Microsoft released its July edition of Patch Tuesday. In it, Microsoft addressed 142 flaws and patched four zero-day bugs.
Of the 142 vulnerabilities, 134 belong to the Important category, five to the Critical category, and three to the Moderate category.
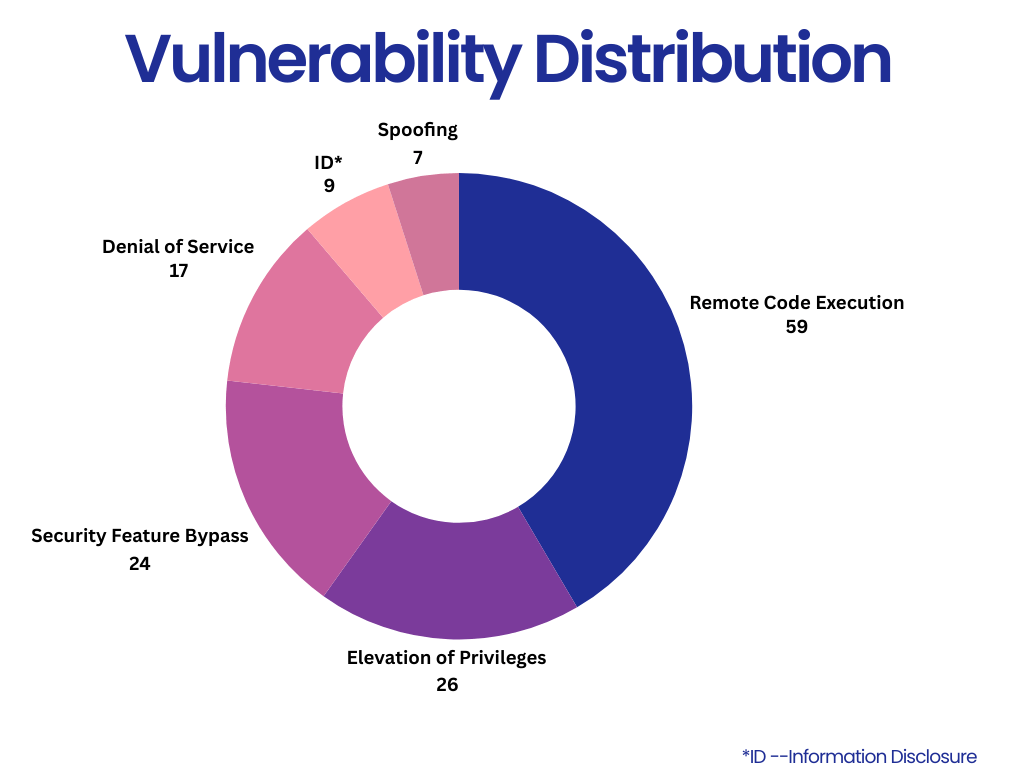
Zero-Day Vulnerabilities
Microsoft has patched a total of four zero-day vulnerabilities in its July edition.
CVE-2024-38080 Windows Hyper-V Elevation of Privilege Vulnerability
(CVSS Score: 7.8) (Severity: Important)
This vulnerability allows an attacker with low privileges to gain SYSTEM privileges, leading to unauthorized access to sensitive information, modification of system configurations, and possible disruption to services running on the Hyper-V host or virtual machines.
The CVE-2024-38080 vulnerability is actively exploited and is part of the CISA Known Exploited Vulnerability list.
Microsoft claims that the CVE-2024-35264 vulnerability as Exploitation Detected.
CVE-2024-38112 Windows MSHTML Platform Spoofing Vulnerability
(CVSS Score: 7.5) (Severity: Important)
This vulnerability affects Microsoft’s MSHTML browser engine, which is present on desktop and server versions of Windows operating systems. An attacker could use this vulnerability to spoof content or resources, leading to unauthorized access to sensitive information that can significantly impact confidentiality, integrity, and availability. The attacker must trick the potential target into opening a malicious file for the vulnerability to work.
The CVE-2024-38112 vulnerability is actively exploited and is part of the CISA Known Exploited Vulnerability list.
Microsoft claims that the CVE-2024-38112 vulnerability as Exploitation Detected.
