In this episode of “Story behind a cyberattack”, let’s talk about a cyberattack that shook the cybersecurity landscape in 2021. The attack that exposed the potential risks of unpatched systems and highlighted the important of cybersecurity practices. Approximately, 60,000 organizations have been compromised by this vulnerability, and tens of thousands are still unaware that they are exposed to this vulnerability.
Yes, you got it right. It is the famous ProxyLogon Vulnerability that sent shockwaves through organizations across the globe.
Let’s deep dive into this vulnerability and find out how to kill it, shall we?
What is ProxyLogon?
ProxyLogon is the formally generic name for CVE-2021-26855, a vulnerability on Microsoft Exchange Server that allows an attacker bypassing the authentication and impersonating as the admin. Attackers then install web shells, steal data, or launch subsequent attacks within compromised networks.
The attackers behind ProxyLogon, primarily associated with the Chinese state-sponsored hacking group Hafnium, were responsible for a global wave of cyberattacks and data breaches. This began in January 2021 after several zero-day exploits were discovered in Microsoft Exchange Servers. The compromised data and potential unauthorized access to sensitive systems raised concerns of data breaches, espionage, and even ransomware attacks.
How was ProxyLogon discovered?
ProxyLogon was first discovered by Orange Tsai from DEVCORE Research Team.
Here is an in-depth vulnerability disclosure timeline,
| October 01, 2020 | DEVCORE started reviewing the security on Microsoft Exchange Server |
| December 10, 2020 | DEVCORE discovered the first pre-auth proxy bug (CVE-2021-26855) |
| December 27, 2020 | DEVCORE escalated the first bug to an authentication bypass to become admin |
| December 30, 2020 | DEVCORE discovered the second post-auth arbitrary-file-write bug (CVE-2021-27065) |
| December 31, 2020 | DEVCORE chained all bugs together to a workable pre-auth RCE exploit |
| January 05, 2021 | DEVCORE sent (18:41 GMT+8) the advisory and exploit to Microsoft through the MSRC portal directly |
| January 06, 2021 | MSRC acknowledged the pre-auth proxy bug (MSRC case 62899) |
| January 06, 2021 | MSRC acknowledged the post-auth arbitrary-file-write bug (MSRC case 63835) |
| January 08, 2021 | MSRC confirmed the reported behavior |
| January 11, 2021 | DEVCORE attached a 120-days public disclosure deadline to MSRC and checked for bug collision |
| January 12, 2021 | MSRC flagged the intended deadline and confirmed no collision at that time |
| February 02, 2021 | DEVCORE checked for the update |
| February 02, 2021 | MSRC replied “they are splitting up different aspects for review individually and got at least one fix which should meet our deadline” |
| February 12, 2021 | MSRC asked the title for acknowledgements and whether we will publish a blog |
| February 13, 2021 | DEVCORE confirmed to publish a blog and said will postpone the technique details for two weeks, and will publish an easy-to-understand advisory (without technique details) instead |
| February 18, 2021 | DEVCORE provided the advisory draft to MSRC and asked for the patch date |
| February 18, 2021 | MSRC pointed out a minor typo in the draft and confirmed the patch date is 3/9 |
| February 27, 2021 | MSRC said they are almost set for release and wanted to ask if we’re fine with being mentioned in their advisory |
| February 28, 2021 | DEVCORE agreed to be mentioned in their advisory |
| March 03, 2021 | MSRC said they are likely going to be pushing out their blog earlier than expected and won’t have time to do an overview of the blog |
| March 03, 2021 | MSRC published the patch and advisory and acknowledged DEVCORE officially |
| March 03, 2021 | DEVCORE has launched an initial investigation after informed of active exploitation advisory from Volexity |
| March 04, 2021 | DEVCORE has confirmed the in-the-wild exploit was the same one reported to MSRC |
| March 05, 2021 | DEVCORE hadn’t found concern in the investigation |
| March 08, 2021 | As more cybersecurity companies have found the signs of intrusion at Microsoft Exchange Server from their client environment, DEVCORE later learned that HAFNIUM was using ProxyLogon exploit during the attack in late February from Unit 42, Rapid 7, and CrowdStrike. |
| August 06, 2021 | DEVCORE has published the technique details and the story afterward |
Exploitation and Impact
The ProxyLogon vulnerabilities were extremely worrying due to their severity and widespread impact. Given that Microsoft Exchange Server is a widely used email and collaboration platform, many organizations were at risk of this attack. The vulnerabilities’ ease of exploitation and lack of required user interaction made them particularly dangerous.
