Vulnerability management services should offer end-to-end solutions that ensure you have a clear understanding of the cybersecurity risks. Security flaws that pose the highest risk to your enterprise can be addressed immediately. There are different types of vulnerability management services through which an enterprise can prevent cyber attacks in advance. They use software as a service or co-manage the cyber security need by outsourcing to the service providers. This article clearly explains both in detail.
Fully Managed Vulnerability Management Program
A fully managed vulnerability management program collaborates with your organization to determine the process for discovering, assessing, prioritizing and remediating various security flaws. The program uses lightweight software that monitors all the cyber security data points from the end-users device operating from different locations. Finally, the overall results are measured to look for continuous improvements. Such a program is continuous and automated for large and mid-sized enterprises in today’s information era. Some of the features are as follows:
Continuous Visibility of Enterprises IT Network
New vulnerabilities are identified every day. Old ones can become more dangerous in the computing network if the hackers include them in automated exploit kits. In such scenarios, possible threats and vulnerabilities are continuously monitored across the entire IT landscape. A fully managed vulnerability management platform offers continuous visibility of the security flaws in all IT assets irrespective of the type of computing environment, be it on-premises or remote networks.
Rapid Assessment and Prioritization
Assessment helps to evaluate each stage of the scanned vulnerability report. It includes IT asset information and the security flaws associated with each of them. The severity level of the vulnerability, the possibility of cyber threats and many other factors. These data points play a significant role while patching a vulnerability.
When it comes to prioritization, the IT security team needs sufficient data. Prioritization is one such technique that distinguishes the severity level of the vulnerabilities into critical, high, medium, and low scales. This data helps IT admins address the high critical cyber security flaws first and the low priority ones later.
Insightful and Actionable Reports
Fully managed service involves a continuous and automated program that offers a comprehensive report and necessary recommended solutions. It makes the job of IT security experts easier while addressing a large number of vulnerabilities. Since the insightful report consists of a Scanning report, Assessment and prioritization data, IT admins can easily make better informed data-driven decisions while securing an IT environment.
Vulnerability Management as a Service
Vulnerability management as a service involves a team of IT security experts who are experienced in using multiple tools and technologies. It is generally done in a co-managed computing environment. The team offers several flexible options both for the remote and on-premises network. In addition, it takes the burden off of your in-house IT security experts due to IT staff augmentations.
Developing an Enterprise Vulnerability Management Program
Providing vulnerability management as a service involves policy governance, breaking down security and operations barriers and many other factors. However, the main objective is to enhance existing practices of cyber security. Some of the factors involved while implementing the program are:
Approved scanning vendors (ASV)
Approved scanning vendor is all about using a set of data security services and tools to decide IT compliance with external scanning requirements. ASV involves external vulnerability scans of the computing network from outside service providers. They can provide insight into any cyber security changes, and they should have gone through a registration process with security standards.
Multiple Tools, Integrations and Processes
Generally, service providers use multiple tools and integrations process to support the organization’s cyber security requirements. The method of remediating security flaws involves various stages such as identifying, assessing, prioritizing and mitigating or remediating the flaws in the IT assets.
Here several enterprises outsource their cyber security requirements to outside agencies. It involves a team of IT security experts with multiple vulnerability management tools for every stage. It is time-consuming and considered ineffective for several enterprises with hybrid computing environments.
The Need and Impact of Continuous Automated Vulnerability Management Service
The vulnerability remediation process includes several steps. It may be gathering scanning reports, retrieving fixes for discovered vulnerabilities and finally applying patches across the computing environment. These tasks are often passed off between IT and security teams through ticketing or various communication channels. This method is time-consuming. For instance, A computing environment with more than 1000 devices would take more than four weeks to patch for an IT and security team.
If an enterprise incorporates automation into the vulnerability management program, it can be reduced to less than 1-2 days. More importantly, you would never miss a vulnerability using automated scans, as it allows you to identify security flaws while being busy with other tasks.
