The fight against vulnerabilities and threats is constant. The real race is between cyber-attackers and organizations constantly trying to stay ahead. Attackers give their all to penetrate enterprises’ cyber defense while enterprises defend their IT infrastructure.
Unfortunately, most of the time, enterprises lose this battle. Attackers will attack from anywhere anytime. However, organizations must be two steps ahead of these attackers. A reliant vulnerability management tool is a necessity.
Let’s start making your organization attack-proof.
What you need to know
Once a vulnerability is discovered in your IT, of course the risk increases. However, the risk keeps multiplying as the vulnerability becomes exploitable and more likely known. Risks drop only when applying a patch.
Cyber-attackers work hard to find and exploit weak points in your IT, using various tricks to break in.
Challenges faced by organizations
- No unified view of vulns: Firms often use different tools for scanning and detecting vulnerabilities, each working at its own pace. Without unifying all details about vulnerabilities on a single unified dashboard, remediating them is difficult.
- Incomplete asset inventory: Unless companies know what and how many assets exist, how can they even protect them? They have 1000s of assets which in fact is a large number. Also, the rapid change in the number of endpoints makes it difficult to keep track.
- Inefficient prioritization of vulns: Given a large number of vulnerabilities in an organization, tracking and remediating each one of them is next to impossible. Therefore, risk-based prioritization into different categories based on potential impact to the company is useful.
- Use of outdated tools: Another challenge faced by organizations is the use of outdated or manual tools. The time and effort taken to scan for vulns using such tools is like pouring water into a broken bucket.
IT security teams need a comprehensive tool that focuses on weaknesses, manages vulnerabilities, provides patching, and ensures ongoing protection against cyberattacks, all in one platform.
Use SanerNow to defeat vulns in 5 minutes!
SanerNow Continuous Vulnerability and Exposure Management tool is a bridge between IT and Security teams, here’s how:
- See Everything: Manage vulnerabilities, exposures, and other security risks in a single unified dashboard. It offers a centralized console where both IT and security teams collaborate. Both the teams access the same information, track progress, and communicate effectively.
- Prioritization of Risks: The vulnerabilities are prioritized into Act, Attend, Track and Track*. Both teams work together to prioritize vulnerabilities based on their potential impact on the operations and security.
- Real time visibility: Access real-time visibility into the company’s security posture and IT. Both teams can access up-to-date information about the security vulnerabilities, asset inventory, patch status, and compliance posture, enabling them to make informed decisions together.
- Customizable Reports: Create customized reports tailored to your specific requirements. These reports provide insights into key metrics and KPIs, clearing the way for communication and alignment between teams.
- Integrated Patch Management: Collaborate on patching risks with integrated patch management solution. Both security and IT teams can collaborate and ensure the vulnerabilities are detected and patched immediately or schedule patches during off hours to ensure the company’s business is not disrupted.
- Meet Compliant Standards: Automate and streamline compliance management with SanerNow. Security and IT teams can ensure the companies compliance standards are up to date by regulating their IT devices with HIPAA, PCI, ISO, NIST CSF, and STIG compliance benchmarks.
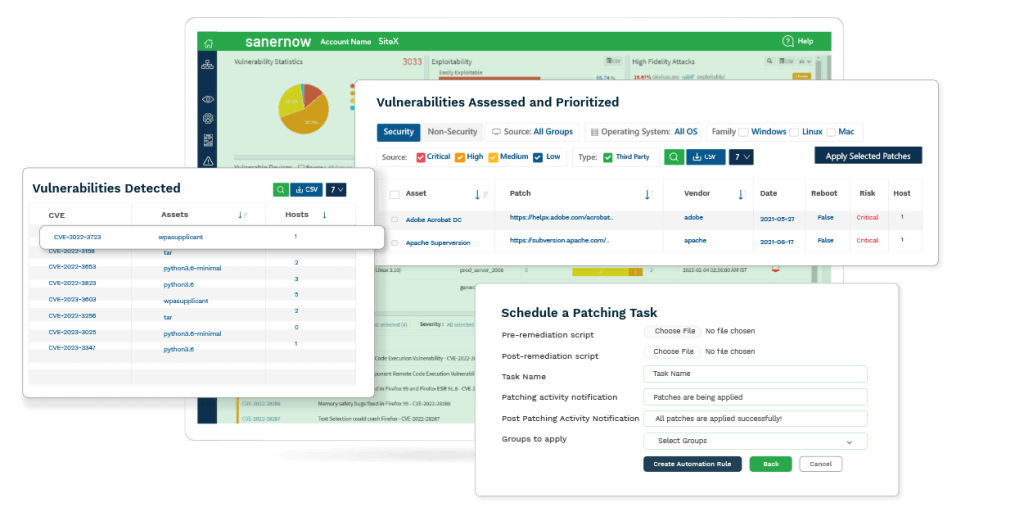
Deep Dive into SanerNow’s Backend
Risk Prioritization: The values of Exploitability, Automatability, Technical Impact, and Mission Prevalence help reach a decision and prioritize whether the risk should be acted quickly.
