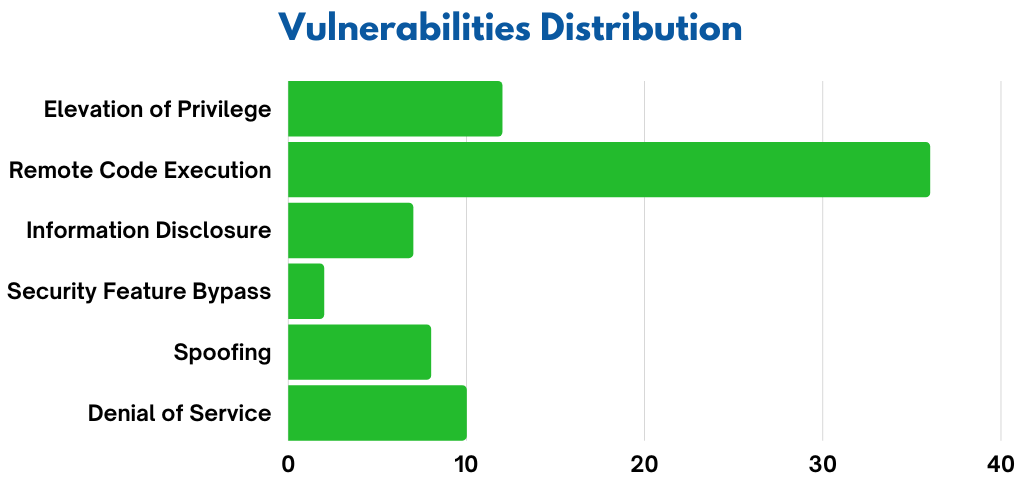
Microsoft has released February 2023 Patch Tuesday security updates, addressing 77 vulnerabilities. 9 are classified as critical as they allow the most severe type of vulnerability remote code execution, and 68 are classified as important. The products covered in the February security update include Windows Graphics Component, Microsoft Publisher, Windows Common Log File System Driver, .NET Framework, 3D Builder, Azure App Service, Azure Data Box Gateway, Azure DevOps, etc. The solution for this problem is a good vulnerability management tool.
This Microsoft February 2023 Patch Tuesday fixes three zero-day vulnerability that is known to be actively exploited (CVE-2023-21823, CVE-2023-21715, CVE-2023-23376). These vulnerabilities came to light with the help of a vulnerability management software.
Zero-Days Vulnerabilities
CVE-2023-21823 | Windows Graphics Component Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8 out of 10. This vulnerability allows remote attackers to execute commands with the highest level of privileges, called SYSTEM privileges, on a Windows system. This can give the attacker complete control over the targeted system if exploited.
CVE-2023-21715 | Microsoft Publisher Security Features Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 7.3 out of 10. This vulnerability allows malicious macros in Publisher documents to run without warning the user, even if the user has enabled macro policies to block such files. An attacker with authentication to the system could exploit this flaw by tricking the victim into downloading and opening a specially crafted file, leading to a local attack on the victim’s computer.
CVE-2023-23376 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8 out of 10. This vulnerability enables attackers to gain SYSTEM privileges, which provide them with complete control over a system. This level of access allows them to perform any action, including installing or deleting programs and modifying or deleting data.
Critical Vulnerabilities
This Patch Tuesday addresses nine security vulnerabilities categorized as “Critical.” These vulnerabilities can pose a significant threat to the security of the affected devices. If exploited, they could allow remote code execution, enabling attackers to gain control of systems and perform various malicious activities.
| Tag | CVE ID | CVE Title | Severity |
| .NET and Visual Studio | CVE-2023-21808 | .NET and Visual Studio Remote Code Execution Vulnerability | Critical |
| Microsoft Office Word | CVE-2023-21716 | Microsoft Word Remote Code Execution Vulnerability | Critical |
| SQL Server | CVE-2023-21718 | Microsoft SQL ODBC Driver Remote Code Execution Vulnerability | Critical |
| Visual Studio | CVE-2023-23381 | Visual Studio Remote Code Execution Vulnerability | Critical |
| Visual Studio | CVE-2023-21815 | Visual Studio Remote Code Execution Vulnerability | Critical |
| Windows iSCSI | CVE-2023-21803 | Windows iSCSI Discovery Service Remote Code Execution Vulnerability | Critical |
| Windows Protected EAP (PEAP) | CVE-2023-21692 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | Critical |
| Windows Protected EAP (PEAP) | CVE-2023-21690 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | Critical |
| Windows Protected EAP (PEAP) | CVE-2023-21689 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | Critical |
Microsoft security bulletin summary for February 2023
-
- .NET and Visual Studio
-
- .NET Framework
-
- 3D Builder
-
- Azure App Service
-
- Azure Data Box Gateway
-
- Azure DevOps
-
- Azure Machine Learning
-
- HoloLens
-
- Internet Storage Name Service
-
- Microsoft Defender for Endpoint
-
- Microsoft Defender for IoT
-
- Microsoft Dynamics
-
- Microsoft Edge (Chromium-based)
-
- Microsoft Exchange Server
-
- Microsoft Graphics Component
-
- Microsoft Office
-
- Microsoft Office OneNote
-
- Microsoft Office Publisher
-
- Microsoft Office SharePoint
-
- Microsoft Office Word
-
- Microsoft PostScript Printer Driver
-
- Microsoft WDAC OLE DB provider for SQL
-
- Microsoft Windows Codecs Library
-
- Power BI
-
- SQL Server
-
- Visual Studio
Product: Microsoft Windows
CVEs/Advisory: CVE-2023-21684, CVE-2023-21685, CVE-2023-21686, CVE-2023-21687, CVE-2023-21688, CVE-2023-21689, CVE-2023-21690, CVE-2023-21691, CVE-2023-21692, CVE-2023-21693, CVE-2023-21694, CVE-2023-21695, CVE-2023-21697, CVE-2023-21699, CVE-2023-21700, CVE-2023-21701, CVE-2023-21702, CVE-2023-21797, CVE-2023-21798, CVE-2023-21799, CVE-2023-21801, CVE-2023-21802, CVE-2023-21803, CVE-2023-21804, CVE-2023-21805, CVE-2023-21811, CVE-2023-21812, CVE-2023-21813, CVE-2023-21816, CVE-2023-21817, CVE-2023-21818, CVE-2023-21819, CVE-2023-21820, CVE-2023-21822, CVE-2023-21823, CVE-2023-23376
Impact: Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution
KB’s: 5022834, 5022835, 5022836, 5022838, 5022840, 5022842, 5022845, 5022858, 5022894, 5022895, 5022899, 5022903
Product: Microsoft Visual Studio
CVEs/Advisory: CVE-2022-23521, CVE-2023-21566, CVE-2023-21567, CVE-2023-21808, CVE-2023-21815, CVE-2023-23381, CVE-2023-41953
Impact: Denial of Service, Elevation of Privilege, Remote Code Execution
Product: .NET Framework
CVEs/Advisory: CVE-2023-21722, CVE-2023-21808
Impact: Denial of Service, Remote Code Execution
KB’s: 5022497, 5022503, 5022727, 5022728, 5022729, 5022730, 5022731, 5022732, 5022733, 5022734, 5022735, 5022782, 5022783, 5022784, 5022785, 5022786, 5022838, 5022858
SanerNow VM and SanerNow PM detect and automatically fix these vulnerabilities by applying security updates. Use SanerNow and keep your systems updated and secure.