The attackers, mainly linked to the Hafnium, targeted a broad spectrum of victims, including government agencies, businesses, and non-governmental organizations. The resulting data compromises and potential unauthorized access to sensitive systems sparked fears of data breaches, espionage, and even ransomware attacks.
Kill the chance of ProxyLogon with SanerNow
Have you heard the saying, “Fight fire with fire”?
To fight ProxyLogon, you need the best solution out there. That’s SanerNow CVEM for you.
SanerNow Continuous Vulnerability and Exposure Management does everything from end-to-end. Detect, defend and defeat vulns from start to finish!
Here are bunch of amazing things SanerNow CVEM does to make your IT attack-proof.
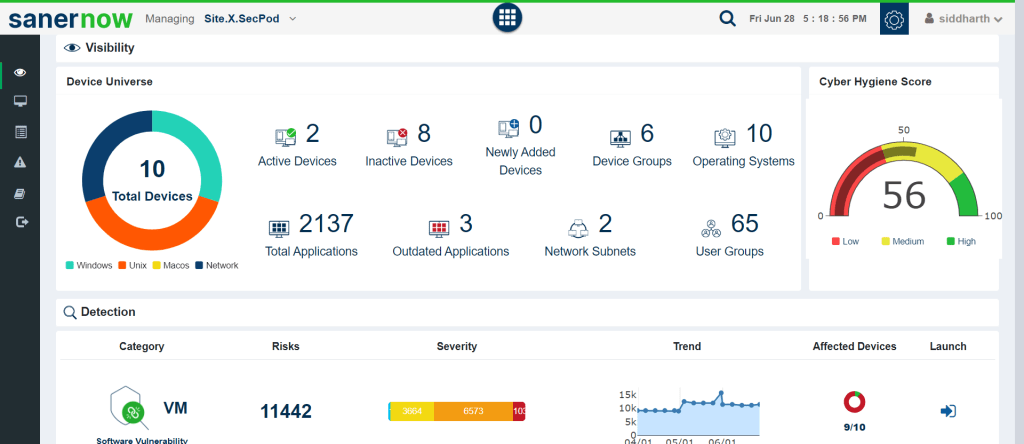
- See Everything: Manage vulnerabilities, exposures and other security risks like ProxyLogon, all from a single unified dashboard.
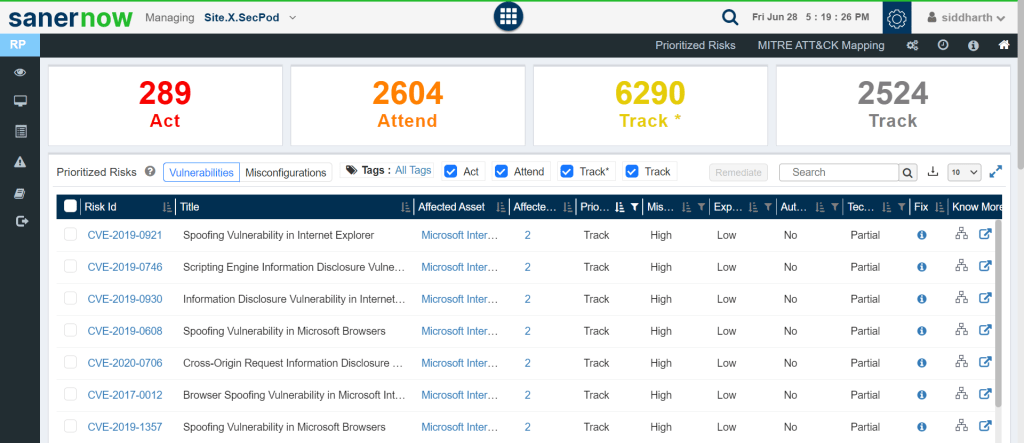
- Prioritization of Risks: With the world’s first, integrated, effective, and rapid risk prioritization based on CISA’s SSVC based framework, prioritize risks into Act, Attend, Track and Track*.