CVE-2024-35264 .NET and Visual Studio Remote Code Execution Vulnerability
(CVSS Score: 8.1) (Severity: Important)
This vulnerability exists in Microsoft’s .NET 8.0 and Visual Studio 2022 and arises due to a race condition during the processing of HHTP/3 streams, especially when an HHTP/3 stream is prematurely closed while its request body is still being processed, allowing the attacker to access the freed memory and execute the arbitrary code on the targeted system.
Microsoft claims that CVE-2024-35264 vulnerability as Exploitation Less Likely.
CVE-2024-37985 Arm: CVE-2024-37985 Systematic Identification and Characterization of Proprietary Prefetchers
(CVSS Score: 5.9) (Severity: Important)
This vulnerability is a third-party (Intel) CVE that Microsoft integrated into the July Patch Tuesday release. The CVE-2024-37985 vulnerability affects specific ARM-based operating systems. An attacker who successfully exploits this vulnerability could view heap memory from a privileged process running on the server.
Microsoft claims that the CVE-2024-37985 vulnerability is Exploitation Detected.
A few other notable vulnerabilities Microsoft fixed during its July editions are as follows.
- CVE-2024-38023 Microsoft SharePoint Server Remote Code Execution Vulnerability

(CVSS Score: 7.2) (Severity: Critical)
This vulnerability exists in Microsoft SharePoint that allows an authenticated attacker with Site Owner permissions or above to upload custom files to a targeted SharePoint Server and create a dedicated API request to trigger the deserialization of file parameters.
- CVE-2024-38060 Microsoft Windows Codecs Library Remote Code Execution Vulnerability
(CVSS Score: 8.8) (Severity: Critical)
This vulnerability exists in Windows Imaging Component – a framework used for processing images, that allows an attacker to remotely execute code on the affected system with the same permissions as the vulnerable component.
- CVE-2024-38074 Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
(CVSS Score: 9.8) (Severity: Critical)
This vulnerability allows the attacker to execute remote code on the Sharepoint Server. The attacker could potentially use a PATH-based attack (CWE-426) to execute their own programs, access unauthorized data, or make unwanted changes to configuration.
- CVE-2024-38076 and CVE-2024-38077 Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
(CVSS Score: 9.8) (Severity: Critical)
This vulnerability exists in the Windows Remote Desktop Licensing Service, which allows the attacker to execute code remotely on the targetted system. An attacker can exploit this vulnerability over the network, requiring no user interaction and not needing any exploitation privileges.
We recommend that you patch these vulnerabilities immediately using SanerNow to secure your devices and prevent attacks on your organization.
Microsoft Security Bulletin Summary for July 2024
Microsoft released security updates for the following products in the July Patching Tuesday release.
- .NET and Visual Studio
- Active Directory Rights Management Services
- Azure CycleCloud
- Azure DevOps
- Azure Kinect SDK
- Azure Network Watcher
- Intel
- Line Printer Daemon Service (LPD)
- Microsoft Defender for IoT
- Microsoft Dynamics
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Streaming Service
- Microsoft Windows Codecs Library
- Microsoft WS-Discovery
- NDIS
- NPS RADIUS Server
- Role: Active Directory Certificate Services; Active Directory Domain Services
- Role: Windows Hyper-V
- SQL Server
- Windows BitLocker
- Windows COM Session
- Windows Core Messaging
- Windows Cryptographic Services
- Windows DHCP Server
- Windows Distributed Transaction Coordinator
- Windows Enroll Engine
- Windows Fax and Scan Service
- Windows Filtering
- Windows Image Acquisition
- Windows Imaging Component
- Windows Internet Connection Sharing (ICS)
- Windows iSCSI
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows LockDown Policy (WLDP)
- Windows Message Queuing
- Windows MSHTML Platform
- Windows MultiPoint Services
- Windows NTLM
- Windows Online Certificate Status Protocol (OCSP)
- Windows Performance Monitor
- Windows PowerShell
- Windows Remote Access Connection Manager
- Windows Remote Desktop
- Windows Remote Desktop Licensing Service
- Windows Secure Boot
- Windows Server Backup
- Windows TCP/IP
- Windows Themes
- Windows Win32 Kernel Subsystem
- Windows Win32K – GRFX
- Windows Win32K – ICOMP
- Windows Workstation Service
- Xbox Crypto Graphic Services
SanerNow vulnerability management and SanerNow patch management detect and automatically fix the vulnerabilities mentioned above by applying security updates. Use SanerNow to keep your systems updated and secure.

