Bourne Again Shell (BASH) CVE-2014-6271 is widely used and default command interpreter for many Linux flavors, is prone to a command execution vulnerability as discovered by Stephane Chazelas of Akamai. A vulnerability management software can detect this vulnerability.
Bash vulnerability is due to the way bash processes specially crafted environment variables i.e trailing code in function definitions was executed, independent of the variable name, which allows attackers to execute arbitrary commands. A patch management tool can mitigate this vulnerability.
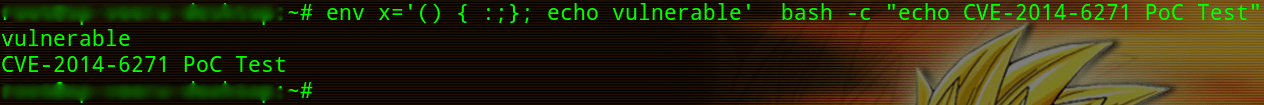
Bash supports exporting not just shell variables, but also shell functions to other bash instances, via the process environment to (indirect) child processes. If we can control the environment variable (which will process by bash, we can run arbitrary commands).
Bash uses various remote application to execute commands. Rates this bash vulnerability as critical due to this nature. Hence users and administrators need to take required actions as soon as possible.
Simple test to check your Bourne Again Shell (BASH) is vulnerable.
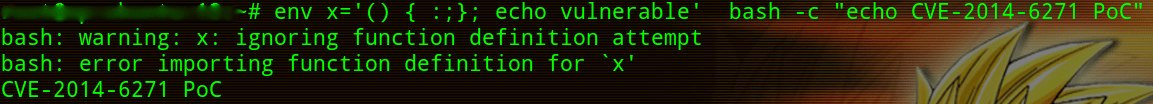
After applying the patch for CVE-2014-6271, same test will return following message.
In many other common configurations, bash vulnerability is exploitable remotely. Most commonly Apache server uses CGI applications to execute through mod_cgi or mod_cgid. Crafted request to these CGI applications when default shell is bash allows executing commands on the server remotely. Similar attacks are also possible via SSH but require authentication to trigger this vulnerability.
How it affects Apache with CGI applications?
CGI applications will parse HTTP headers and store many parameters (User-Agents, Referer, Cookie, Host, etc) in the process environment before executing the application. Attackers can control these HTTP headers. Hence attackers take advantage of this vulnerability to execute desired commands on the server.
When attackers send crafted HTTP header, CGI application stores those headers in the process environment before executing and if the default shell is bash, it will parse the environment variables and executes commands specified after the function.
The bash interpreter will keep parsing outside the function and execute commands outside the function due to the bug, even though it stops parsing after the function.
Crafted User-Agent header looks like
‘User-Agent: () { :;};’ CMD_TO_BE_EXECUTED
‘() { :;};’ – function with syntactically correct with an empty body.
The available patch for CVE-2014-6271 is incomplete but still, users and administrators need to deploy the patch which contains a fix for CVE-2014-6271 and patched bash versions are more complicated to exploit.
– Veerendra GG