Attack surface has increased by two folds recently. And so, the chance of a cyberattack.
Vulnerability management is the pillar of an organization’s cybersecurity. Be it a startup or an MNC. Mitigating vulnerabilities is always better than fighting threats.
But do you know the top vendors that provide vulnerability management? Well, this blog gives insights about the top vulnerability management vendors available in the market!
The Benefits of Vulnerability Management Tools
From neglected software updates to missing patches, to misconfigurations, and other instances, there is an entire IT ecosystem with weaknesses.
These weaknesses increase the overall risk to an organization.
Some benefits of adopting a vulnerability management solution:
- Responds to threats quicker: New vulns are found every day and never stops. Vulnerability management helps you to move from a reactive to proactive response.
- Keep up compliance standards: Effective vulnerability management helps you achieve regulatory compliance requirements.
- Enhances your security posture: Vulnerability management enhances the overall security posture of your organization by detecting, prioritizing, and remediating vulns.
Top Vulnerability Management Vendors
- SecPod
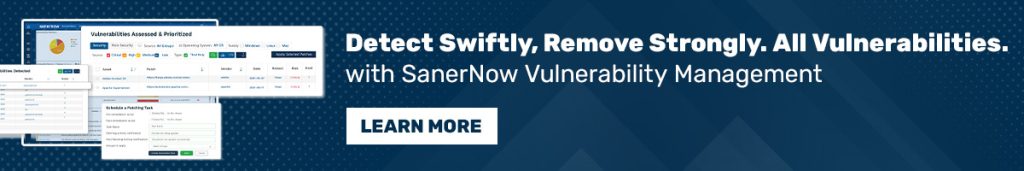
- SecPod’s SanerNow CVEM (Continuous Vulnerability and Exposure Management) quickly detects vulnerabilities and intelligently prioritizes them.
- Swiftly remediates risks for rapid attack surface reduction.
- Seamlessly complies to industry solutions like HIPAA, PCI, ISO, NIST CSF, and STIG.
- SanerNow has the world’s largest built-in vulnerability database, with over 190,000+ vulnerability checks.
- The tool also performs industry’s fastest scanning in under 5 minutes.
- Supports all major operating systems like Windows, Linux, macOS, and over 550+ third-party apps.
- With its single unified dashboard, now manage vulnerabilities, exposures, and other security risks.
- Tenable
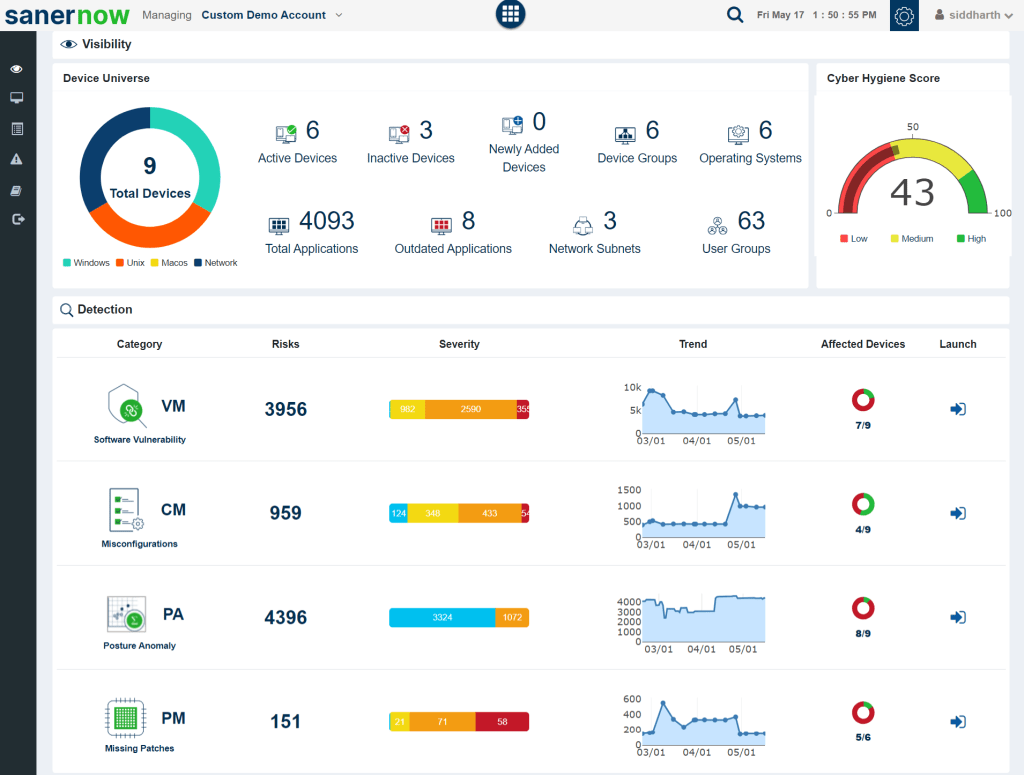
- Tenable’s vulnerability management solution offers continuous scanning and risk-based prioritization.