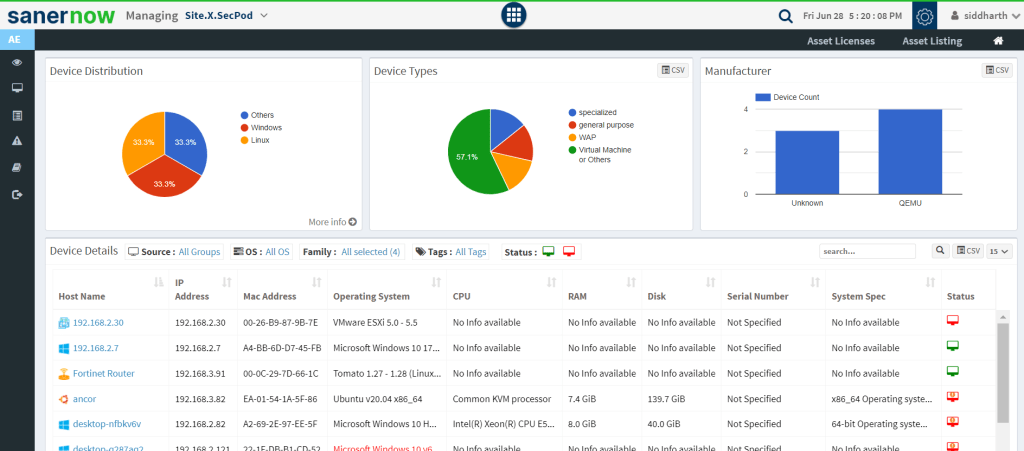
- Real-time Visibility: Access real-time visibility into the organization’s security posture and IT infrastructure.
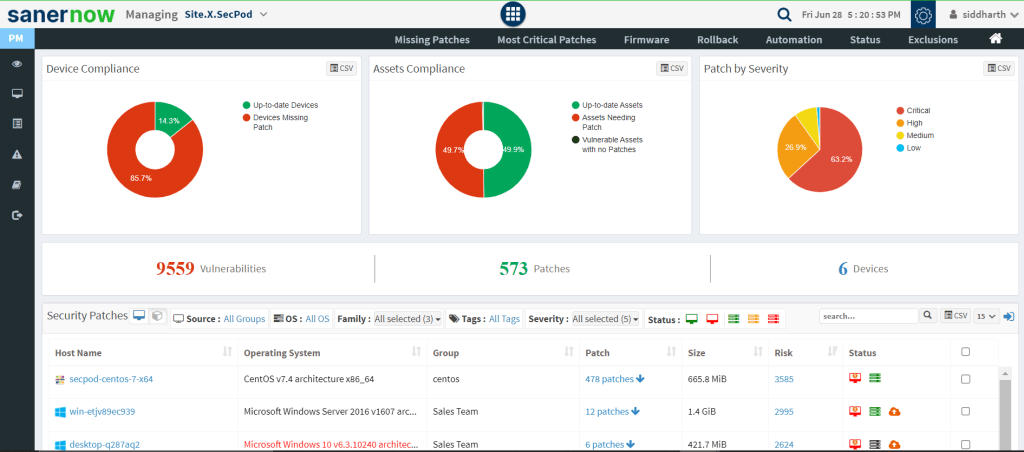
- Integrated Patch Management: Collaborate on patching risks with integrated patch management. Ensure the vulns are detected and patched immediately or schedule patching during off hours to ensure the business is not disrupted.
- Meet Compliance Standards: Automate and streamline compliance management with SanerNow. Ensure the company’s compliance is up to date by regulating the IT devices with HIPAA, PCI, ISO, NIST CSF and STIG compliance benchmarks.
Also, here are some more cool benefits of SanerNow you don’t want to miss.
- SanerNow has the world’s largest built-in vulnerability database, with over 190,000+ vulnerabilities checks.
- It performs the industry’s fastest scanning in under 5 mins.
- Supports all major operating systems like Windows, Linux, macOS, and over 550+ third party applications.
- Seamlessly comply with compliance benchmarks and build the trust of stakeholders.
Conclusion
ProxyLogon highlighted the critical need for continuous cybersecurity practices and the importance of timely patch management. While the vulnerabilities themselves have been addressed through updates from Microsoft, the incident serves as a reminder of the ever-evolving threat landscape. Utilizing tools like SanerNow Continuous Vulnerability and Exposure Management can help organizations stay ahead of potential threats, ensuring their networks remain secure and resilient against future cyber-attacks.


