What is Vulnerability Management?
Vulnerability Management is a process of identifying, evaluating based on priority, reporting, and remediating vulnerabilities in an organization’s IT network. It additionally includes security tools such as a vulnerability management tool, which does thousands of checks to gather information and report results to a dashboard containing information about devices exposed to threats in the organization.
A vulnerability scanner will test all devices alongside the vulnerability database. After the software checks for vulnerabilities, it generates a report. The analysis of the report’s findings would be helpful in remedying vulnerabilities.
Proper vulnerability management software will reduce the surface attack that cybercriminals might exploit, therefore making your network more secure.
Why Do You Need a Vulnerability Management Program?
Cyber-attacks are constantly increasing; it takes a single vulnerability to steal your data. Higher the number of devices in the organization’s computing network, the possibility of cyber threats increases. However, actively managing vulnerabilities long before the attacks makes the organization secure.
The main purpose of having a vulnerability management program is to keep your network safe. Moreover, it does this by analyzing your network for any missed updates or potential threats and then finally applying appropriate patches.
How does the process Work?
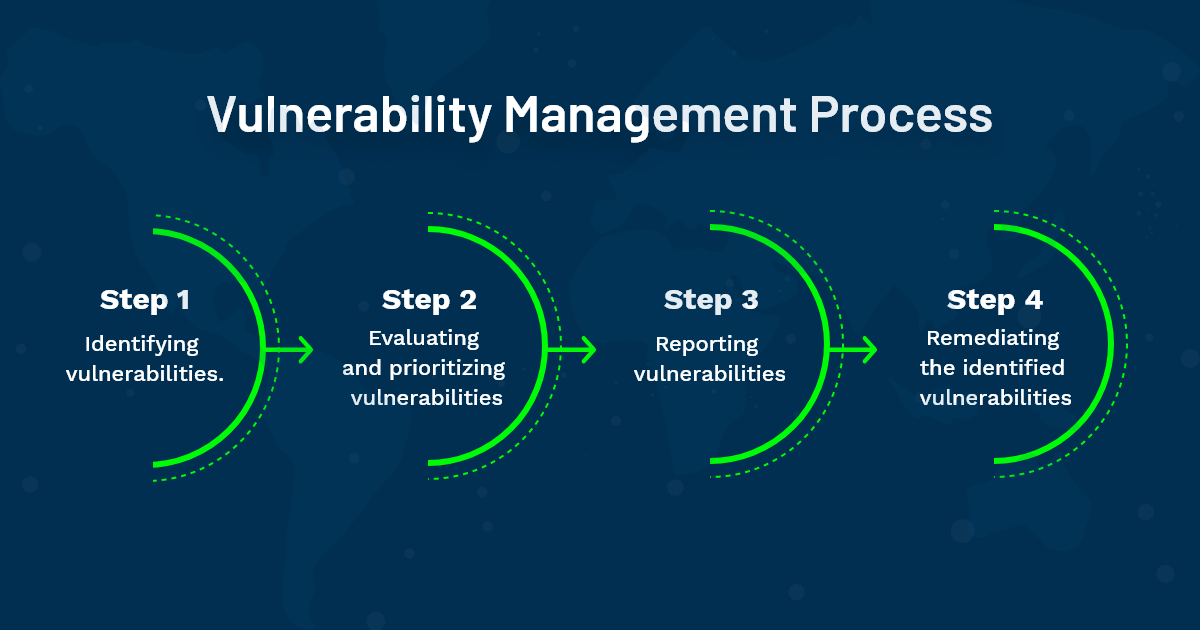
The vulnerability management process breaks down into four steps:
- Identifying vulnerabilities.
- Evaluating and prioritizing vulnerabilities.
- Reporting vulnerabilities.
- Remediating the identified vulnerabilities.
1. Identifying Vulnerabilities:
- Vulnerability scanners identify various devices that are prone to risk in an organization’s network.
- With the help of a vulnerability database (which contains publicly known vulnerabilities), vulnerability scanners associate known vulnerabilities with scanned devices.
- Scanning under limited network bandwidth can disrupt devices.
- The above information assists in maintaining up-to-date vulnerability data and also serves in creating reports.
2. Evaluating and Prioritizing Vulnerabilities:
- All identified vulnerabilities will be evaluated according to their severity level.
- Vulnerability management solutions prioritize vulnerabilities based on CVSS (common vulnerability scoring system).
- CVSS scores the vulnerabilities between 1-10 based on their severity.
- You might face two types of error while evaluating vulnerabilities
a. Type 1 error: Where you report vulnerabilities that don’t actually exist, this is generally called has false positive.
b. Type 2 error: You don’t report vulnerabilities even though they are present, known as a false negative.
3. Reporting Vulnerabilities:
- Finally, the vulnerability scanning tool will generate a report summarizing the identified vulnerabilities and their risk to the organization.
4. Remediating the Identified Vulnerabilities:
- After identifying and prioritizing vulnerabilities, the next step is to remediate them. There are different ways to treat vulnerabilities:
A. Remediation:
-
-
-
-
-
- Process of patching vulnerability before it becomes a security threat.
- Once you have completed applying patches to vulnerabilities, it is recommended to have another round of scans to ensure that vulnerabilities are remediated.