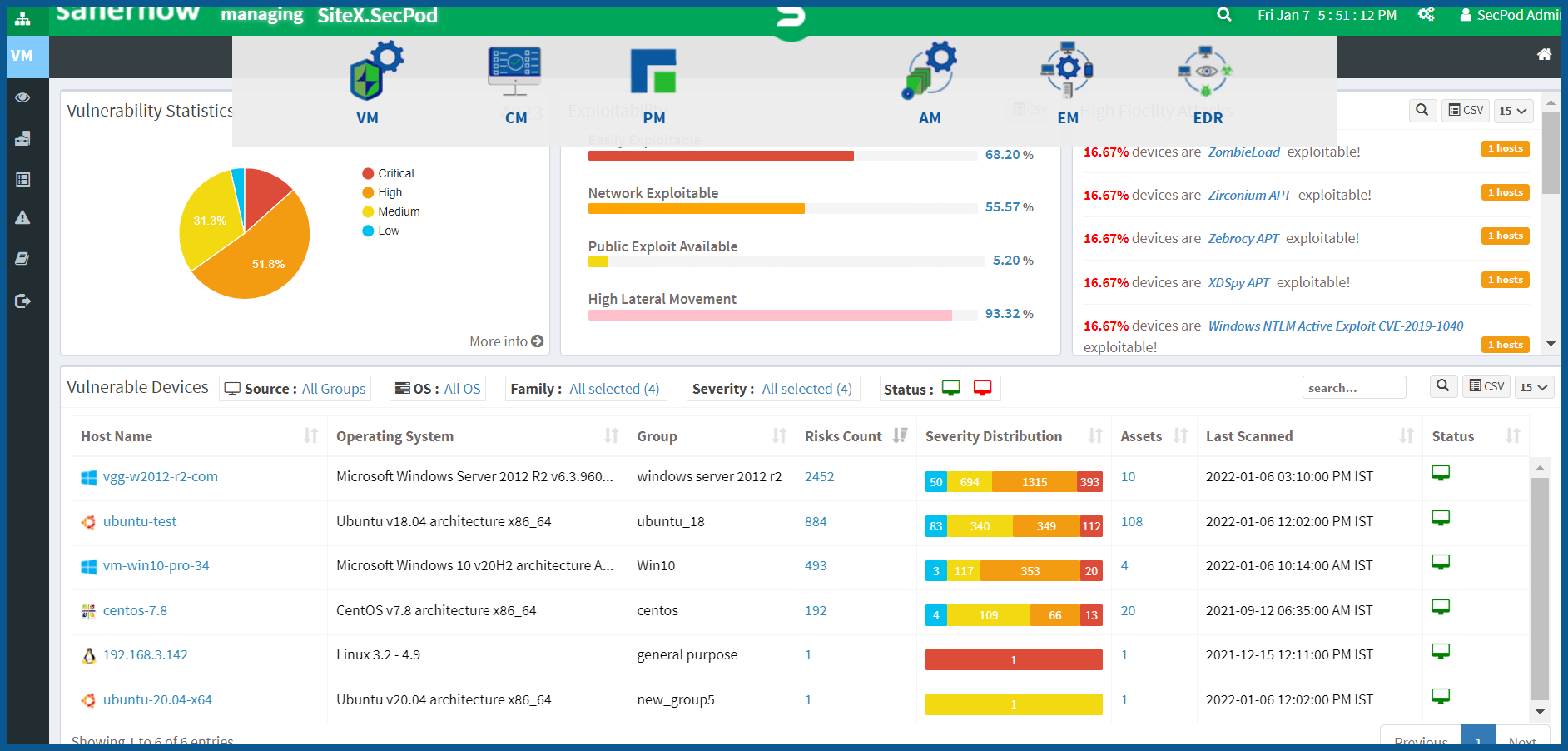
SecPod SanerNow’s Continuous and Automated Vulnerability Management Services
SanerNow is a Cyber Hygiene platform that offers continuous and automated vulnerability management services. Enterprise can prevent cyberattacks as the platform addresses vulnerabilities from multiple perspectives from a single console. It works on the agent-server model. With the help of SanerNow, IT admins can remotely identify and address the vulnerabilities from a centralized server console to prevent cyber threats. The platform manages a large number of devices in a complex computing environment without any performance degradation.
SanerNow eliminates the need of using multiple tools to remediate vulnerabilities as it consolidates numerous use cases into a single console. In addition, it performs a scan of entire IT assets in just five minutes. It also applies necessary fixes to mitigate vulnerabilities and helps automate them.
Schedule a demo of SanerNow and remediate vulnerabilities before getting exploited. Know how continuous automated vulnerability management differs from traditional programs