In our very first episode of “Story Behind a Cyberattack,” we are bringing in the most critical vulnerability that hampered the security posture of almost every enterprise– Log4j
Are you ready to hear about the story behind the cyberattack?
Let’s start this journey by knowing what exactly is Log4j.
What is Log4j?
Apache developed Log4j as open-source software that runs across Windows, macOS, and Linux platforms. This open-source software allowed the creation of records for troubleshooting tasks.
Log4shell, popularly known as the Log4j vulnerability, is an Apache critical vulnerability that allows attackers to have complete control of IT. Attackers discovered they could easily exploit this vulnerability on any device by providing specific instructions tailored to the system’s configuration.
How was Log4shell Discovered?
Early Discovery: Log4j, identified as CVE-2021-44228, made headlines in early December and instantly received a CVSS rating of 10 out of 10. According to reports, Log4j was first detected in Minecraft, especially in the Java version.
The threat actors discovered that adding a malicious line of code to an in-game chat control logged them as log4j. If they enter this malicious code, it will cause remote code execution (RCE), a type of cyberattack that can harm devices’ backends. All OSs, Windows, Linux, and macOS, were equally vulnerable.
Later, Chen Zhaojun, a security researcher from Alibaba, reported this critical vulnerability to Apache software. When attackers made this vulnerability public, they initiated mass scanning activity on all enterprise servers.
On December 10th, the UK National Cybersecurity announced a public warning to UK companies about the vulnerability. They stated, “Log4j should be the first priority for all UK organizations to remediate”. Adding to this, CISA director Jen Easterly said, “CISA is working closely with all public and private sector organizations to remediate this critical vulnerability, and also added he has never seen this kind of vulnerability in his career.”
Following this, several incidents and patches from multiple vendors were released. But how did the enterprise overcome Log4j?
Can Log4j be fixed?
While Log4j has impacted many enterprises, continuous real-time detection and remediation can effectively fix this critical vulnerability. IT and security teams have worked hours together researching for the patch.
CISA created a guide that offers assistance in scanning for IT devices and suggests a few best practices for protecting IT from this vulnerability.
Additionally, Apache also maintains the list of patches that were released and applied to remediate Log4j.
Defeating Log4j with SanerNow
SanerNow Continuous Vulnerability and Exposure Management tool detects, assesses, prioritizes, and remediates vulnerabilities, exposures, anomalies, and other security risks and complies with industry benchmarks in a single dashboard.
Following the CISA guide/best practices, here are a list of things that SanerNow will easily achieve.
1. Asset Coverage: Limited asset coverage leads to limited visibility to risks. SanerNow tracks all the hardware and software in the network and presents it in one dashboard.
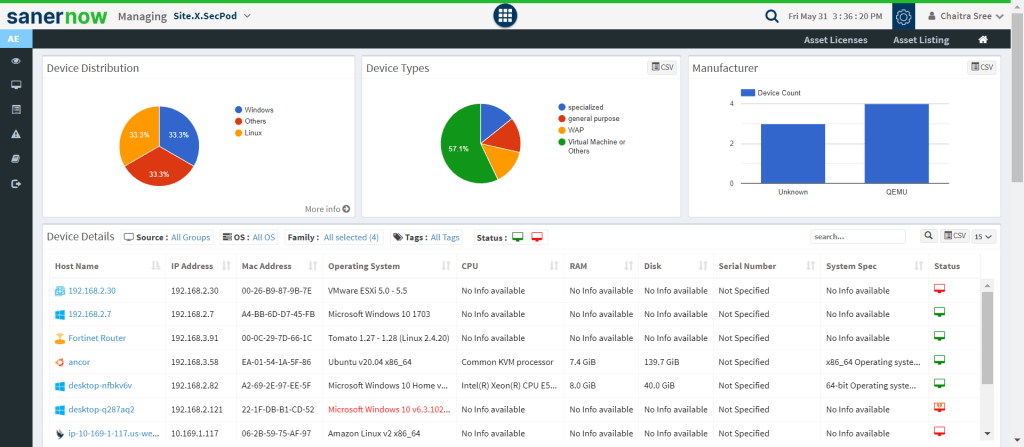
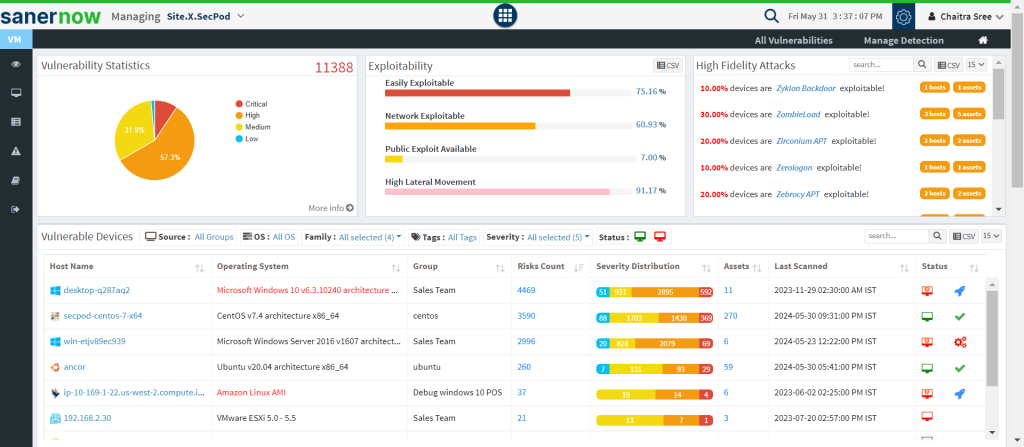
2. Continuous Monitoring: SanerNow effortlessly assesses and monitors your devices anywhere.It detects real-time vulnerabilities, misconfigurations, and other critical risks completely automatically.
