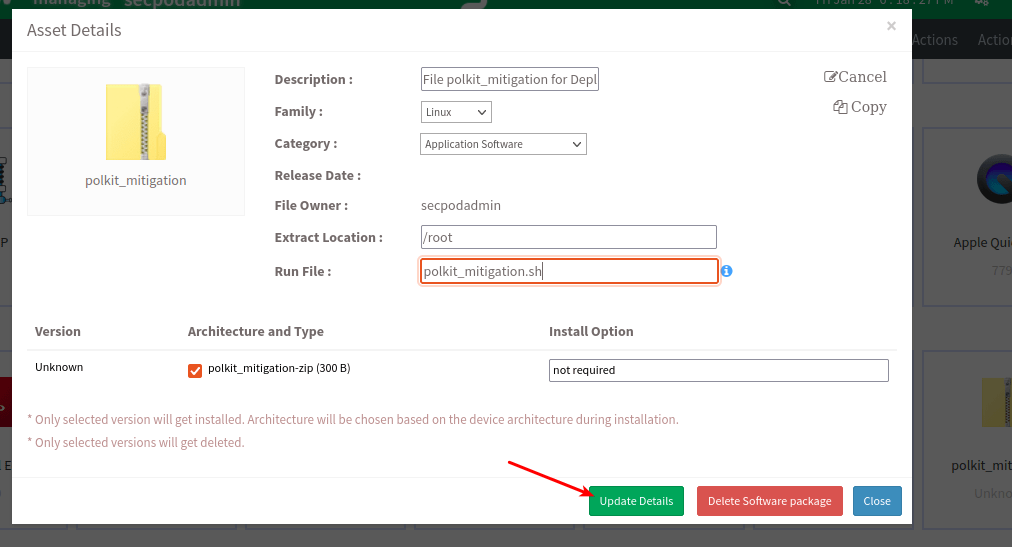
- Once you upload the file, select the file and click on ‘Edit then edit the file by specifying the relevant OS as ‘Family,’ the extraction location as ‘Extract Location’ where you should extract the compressed file, and the file’s name in the ‘Run File’ option as shown.
- Select ‘Update Details’, and the compressed file will update with all the newly added details.
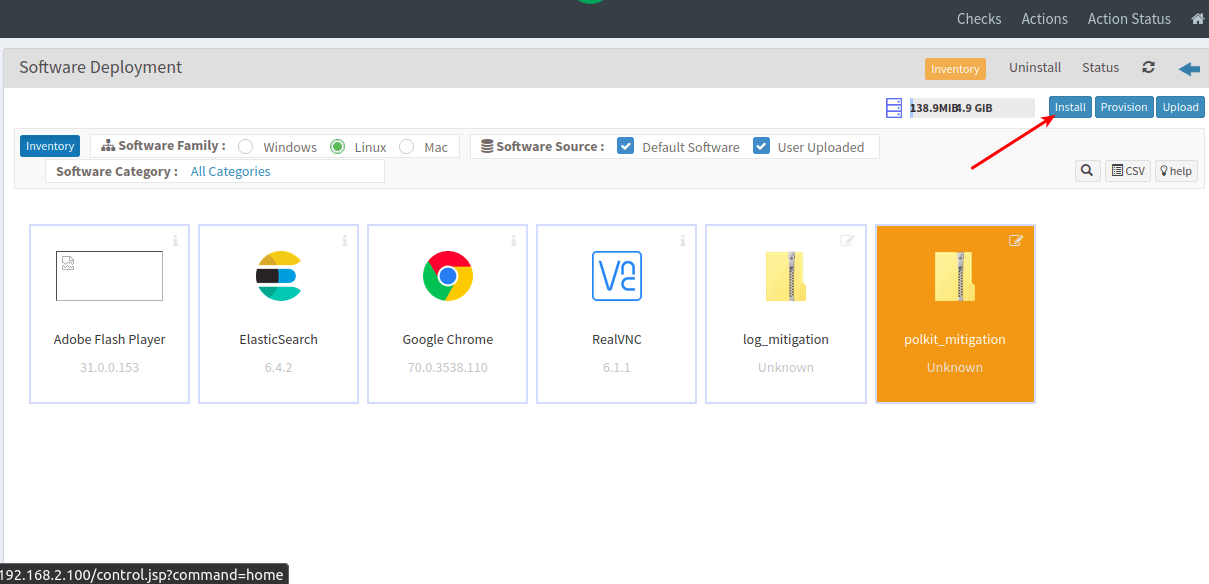
- After the update click on the refresh button and select the file. Click on install.
