We all know that cyberattacks are rising daily! They have caused chaos in every organization, resulting in substantial financial losses.
Wouldn’t it be wonderful if we were able to get information about the attacker’s tactics and techniques?
MITRE developed a cyber advisory named ATT&CK, which talks about the behavior of an advisory (attacker) in the real world. Let’s understand more about this MITRE ATT&CK.
What is MITRE ATT&CK?
MITRE adversarial tactics, techniques, and common knowledge, commonly known as MITRE ATT&CK, is a globally available knowledge-based advisory detailing the attacker’s behavior in real-time throughout an attack’s lifecycle.
It was developed keeping IT and security teams in mind to use the MITRE framework as a tool to understand attacker behavior and safeguard organizations better. MITRE ATT&CK has different metrics and techniques listed. Let’s first understand what its metrics are.
What is MITRE ATT&CK Metrics?
MITRE ATT&CK categorizes attackers’ tactics and techniques into three groups:
- Enterprise Metrics: All attackers’ techniques related to enterprise attacks are covered in this metric. It also contains submatrices for protecting Windows, macOS, and Linux platforms and covers cloud infrastructure.
- Mobile Metrics: Covers all attacker techniques related to mobile devices and network-based devices that don’t require access to mobile devices. Submetrices for this would be iOS and Android.
- ICS Metrics: This matrix protects industries, specifically the automobile sector. It has multiple submatrices of factories, utilities, and other service providers.
The image below shows the enterprise metrics’ overall layout
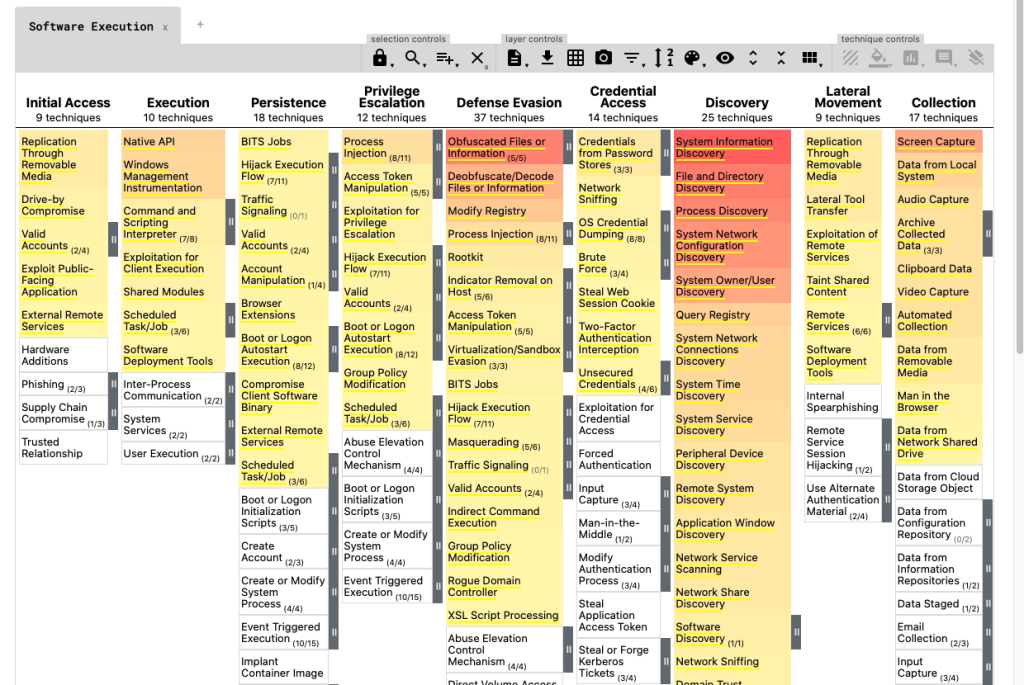
MITRE ATT&CK Tactics
The tactics in MITRE address the “why” question of advisory behavior. In simple words, they state why an attacker exploited an attack. For example, a threat actor will want to damage reputation, cause financial loss, or have a personal agenda.