-
-
-
-
B. Mitigation:
-
-
-
-
-
- The impact of vulnerabilities being exploited is reduced due to mitigation. This is necessary when there is no proper patch available.
- It acts as a temporary solution and does not eliminate vulnerabilities.
-
-
-
-
C. Acceptance:
-
-
-
-
-
- When there are low-risk vulnerabilities, and the cost of fixing them is greater, we take no action to fix them.
- For a better understanding, consider you wanted to buy a gadget, but you find its price higher for its features, and you can get a better gadget at the same price. You would choose the latter.
- When other high-risk vulnerabilities could be fixed at the same cost, choosing low-risk vulnerabilities becomes significantly less preferable.
- It is dangerous to avoid addressing discovered vulnerabilities. Therefore, this choice should only be selected when there is no significant impact on the organization.
-
-
-
-
SanerNow Vulnerability Management
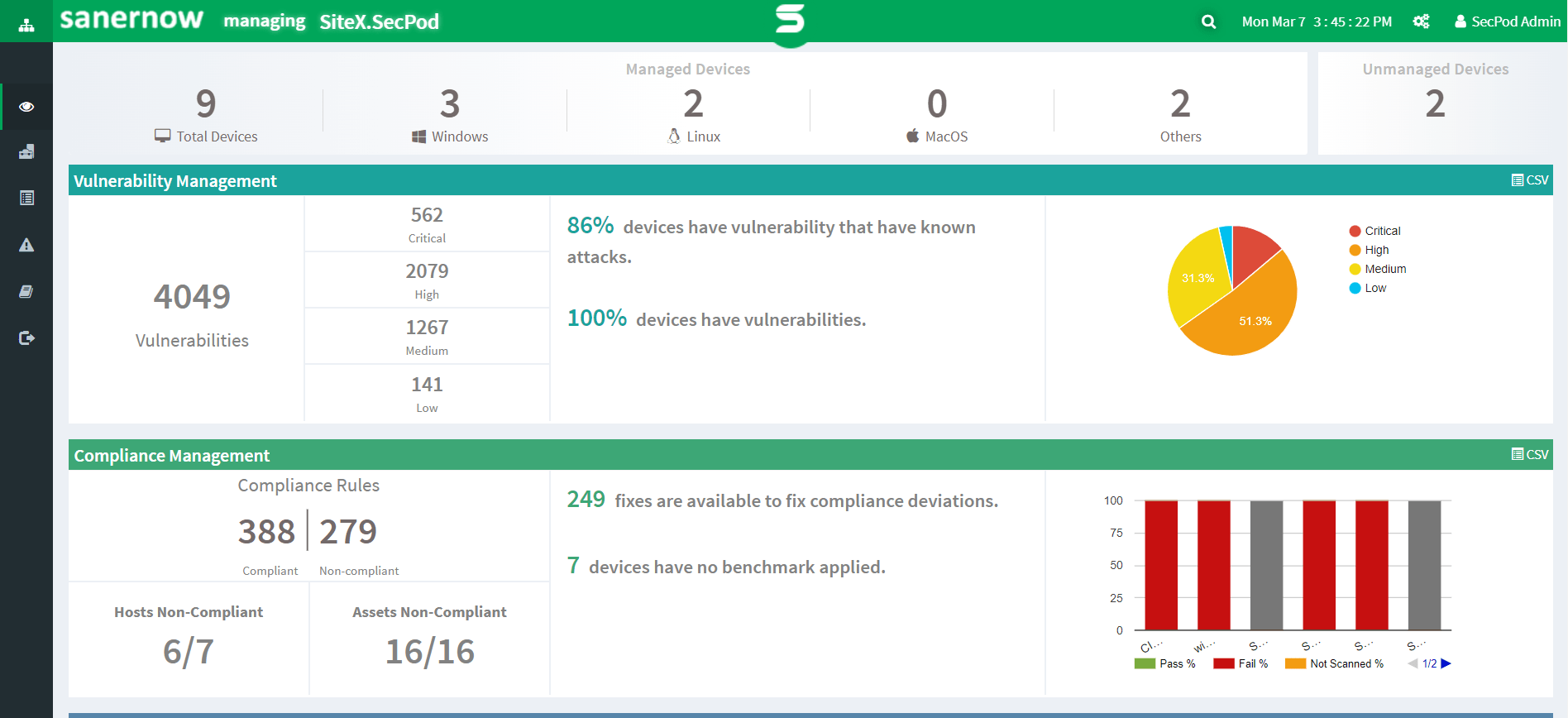
SanerNow is a CyberHygiene platform that provides visibility to a computing environment. Moreover, it detects and remediates vulnerabilities, fixes misconfiguration, keeps the system up-to-date, and acts as an all-in-one platform for all your cyber-security needs.
Finally, you no longer need to be concerned about the never-ending scans, SanerNow can do it in just 5 minutes; With the SecPod’s SCAP feed of over 175,000+ vulnerability checks, it is the industry’s fastest, fully integrated tool that remediates vulnerabilities with its very own integrated patch management.
Explore SanerNow Vulnerability Management by scheduling a demo, or you can also start your free trial