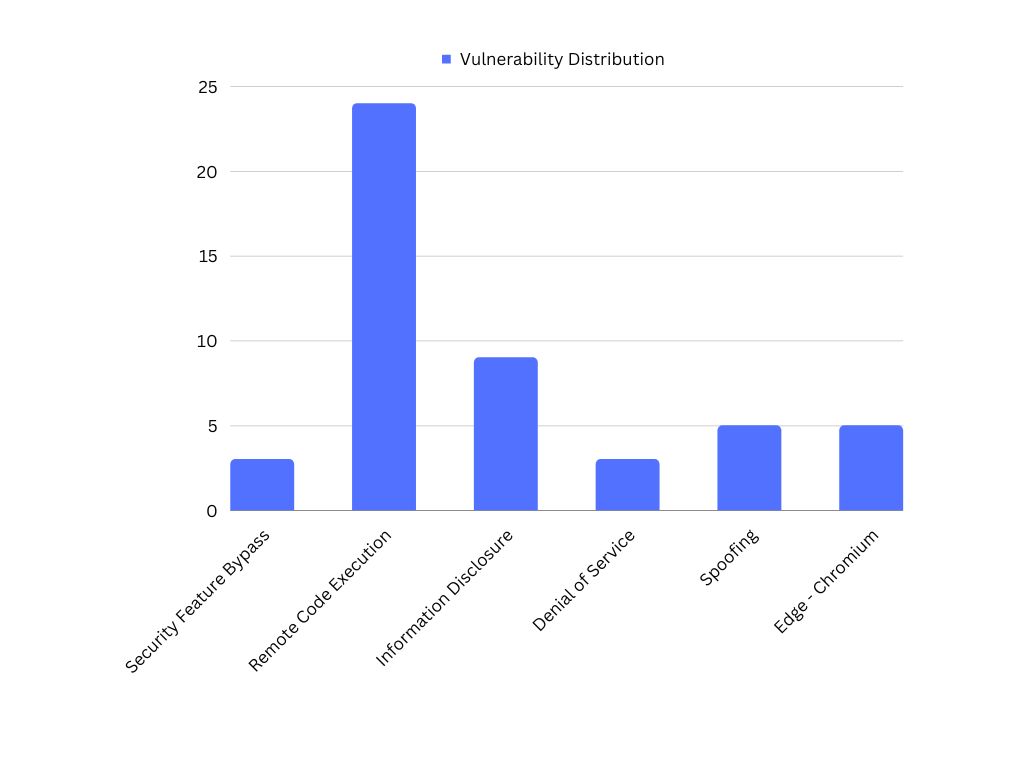
Microsoft has released September 2023 Patch Tuesday security updates, which fixes 59 vulnerabilities. Five are classified as critical, two zero-day(CVE-2023-36802 and CVE-2023-36761), and twenty-four vulnerabilities were related to remote code execution. Vulnerability management tools play a crucial role in identifying critical vulnerabilities and remediating them.
The September security update covers Microsoft Windows, Exchange Server, Microsoft Dynamics, Office, .NET and Visual Studio, Azure, Microsoft Edge (Chromium-based), Windows Kernel, Windows Defender, etc.
Zero-day/Actively exploited Vulnerabilities
CVE-2023-36802 – Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability. The vulnerability enables attackers to acquire SYSTEM privileges if they successfully exploit it. If exploited, this could grant the attacker complete control over the targeted system.
CVE-2023-36761 – Microsoft Word Information Disclosure Vulnerability. When opening a document, including in the preview pane, this vulnerability can be exploited to steal NTLM (Windows New Technology LAN Manager) hashes, which can be cracked or used to access the account.
Critical Vulnerabilities
CVE-2023-36792, CVE-2023-36793, and CVE-2023-36796 – Visual Studio Remote Code Execution Vulnerability. To exploit this vulnerability, an attacker needs to persuade a user to open a specially crafted file in Visual Studio with malicious intent. This implies that the vulnerability can only be exploited when the attacker or the victim executes code from the local machine.
CVE-2023-38148 – Internet Connection Sharing (ICS) Remote Code Execution Vulnerability. This attack is constrained to systems within the same network segment as the attacker and cannot extend across multiple networks, such as a WAN. Instead, it is limited to systems connected to the same network switch or virtual network. An unauthorized attacker has the potential to exploit this vulnerability in Internet Connection Sharing (ICS) by transmitting a specifically crafted network packet to the Internet Connection Sharing Service.
CVE-2023-29332 – Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability. An attacker could attain Cluster Administrator privileges if this vulnerability is successfully exploited. An attacker does not need substantial prior knowledge of the cluster or system and can consistently achieve successful exploitation of this vulnerability.
Microsoft security bulletin summary for September 2023
This release includes security updates for the following products, features, and roles.
- .NET and Visual Studio
- .NET Core & Visual Studio
- .NET Framework
- 3D Builder
- 3D Viewer
- Azure DevOps
- Azure HDInsights
- Microsoft Azure Kubernetes Service
- Microsoft Dynamics
- Microsoft Dynamics Finance & Operations
- Microsoft Edge (Chromium-based)
- Microsoft Exchange Server
- Microsoft Identity Linux Broker
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office OneNote
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Streaming Service
- Microsoft Windows Codecs Library
- Visual Studio
- Visual Studio Code
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows Defender
- Windows DHCP Server
- Windows GDI
- Windows Internet Connection Sharing (ICS)
- Windows Kernel
- Windows Scripting
- Windows TCP/IP
- Windows Themes
Microsoft September Patch Tuesday 2023 affected products:
Product: Microsoft Office
CVEs/Advisory: CVE-2023-41764, CVE-2023-36767, CVE-2023-36765, CVE-2023-36766, CVE-2023-36769, CVE-2023-36763, CVE-2023-36764, CVE-2023-36762, CVE-2023-36761
Impact: Spoofing, Security Feature Bypass, Elevation of Privilege, Information Disclosure, Remote Code Execution
Product: Visual Studio
CVEs/Advisory: CVE-2023-36759, CVE-2023-36758
Impact: Elevation of Privilege
Product: Windows Kernel
CVEs/Advisory: CVE-2023-38150, CVE-2023-38142, CVE-2023-38141, CVE-2023-38140, CVE-2023-38139, CVE-2023-36803
Impact: Elevation of Privilege, Information Disclosure
Product: Microsoft Exchange Server
CVEs/Advisory:CVE-2023-36777, CVE-2023-36757, CVE-2023-36756, CVE-2023-36745, CVE-2023-36744
Impact: Spoofing, Remote Code Execution
However, SanerNow Vulnerability Management and SanerNow Patch Management detect and automatically fix these vulnerabilities by applying security updates. Finally, use SanerNow and keep your systems updated and secure.