Microsoft released its June edition of Patch Tuesday. Microsoft addressed 51 flaws in its June edition and patched one actively exploited zero-day.
One of the 51 vulnerabilities falls under the Critical category, while 50 have been marked as Important.
Zero-Day Vulnerability
The details for the publicly disclosed zero-day vulnerability Microsoft patched in its June edition are mentioned below.
CVE-2023-50868 (CVSS Score: 7.5) (Severity: Important) Uncontrolled Resource Consumption
This vulnerability allows remote attackers to cause a denial of service (CPU consumption for SHA-1 computations) via DNSSEC responses in a random subdomain attack, aka the “NSEC3” issue.
By exploiting this vulnerability, an attacker could cause the DNS servers to become overloaded and unresponsive due to excessive CPU usage caused by the computation of SHA-1 hashes, resulting in DNS resolution disruption in the networks where the DNS servers are present.
A few other notable vulnerabilities Microsoft fixed during its June editions are as follows.
- CVE-2024-30080 (CVSS Score: 9.8) (Severity: Critical) Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
This vulnerability exists in Microsoft Message Queuing (MSMQ), which allows remote code execution on the affected version of Windows Server and Windows 10, giving the attacker control of an affected system.
An authenticated attacker could send a specially crafted message to the MSMQ service remotely and execute arbitrary code on the target system with SYSTEM privileges. This could enable the attacker to install programs, modify data, and create new user accounts with administrative privileges.
- CVE-2024-30101 (CVSS Score: 7.5) (Severity: Important) Microsoft Office Remote Code Execution Vulnerability
This vulnerability exists in Microsoft Outlook, which allows remote code execution, allowing the user to take control of the affected system. The attacker could possibly deploy malware, tamper with sensitive data, or perform other malicious activities.
- CVE-2024-30100 (CVSS Score: 7.8) (Severity: Important) Microsoft SharePoint Server Remote Code Execution Vulnerability

This vulnerability allows the attacker to execute remote code on the SharePoint Server. The attacker could potentially use a PATH-based attack (CWE-426), allowing the attacker to execute their own programs, access unauthorized data, or make unwanted changes to configuration.
- CVE-2024-30078 (CVSS Score: 8.8) (Severity: Important) Windows Wi-Fi Driver Remote Code Execution Vulnerability
This vulnerability exists in the Windows Wi-Fi Driver, which allows an attacker to perform a remote code execution. An unauthenticated attacker can send a specially designed network message to the Wi-Fi driver and execute malicious code with SYSTEM privileges, leading to complete control of the system.
We recommend that you patch these vulnerabilities immediately using SanerNow Patch Management to secure your devices and prevent attacks on your organization.
In the June month Patch Tuesday, Elevation of Privilege vulnerabilities had a majority share, followed by Remote Code Execution, Denial of Service, and Information Disclosure vulnerabilities.
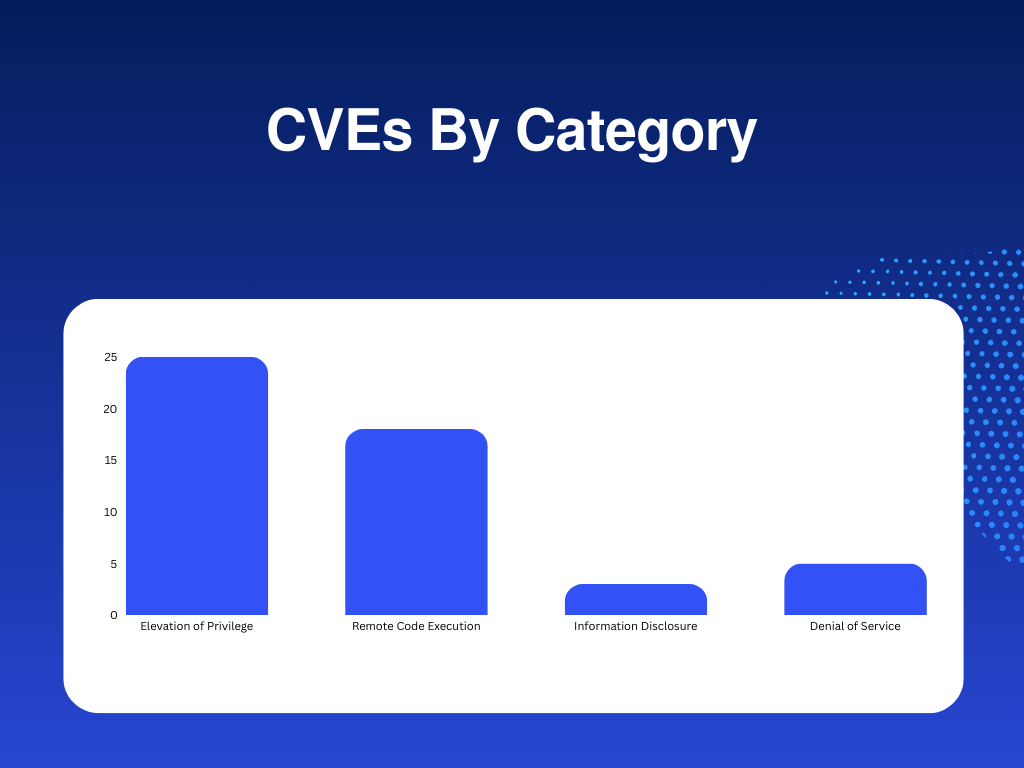
Microsoft Security Bulletin Summary for June 2024
Microsoft released security updates for the following products in its June Patch Tuesday release.
- Azure Data Science Virtual Machines
- Azure File Sync
- Azure Monitor
- Azure SDK
- Azure Storage Library
- Dynamic Business Central
- Microsoft Dynamics
- Microsoft Edge
- Microsoft Office
- Microsoft Office Outlook
- Microsoft Office Sharepoint
- Microsoft Office Word
- Microsoft Streaming Service
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows
- Microsoft Windows Speech
- Visual Studio
- Windows Cloud Files Mini Filter Driver
- Windows Container Manager Service
- Windows Cryptographic Services
- Windows DHCP Server
- Windows Distributed File System
- Windows Event Logging Service
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows Link Layer Topology Discovery Protocol
- Windows NT OS Kernel
- Widows Perception Service
- Windows Routing and Remote Access Service
- Windows Server Service
- Windows Standards-Based Storage Management Service
- Windows Storage
- Windows Themes
- Windows Wi-Fi Driver
- Windows Win32 Kernel Subsystem
- Windows Win32k-GRFX
- Winlogon
SanerNow vulnerability management and SanerNow patch management detects and automatically fixes these vulnerabilities mentioned above by applying security updates. Use SanerNow to keep your systems updated and secure.

