Although there are several ways to secure IT assets, the only way to truly understand the existing security’s effectiveness is to scan and assess the report with several tests. Vulnerability scanning is necessary to evaluate and enhance an organization’s cybersecurity network. The computing environment needs sufficient examination periodically using the latest vulnerability management software and techniques. It helps to find any IT security flaws in the IT assets.
Cyber attackers identify a few vulnerabilities before the software vendor releases the relevant patches. They are termed as zero-day vulnerabilities and hackers are likely to succeed in exploiting them. Once they find such a vulnerability, they need access to the vulnerable system. And even if a zero-day patch is available, not everyone implements it quickly. Therefore, enterprises should have a continuous and automated vulnerability management tool to detect and patch vulnerabilities instantly.
Also Read: Most Painful Products that Keep IT Security Admins Up on their Toes
Discovering Vulnerabilities
Generally, businesses hire cybersecurity experts to secure their computing networks. Here the IT security experts perform security checks using various tools and technology. They may use the same methods and tools hackers use to identify security flaws.
Most of the traditional testing methods are time-consuming and ineffective. In today’s cloud-based technology, several SaaS-based products can automate the entire manual process of scanning and testing. Such software helps IT experts speed up identifying security flaws in applications. It also plays a significant role in examining the compliance policy, responding to security incidents, and testing employees’ cyber security awareness.
Continuous and automated vulnerability management solutions help you identify the vulnerabilities before the attackers. Several cloud-enabled devices can detect vulnerabilities in just a few minutes and reports them as per the company’s security standards.
Assessing Vulnerabilities
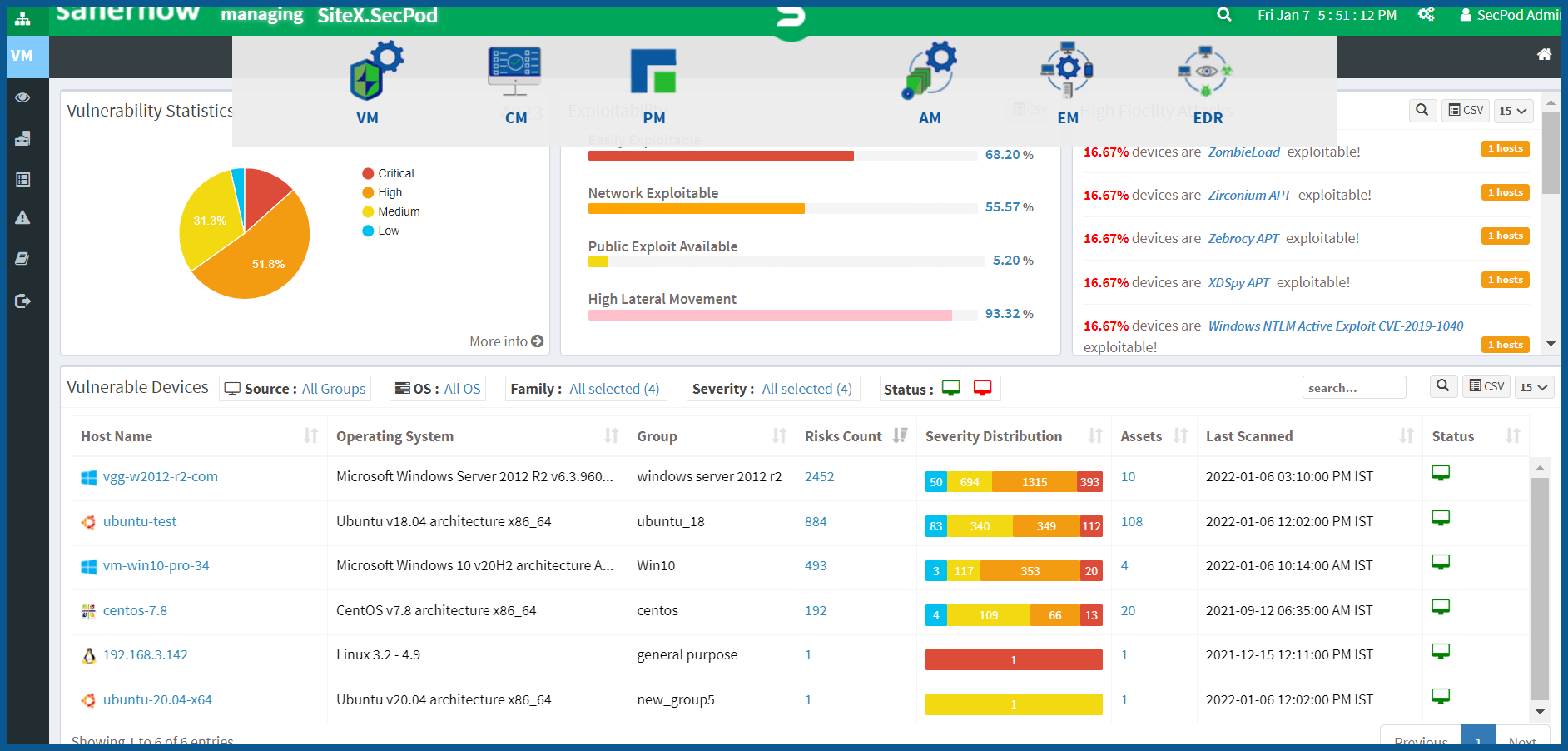
Vulnerability assessment forms the base for an effective patch remediation technique so that the IT security team can quickly fix the security flaws. While evaluating an enterprise’s cybersecurity readiness, identification and assessments are crucial components in improving network security. It is essential to scan and assess the strength of security measures. It helps to address potential security flaws that hackers could exploit in the network.
Detecting the security flaws in the network through hacking techniques is time-consuming and ineffective; the vulnerability management tool scan can identify and rank them as per the severity level.
Once they are identified, organizations tend to simulate and understand the actions of an attacker using various assessments. In some scenarios, IT security teams conduct penetration tests to evaluate the ease of accessing the system data. There are several backend tasks involved in securing the computing network. These security test helps to detect security flaws before hackers. IT security experts view vulnerability scanning and assessment of the report as an essential component in the process of securing an organization’s computing network. They are crucial in optimizing cybersecurity readiness for large private and government enterprises.
Reporting
The continuous and automated vulnerability management report helps IT admins to make better-informed decisions. The scanned vulnerability reports come with the severity level and various suggestions for patch remediation. A real-time vulnerability management program helps enterprises address potential holes in the security system before the cyber attacker tries to exploit them.
How SanerNow Detects Vulnerabilities Instantly
SanerNow is a continuous and automated vulnerability management solution. SanerNow CyberHygiene platform offers continuous visibility to the computing environment, identifies vulnerabilities and misconfigurations, mitigates loopholes to eliminate attack-surface. It helps enterprises find security flaws in real-time. It performs a scan of the entire computing environment in just 5 minutes. And assessment of the vulnerability report is at a rapid pace. As a result, SanerNow’s cyber hygiene measures ensure that attackers have a tough time piercing through the computing environment.
Schedule a demo of SanerNow and identify vulnerabilities in just five minutes. Build a strong defense for your computing environment using continuous and automated vulnerability management solutions.