Microsoft’s June 2023 Patch Tuesday addressed 78 flaws, including 38 remote code execution (RCE) vulnerabilities. Among the critical vulnerabilities, a severe RCE bug (CVE-2023-29357) in Microsoft SharePoint Server stood out, potentially allowing unauthenticated attackers on the same network to access sensitive documents and potentially execute ransomware attacks. Therefore, vulnerability management software is essential to detect critical vulnerabilities.
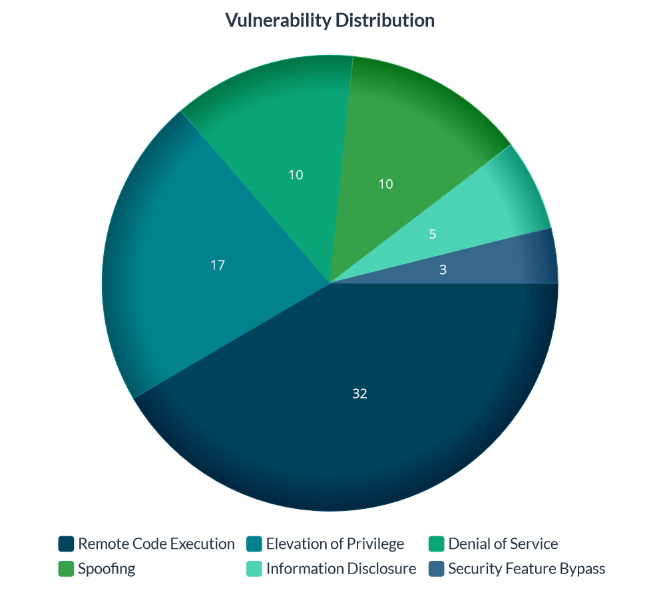
To provide further insight into the distribution of vulnerabilities, the list includes 17 elevations of privilege vulnerabilities, three security feature bypass vulnerabilities, five information disclosure vulnerabilities, ten denial of service vulnerabilities, and ten spoofing vulnerabilities.
An important aspect of this Microsoft June 2023 Patch Tuesday release is the absence of any zero-day vulnerabilities or actively exploited bugs, which is a relief for Windows administrators who typically face heightened pressure during this time.

Critical Vulnerabilities of Microsoft June 2023 Patch Tuesday
CVE-2023-29357 – Microsoft SharePoint Server Elevation of Privilege Vulnerability. In fact, this flaw allows unauthenticated attackers on the same network to exploit the server. However, if an attacker gains admin access to an internal SharePoint server, they can cause substantial damage to an organization. To clarify, this includes accessing sensitive documents, executing ransomware attacks, and replacing genuine documents with malicious copies to infect users within the organization.
CVE-2023-29363, CVE-2023-32014, and CVE-2023-32015 – Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability. The vulnerabilities exist in the Windows message queuing service component, specifically in implementing Pragmatic General Multicast (PGM), an experimental multicast protocol. Moreover, an attacker doesn’t need to be authenticated to exploit these flaws and can remotely target a vulnerable system by sending a malicious file. It’s important to note that message queuing services must be enabled for a system to be vulnerable.
Microsoft security bulletin summary 2023
This release includes security updates for the following products, features, and roles
- .NET and Visual Studio
- .NET Core
- .NET Framework
- Azure DevOps
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Power Apps
- Remote Desktop Client
- SysInternals
- Visual Studio
- Visual Studio Code
- Windows Authentication Methods
- Windows Container Manager Service
- Windows CryptoAPI
- Windows DHCP Server
- Windows GDI
- Windows Group Policy
- Windows Hello
- Windows Hyper-V
- Windows Installer
- Windows iSCSI
- Windows Kernel
- Windows NTFS
- Windows ODBC Driver
- Windows OLE
- Windows PGM
- Windows Remote Procedure Call Runtime
- Windows Resilient File System (ReFS)
- Windows Server Service
- Windows SMB
- Windows TPM Device Driver
- Windows Win32K
Products affected in Microsoft June 2023 Patch Tuesday
Product: Microsoft Windows.
CVEs/Advisory: CVE-2023-24937, CVE-2023-24938, CVE-2023-29346, CVE-2023-29351, CVE-2023-29352, CVE-2023-29353, CVE-2023-29355, CVE-2023-29358, CVE-2023-29359, CVE-2023-29360, CVE-2023-29361, CVE-2023-29362, CVE-2023-29363, CVE-2023-29364, CVE-2023-29365, CVE-2023-29366, CVE-2023-29367, CVE-2023-29368, CVE-2023-29369, CVE-2023-29370, CVE-2023-29371, CVE-2023-29372, CVE-2023-29373, CVE-2023-32008, CVE-2023-32009, CVE-2023-32010, CVE-2023-32011, CVE-2023-32012, CVE-2023-32013, CVE-2023-32014, CVE-2023-32015, CVE-2023-32016, CVE-2023-32017, CVE-2023-32018, CVE-2023-32019, CVE-2023-32020, CVE-2023-32021, CVE-2023-32022
Impact: Denial of Service, Security Feature Bypass, Spoofing, Information Disclosure, Remote Code Execution and then Elevation of Privilege
KBs: 5027271, 5027282, 5027219, 5027225, 5027222, 5027283, 5027281, 5027275, 5027256, 5027279, 5027277, 5027215, 5027231, 5027223, 5027230
Product: Microsoft Visual Studio
CVEs/Advisory: CVE-2023-33144, CVE-2023-27911, CVE-2023-33128, CVE-2023-32032, CVE-2023-33126, CVE-2023-33135, CVE-2023-24936, CVE-2023-24895, CVE-2023-29331, CVE-2023-29007, CVE-2023-25652, CVE-2023-33139, CVE-2023-27910, CVE-2023-27909, CVE-2023-29012, CVE-2023-29011, CVE-2023-25815, CVE-2023-24897
Impact: Spoofing, Remote Code Execution, Elevation of Privilege, Denial of Service, Information Disclosure
KBs: 5026455, 5026454, 5025792, 5026610
Product: Microsoft Office
CVEs/Advisory: CVE-2023-33146, CVE-2023-33137, CVE-2023-33133, CVE-2023-33131, CVE-2023-32029
Impact: Remote Code Execution
KBs: 5002401
However, SanerNow VM and SanerNow PM can detect and automatically fix these vulnerabilities by applying security updates. Therefore, use SanerNow and keep your systems updated and secure.
Also, update previous Patch Tuesday updates to stay secure and safe.

