In this Microsoft Security Bulletin February 2015 Patch Tuesday, Microsoft released Nine security bulletins addressing a total of 56 vulnerabilities using a vulnerability management solution. As usual this month high priority fix is for Internet Explorer, along with Windows Kernel-Mode Driver, Windows Group Policy and Microsoft Office. Internet Explorer alone addresses 41 out of 56 vulnerabilities.
This month three bulletins are rated as Critical, addressing 48 vulnerabilities and six are rated as Important. A patch management tool can patch all these vulnerabilities.
Critical security updates addresses security issues in Internet Explorer 6 to Internet Explorer 11, Windows Kernel-Mode Driver and Windows Group Policy. All of them potentially allow Remote Code Execution and even though Microsoft Office is marked as Important it allows Remote Code Execution. Overall Four out of Eight bulletins allow Remote Code Execution, hence these bulletins are high priority for deploying patches.
The other six important security updates address issues in Microsoft Office, Windows Group Policy, Microsoft Windows, Microsoft Graphics Component and Microsoft System Center Virtual Machine Manager.
Microsoft addresses Zero-Day vulnerability in Windows Kernel-Mode Driver CVE-2015-0010, which allows security feature bypass. This vulnerability was disclosed publicly through the Google’s Project Zero research team i.e after 90 days from the initial intimation to Microsoft due to Google’s automatic disclosure policy.
As mentioned earlier by Microsoft in December IE SSL 3.0 fallback blog,
![]()
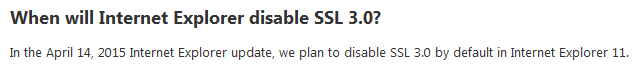
Microsoft released an update which prevents insecure fallback to SSL 3.0 in Internet Explorer 11 for Protected Mode sites and this setting will be turned on by default. For more information, please see KB3038778.
Also Microsoft announced in the blog to disable SSL 3.0 by default in Internet Explorer 11 from April 14, 2015.
Microsoft security bulletin summary for February 2015 in order of severity.
MS15-009: Security Update for Internet Explorer (3034682)
Severity Rating: Critical
Affected Software: Internet Explorer
Impact: Remote Code Execution, Security Feature Bypass
MS15-010: Vulnerabilities in Windows Kernel-Mode Driver Could Allow Remote Code Execution (3036220)
Severity Rating: Critical
Affected Software: Windows Kernel-Mode Driver
Impact: Remote Code Execution, Elevation of Privilege, Security Feature Bypass
MS15-011: Vulnerability in Group Policy Could Allow Remote Code Execution (3000483)
Severity Rating: Critical
Affected Software: Windows Group Policy
Impact: Remote Code Execution
MS15-012: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3032328)
Severity Rating: Important
Affected Software: Microsoft Office
Impact: Remote Code Execution
MS15-013: Vulnerability in Microsoft Office Could Allow Security Feature Bypass (3033857)
Severity Rating: Important
Affected Software: Microsoft Office
Impact: Security Feature Bypass
MS15-014: Vulnerability in Group Policy Could Allow Security Feature Bypass (3004361)
Severity Rating: Important
Affected Software: Windows Group Policy
Impact: Security Feature Bypass
MS15-015: Vulnerability in Microsoft Windows Could Allow Elevation of Privilege (3031432)
Severity Rating: Important
Affected Software: Microsoft Windows
Impact: Elevation of Privilege
MS15-016: Vulnerability in Microsoft Graphics Component Could Allow Information Disclosure (3029944)
Severity Rating: Important
Affected Software: Microsoft Graphics Component
Impact: Information Disclosure
MS15-017: Vulnerability in Virtual Machine Manager Could Allow Elevation of Privilege (3035898)
Severity Rating: Important
Affected Software: Microsoft System Center Virtual Machine Manager
Impact: Elevation of Privilege
SecPod Saner detects these vulnerabilities and automatically fixes by applying security updates. Download Saner now and keep your systems updated and secure.
- Veerendra GG