Once the vulnerability assessment process is completed, security teams generate bulky reports for further analysis. Though these reports are detailed and covered with all the information, security teams find it hard to read them. Hence, they lag in drawing clear insights from these reports. Ultimately, they miss the total summary and overview of the vulnerability assessment. As security teams do not get clear visibility over the threat, they cannot take preventive measures to mitigate the flaws further.
In this blog, you will learn about vulnerability assessment reports that make an essential step in the vulnerability assessment process. This process can be simplified with a vulnerability management software.
What are Vulnerability Assessment and Reporting?
Vulnerability assessment is a process to identify, detect, prioritize, and remediate vulnerabilities using automatic software. At the end of the process, i prepare a report to analyze the threats and convey them to related individuals.
Significance of Vulnerability Assessment Reports
Vulnerability assessment reports are an essential part of the vulnerability assessment process. It aims to help you gain insights into the potential vulnerabilities that exist in the systems. You will get a clear idea of how to prevent them. It is said that the whole vulnerability assessment goes in vain if there is no proper report built that you could understand. The vulnerability assessment report is the last step in the process, and it is the least-liked part. Besides, if you want a high-quality vulnerability assessment, you need to know how to build a comprehensive vulnerability assessment report. The report is good when anyone, including non-technical teams, understands your report.
In this article, you will know everything you need to include in a good vulnerability report.
What Should it Include?
-
Build an explanatory executive summary
It is an essential step while building any vulnerability reports. The executive summary’s quality plays a vital role in gaining clear insights into the detected vulnerabilities. The goal of the executive summary is to help you gauge the security posture and learn how the critical issues might impact the environment.
-
Overview of detected vulnerabilities
An overview of the vulnerabilities detected will help you get an outline and a rough idea of the mitigation process. For instance, it contains information about scans, the severity of vulnerabilities, etc.
-
Describe each stage of the vulnerability assessment process
This section of the report should describe all technical details about the whole vulnerability assessment process. The explanation of these steps helps to replicate the assessment anytime by anyone. In addition to this, the performance of the assessment and its outcomes can be analyzed to mitigate them.
-
Elaborate findings
This section of the report should provide details about vulnerability assessment findings. For instance, CVSS scores are ranked by the severity for further prioritization. The report should provide affected systems, severity level, corresponding CVEs, etc.
-
Eliminate bulking of reports
Bulky and hard-to-read reports do not help in effective vulnerability assessments. Hence, a good vulnerability report should be included with charts and graphs to interpret the data easily. It will be more insightful and comprehensive if you incorporate videos and images to understand the threats better.
-
Explain the impact of a vulnerability
The threats’ effects will help analyze the outcome of a specific vulnerability. It can also state the probability and potential of the risk to exploit the systems that will indicate you to take preventive measures and mitigate them instantly. Besides, it is best to include realistic scenarios to predict how hackers can exploit your environment.
-
Keep it simple with direct and clear sentences
The security team will not have enough time to read lengthy reports and long explanations. Hence, the sentences should be short and precise. Add all reference links and source links that will make you understand completely.
-
Recommend mitigation and remediation solutions
For every vulnerability discovered, after analyzing its severity, recommend the possible solution to mitigate it. It will save the time of security teams to research the solutions. Now we know what must be included in the vulnerability assessment report. All the factors should be automated and added to reports soon after the detection of vulnerabilities.
Automation Of Reports For Continuous Visibility Into Risk
Your tools must provide automated reports after the vulnerability assessment process. Automated reports help the security team be more organized and get clear updates on time. Manual reporting takes more time to build and analyze later. Hence, if one or more flaws are detected, your tool must be capable of generating reports instantly.
Automated reports also reduce typos and cut-paste errors done by security teams while building reports manually. In addition, your tools must generate both canned and customizable reports, which makes security teams analyze canned reports and generate customizable reports accordingly.
Therefore, automation of reports will increase the visibility over the threat and help security teams to take preventive measures on emerging vulnerabilities.
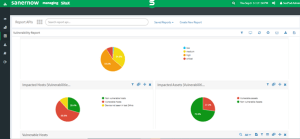
SecPod SanerNow Vulnerability Assessment Report
Along with good vulnerability assessment, SecPod SanerNow provides comprehensive reports that will help you plan to mitigate vulnerabilities instantly. SanerNow provides canned reports and custom reports. Canned reports are in-built reports by the SanerNow. You can also customize your report according to your requirements and download them in PDF format. These reports can be automated and scheduled. Besides, you can configure and receive these reports in your mailbox.
Click here to schedule a demo and check out SanerNow in action!