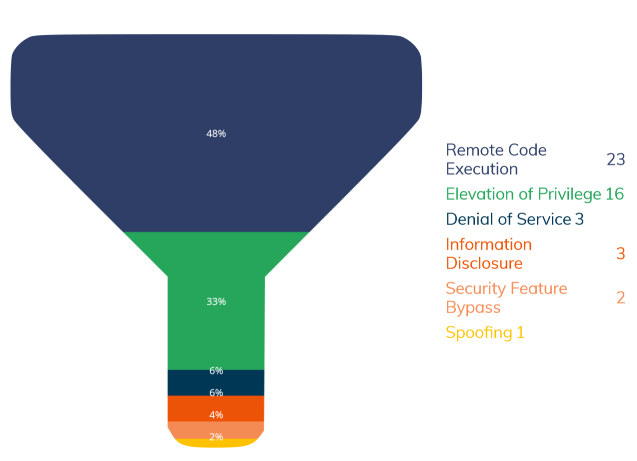
Microsoft’s December 2022 Patch Tuesday has arrived, bringing fixes for two zero-day vulnerabilities, moreover, one of which is currently being exploited. As a result, 49 flaws are addressed with this patch, seven of which are rated as critical. Therefore, these critical flaws allow for remote code execution, which can be potentially harmful. In addition to its December 2022 Patch Tuesday fixes, Microsoft released an update called “Defense in Depth” (ADV220005) to address Driver Certificate Deprecation.
Microsoft December 2022 Patch Tuesday’s two zero-day vulnerabilities are fixed using a patch management tool in this patch Tuesday, in fact, one of which is actively exploited. Meanwhile, the actively exploited vulnerability, CVE-2022-44698, allowed attackers to craft malicious files that could bypass Windows SmartScreen security features, potentially allowing the installation of malware without triggering security warnings. However, the other zero-day vulnerability, CVE-2022-44710, was a DirectX Graphics Kernel Elevation of Privilege vulnerability that attackers could exploit to gain SYSTEM privileges.
Zero-day Vulnerabilities
Further, Patch Tuesday, November 2022, fixed zero-day vulnerabilities like:
CVE-2022-44698 – Windows SmartScreen Security Feature Bypass Vulnerability. In fact, the integrity and accessibility of security features like Protected View in Microsoft Office, which depend on MOTW tagging, could be lost if an attacker creates a malicious file that can evade Mark of the Web (MOTW) safeguards. Thereafter, this vulnerability would prevent SmartScreen from performing a reputation check on downloaded files if successfully exploited. Without a doubt, this could allow known malicious executables to be downloaded without alerting users to their potentially harmful nature.
CVE-2022-44710 – DirectX Graphics Kernel Elevation of Privilege Vulnerability. In fact, the vulnerability would require the attacker to coordinate their actions to win the race carefully and successfully exploit it. Thereafter, if successful, the attacker could gain SYSTEM privileges, allowing them complete control over the affected system. Finally, this could allow the attacker to access sensitive information, install malicious software, or cause harm to the system.
A good patch management software can prevent these attacks.
Microsoft December 2022 Patch Tuesday Critical Vulnerabilities
| Tag | CVE ID | CVE Title | Severity |
| Microsoft Dynamics | CVE-2022-41127 | Microsoft Dynamics NAV and Microsoft Dynamics 365 Business Central (On Premises) Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2022-44690 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2022-44693 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Critical |
| Windows PowerShell | CVE-2022-41076 | PowerShell Remote Code Execution Vulnerability | Critical |
| Windows Secure Socket Tunneling Protocol (SSTP) | CVE-2022-44670 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability | Critical |
| Windows Secure Socket Tunneling Protocol (SSTP) | CVE-2022-44676 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability | Critical |
Microsoft security bulletin summary for December 2022
- .NET Framework
- Azure
- Client Server Run-time Subsystem (CSRSS)
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office OneNote
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Windows Codecs Library
- Role: Windows Hyper-V
- SysInternals
- Windows Certificates
- Windows Contacts
- Windows DirectX
- Windows Error Reporting
- Windows Fax Compose Form
- Windows HTTP Print Provider
- Windows Kernel
- Windows PowerShell
- Windows Print Spooler Components
- Windows Projected File System
- Windows Secure Socket Tunneling Protocol (SSTP)
- Windows SmartScreen
- Windows Subsystem for Linux
- Windows Terminal
Microsoft December 2022 Patch Tuesday product’s
Product: Microsoft Windows.
CVEs/Advisory: CVE-2022-41074, CVE-2022-41076, CVE-2022-41077, CVE-2022-41094, CVE-2022-41121, CVE-2022-44666, CVE-2022-44667, CVE-2022-44668, CVE-2022-44669, CVE-2022-44670, CVE-2022-44671, CVE-2022-44673, CVE-2022-44674, CVE-2022-44675, CVE-2022-44676, CVE-2022-44677, CVE-2022-44678, CVE-2022-44679, CVE-2022-44680, CVE-2022-44681, CVE-2022-44682, CVE-2022-44683, CVE-2022-44689, CVE-2022-44697, CVE-2022-44698, CVE-2022-44702, CVE-2022-44704, CVE-2022-44707 and then CVE-2022-44710
Impact: Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution, and then Security Feature Bypass,
KB’s: 5021294, 5021296, 5021285, 5021303, 5021291, 5021288, 5021289, 5021293, 5021235, 5021243, 5021233, 5021255, 5021234, 5021249, 5021237
Product: Microsoft Office.
CVE/Advisory: CVE-2022-24480, CVE-2022-44713, CVE-2022-44691, CVE-2022-44696, CVE-2022-44695, CVE-2022-44694 and then CVE-2022-44692
Impact: Elevation of Privilege, Spoofing, and then Remote Code Execution
Product: Microsoft SharePoint Server.
CVE/Advisory: CVE-2022-44693 and then CVE-2022-44690
Impact: Remote Code Execution
On the whole, SanerNow VM and SanerNow PM can detect and automatically fix these vulnerabilities by applying security updates. To conclude, use SanerNow and keep your systems updated and secure.