- The solution focuses more on threat monitoring and remediation.
- Provides insights into vulnerabilities in your attack surface.
- Tenable helps organizations make remediation smoother and helps with compliance standards.
- Qualys
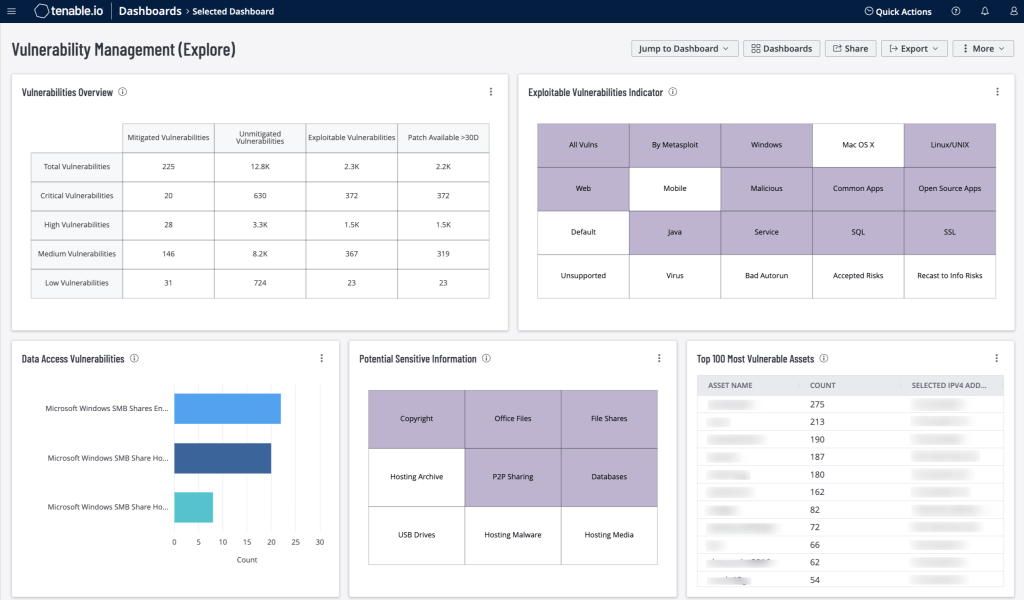
- Qualys provides cloud-based vulnerability management solution.
- Offers asset discovery, vulnerability assessment, prioritization, and remediation solutions.
- It prioritizes integration and automation, ensuring easy workflows and quick response to cyber threats.
- Rapid7
- Rapid7’s vulnerability management solutions focus on comprehensive risk assessment and remediation.
- Their platform offers vulnerability validation and exploitability analysis to prioritize critical vulnerabilities easily.
- Rapid7 provides built-in vulnerability scoring to assess the likelihood of an exploit happening.
- ManageEngine
- ManageEngine’s vulnerability manager plus is a vulnerability management tool offering coverage, visibility, and vulnerability assessment.
- Provides asset categorization features to organize assets based on criticality and functionality.
- With ManageEngine’s patch manager plus, organizations can automate vulnerability assessment and patch management process.
- Cisco
- Cisco’s vulnerability management helps aims to protect organizations networks, endpoints, and cloud environments.
- It offers real time insights on emerging threats and provides proactive vulnerability management.
- Cisco also helps organizations detect and mitigate vulnerabilities in network devices.
Conclusion
Vulnerability management is crucial for every organization IT security. You stay ahead of emerging threats, comply with industry standards, and improve your overall cybersecurity posture. By implementing vulnerability management solutions from top vendors, you say goodbye to vulnerabilities and risks.