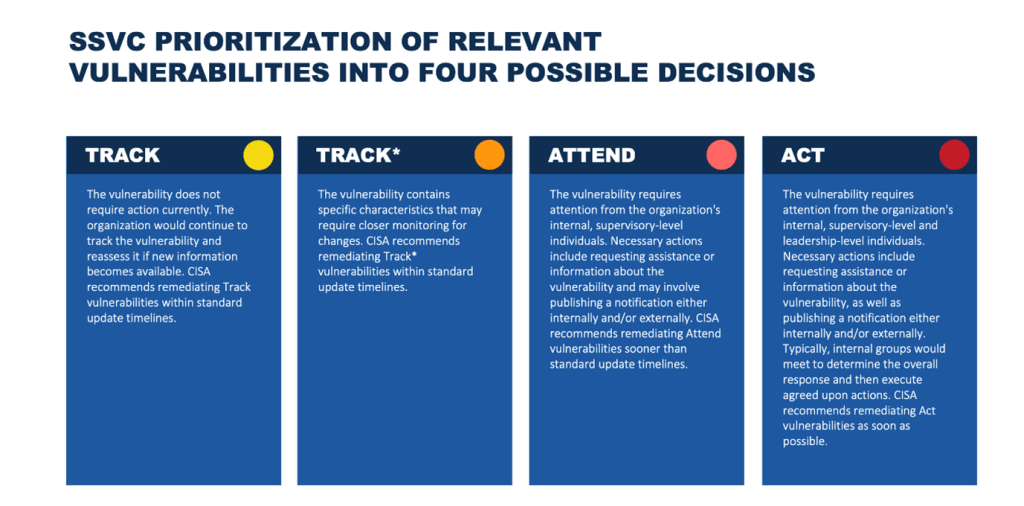
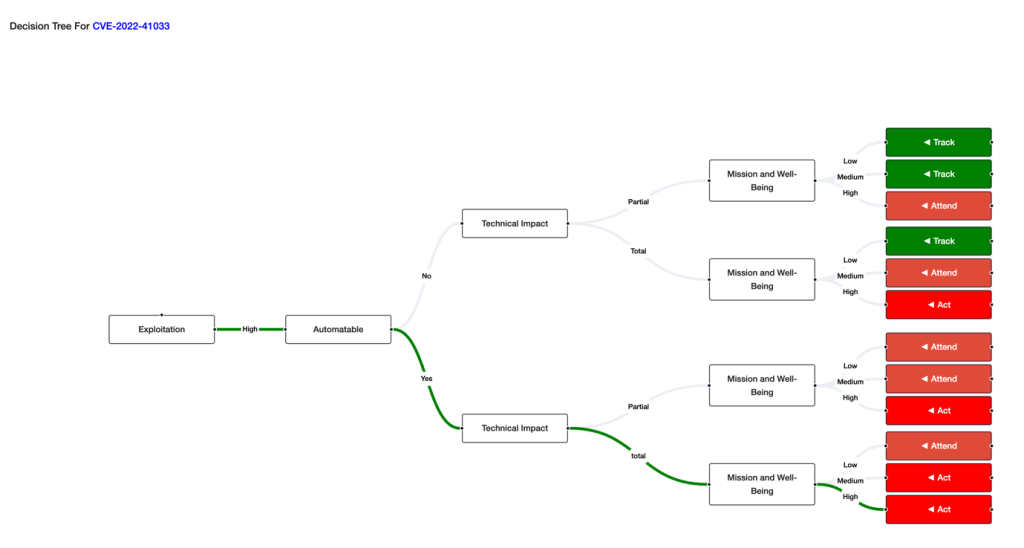
Read this blog to know more about how SanerNow Risk Prioritization works: https://www.secpod.com/blog/understanding-sanernow-risk-prioritization-engine/
Conclusion
Not following vulnerability management properly is like giving a red carpet for them to enter your organization. But there’s always a way to defeat them, and what better way to do so by using SanerNow.