MITRE ATT&CK has 14 different enterprise tactics, all talking about attackers’ POV:
- Reconnaissance: Gathering information or data for future targeted attacks
- Resource development: Planning to exploit an attack using existing resources
- Initial access: Getting hold of the network through different attack vectors
- Execution: Exploiting attack through malicious code
- Persistence: Attackers trying to maintain their hold on IT network
- Privilege escalation: Gaining higher level authorization to exploit an attack
- Defense evasion: Attacker trying to hide his identity
- Credential access: Trying to steal the credentials, such as names or passwords, from the target
- Discovery: Technique of trying to understand the target environment
- Lateral movement: Going through / scrolling through a target environment looking for a loophole
- Collection: Gathering all the data required for the attackers’ goal
- Command and Control (C2 or C&C): Trying and building a connection with the targeted device
- Exfiltration: Stealing the data
- Impact: Attackers trying to destroy, interrupt, or manipulate the data or device
To avoid these situations, enterprises must opt for continuous and automated tools like SanerNow that can safeguard their IT.
Benefits of MITRE Attack Framework
Now that we understand what MITRE ATT&CK is and also about their metrics and tactics. Let’s understand what benefits the MITRE ATT&CK framework holds:
1. Pre-plan Protection: With this framework, pre-plan the protection strategy and prioritize vulnerabilities, exposures, misconfigs, and other security risks rather than waiting for an attack.
2. Complete Visibility: Have 360-degree visibility of your entire IT to know all the loopholes
3. Assess Loopholes: Identify all the loopholes or risks that have been exploited by an attacker, such as vulns, posture anomalies, misconfigs, exposures, and more.
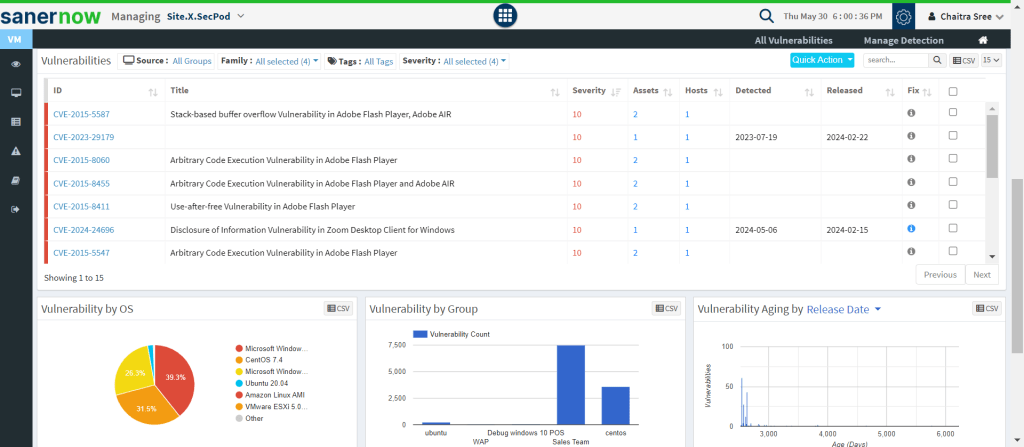
4. Risk Assessment: Prioritize them based on severity levels and CVSS score.
5. Remediate Risks: Remediate all the above risks instantly.
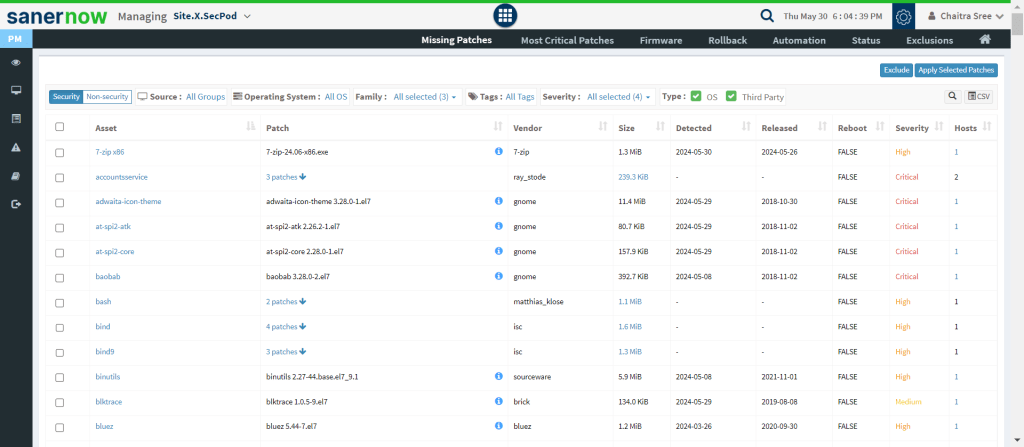
How is MITRE ATT&CK implemented with SanerNow Risk Prioritization?
