An academic research team has developed a novel speculative side-channel attack, which they’ve named “iLeakage.” This attack highlights a security risk targeting vulnerabilities in recent Apple Inc. devices, enabling the extraction of sensitive data from Apple’s Safari web browser.
Technical Details:
Speculative execution is a strategy contemporary processors employ to enhance performance by executing instructions even before determining whether they are genuinely needed. However, if not adequately managed, this approach can introduce security vulnerabilities.
Attackers achieved this by circumventing Apple’s implemented side-channel protections, including features like the low-resolution timer, compressed 35-bit addressing, and value poisoning, while also successfully bypassing Safari’s site isolation policy that segregates websites into distinct address spaces based on their effective top-level domain and one subdomain.
The malicious actors did employ an innovative technique that utilizes the JavaScript window.open API, which enables an attacker’s page to coexist within the same address space as arbitrary victim pages. This technique enables the attacker to access and retrieve the content from other web pages that the user has opened in Safari. This content may include sensitive information such as personal data, passwords, or emails.
However, the researchers point out that executing this attack is challenging and demands a high level of expertise in browser-based side-channel attacks and a deep understanding of Safari’s implementation.
Affected versions:
All versions Safari web browser
Impact:
Successful exploitation of this vulnerability can leak sensitive information of safari users such as personal data, passwords, or emails.
How to use SanerNow to identify if you are affected?
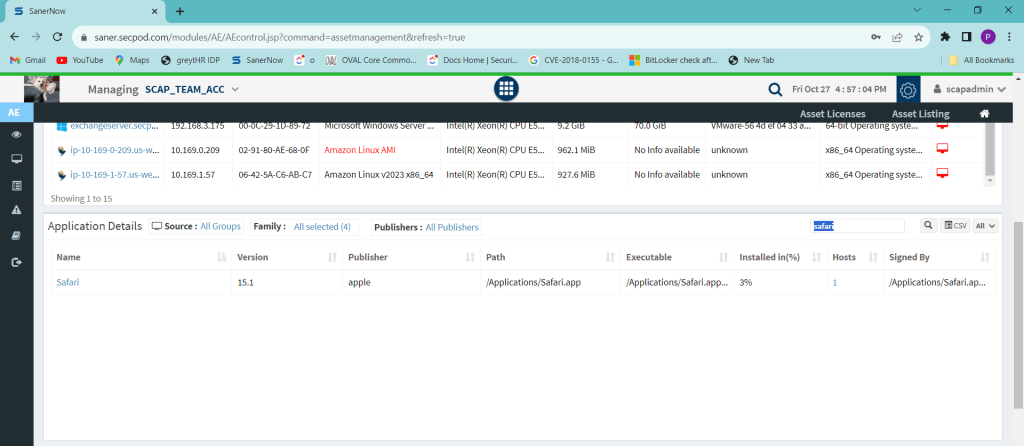
Detection – Identify the vulnerable application Safari in your Infrastructure by using the Asset Exposure module of SanerNow.
Go to the Application Details section and search for “Safari”, it should list all the hosts installed with Safari.
Mitigation:
Apple has introduced a mitigation technique and it is not enabled by default. To enable this follow these steps:
- Open Terminal and run’ defaults write com.apple.Safari IncludeInternalDebugMenu 1′ to enable Safari’s hidden debug menu.
- Open Safari and access the newly visible Debug menu.
- Within the Debug menu, select ‘WebKit Internal Features.’
- Scroll down and activate the ‘Swap Processes on Cross-Site Window Open’ option.
However, Apple has marked this mitigation as unstable. This indicates that it may not provide complete or reliable protection against the iLeakage vulnerability, and there might be ongoing work to improve its stability and effectiveness. We will wait for further updates from the vendor on the availability of Patch and keep you updated. Use SanerNow and keep your systems updated and secure.