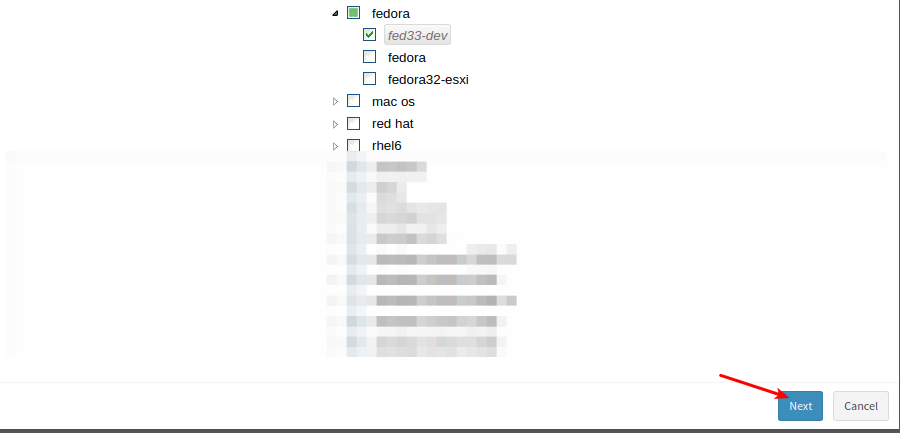
- In addition, select the affected devices where you need to apply the mitigation.
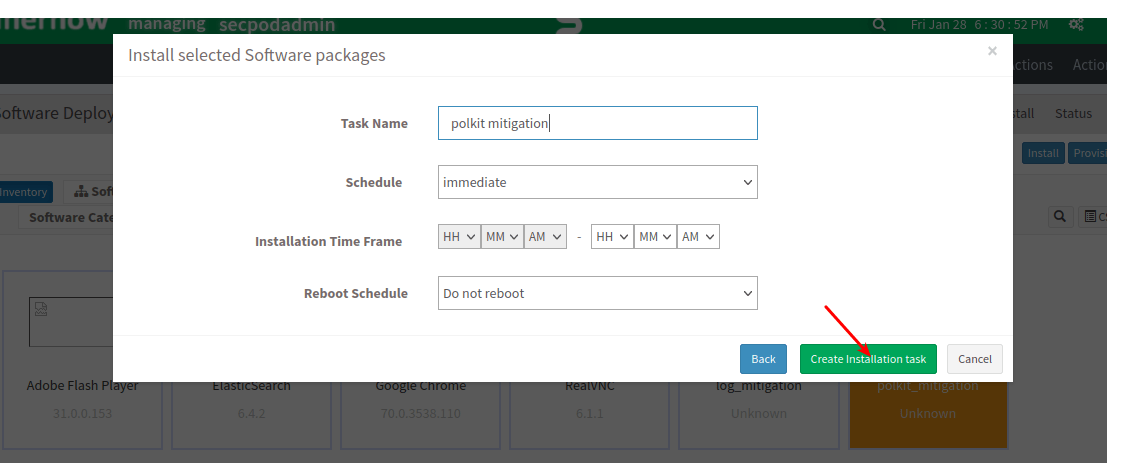
- Update the “Task Name”, “Schedule” the remediation and populate “Reboot Schedule” as required and click on Create Installation task
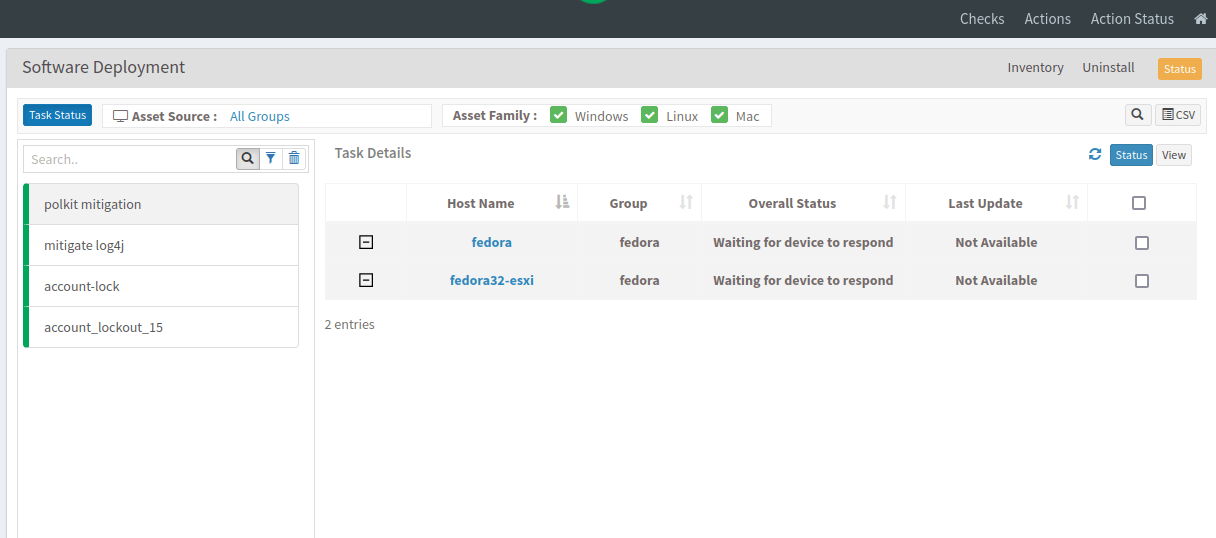
- Once you create the task, it will initiate the job and redirect you to the below-mentioned page:
Therefore, with SanerNow, you can quickly detect and mitigate the Polkit vulnerability in your network. We built SanerNow Vulnerability Management on our home-grown world’s largest vulnerability database, which includes 160,000+ security checks. SanerNow offers the industry’s fastest vulnerability scanning techniques to detect vulnerabilities in less than 5 minutes.