SanerNow CVEM (Continuous Vulnerability and Exposure Management) continuously and automatically detects risks in real time and fixes them instantly. Its risk prioritization is the world’s first CISA-SSVC-based tool that prioritizes vulnerabilities based on business context, technical impact, in-built vulnerability intelligence, and advanced algorithms.
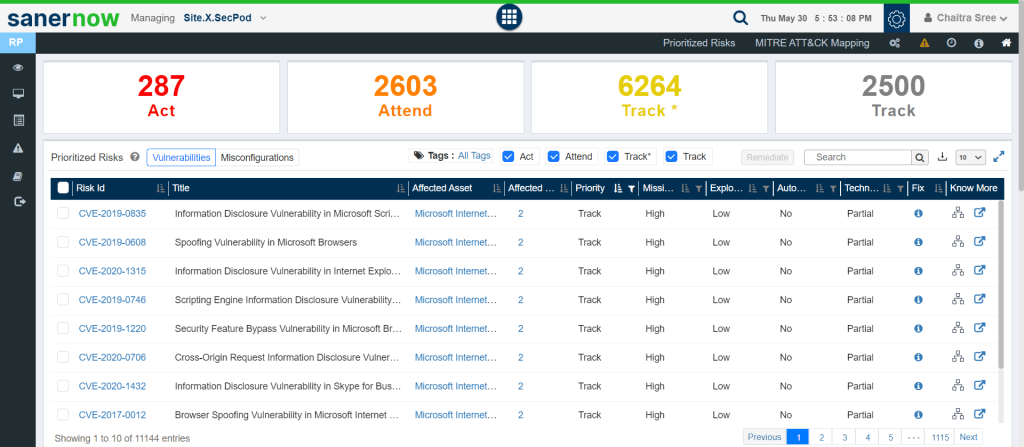
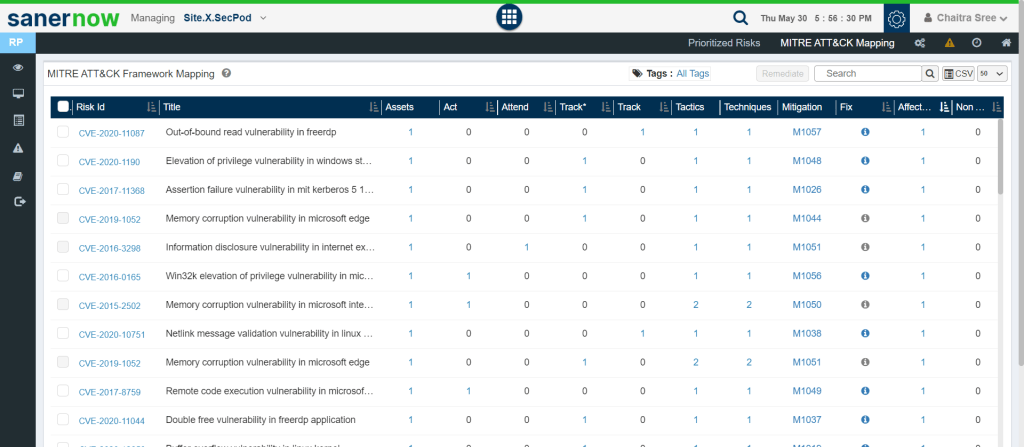
SanerNow has a separate section showcasing MITRE ATT&CK mapping, where each risk detected is mapped alongside different tactics, techniques, and mitigation. This process gives better insights to understand mitigation in devices, which plays an important role in exploitation prevention.
To see the whole suite in action, schedule a demo with our experts: https://www.secpod.com/schedule-demo-sign-up-trial/