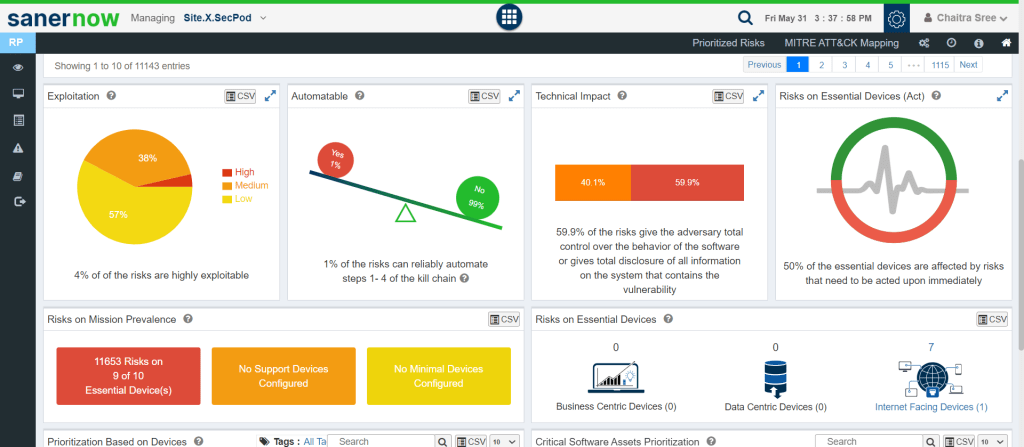
3. Prioritize Risks: Prioritize all detected risks based on severity levels. SanerNow prioritizes risks according to severity levels but also considers other factors such as business context, technical impact, and advanced prioritization algorithms
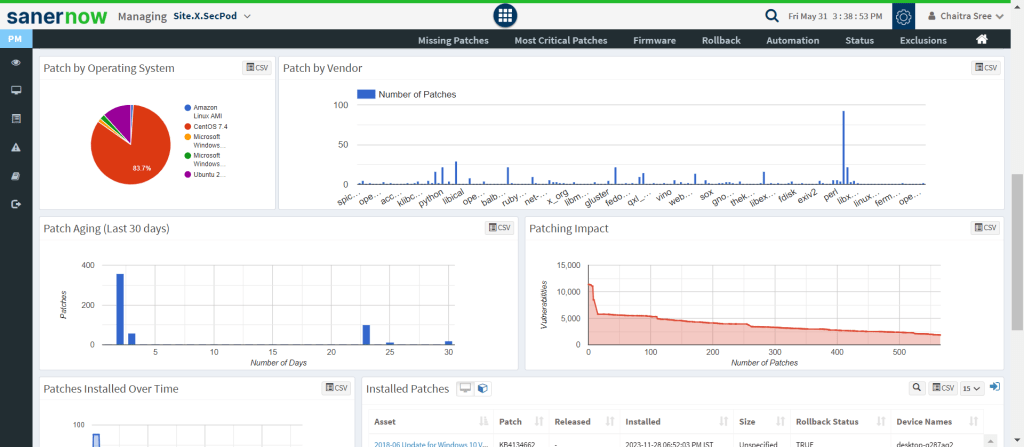
4. Instant Patching: SanerNow supports integrated patching to all major OSs like Windows, Linux, and macOS alongside 550+ third-party apps.
Take a tour of SanerNow’s advanced capabilities and stay ahead of cyberattack, schedule demo here.


