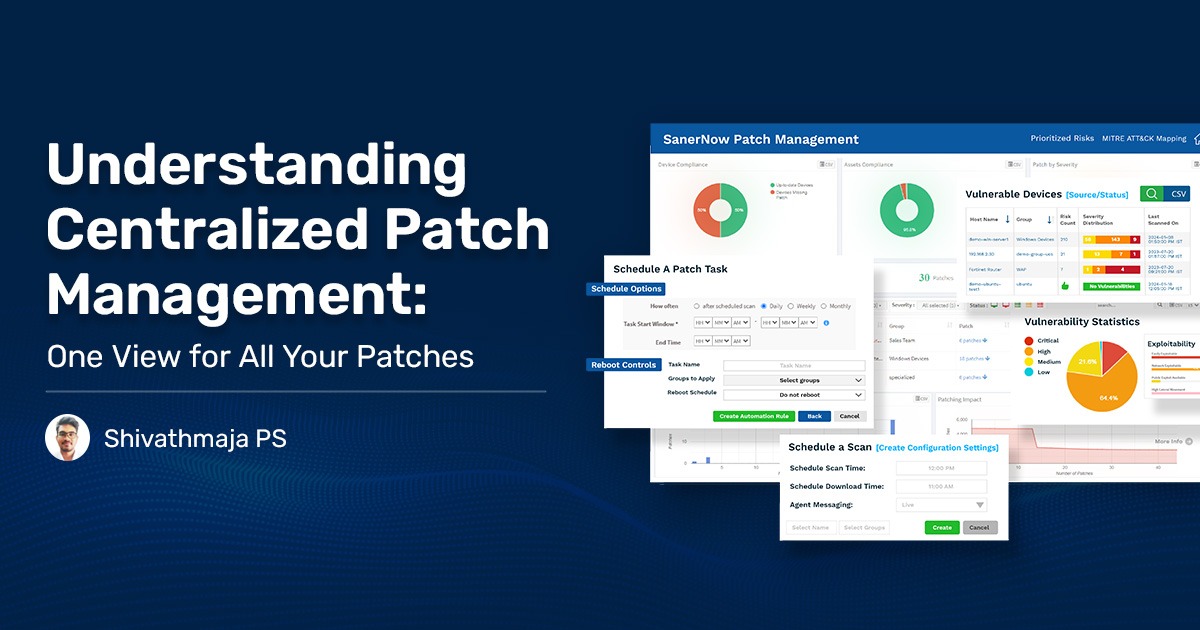
Would you rather have different dashboards for each of your OS groups and jump through multiple hoops to get info and patch your devices? Or just a single one to do it all? The answer is obvious, right? Centralized patch management is the superior way of doing things, and you are missing out on a lot of benefits and advantages.
Patch management, whether you like it or not, is the most critical part of your vulnerability management process, and you need it. So, let’s understand what centralized patch management (CPM) is, why it’s better, and how to implement an impactful CPM strategy with a patch management tool.
What is Centralized Patch Management (CPM)?
As the name suggests, centralized patch management (CPM) is an approach in which you deploy and manage the patches in your network from a single, centralized point.
The key point here is the term ‘central.’ Think of it as one view to control, maintain, and execute your network’s patching needs.
Typically, CPM collects info from around your multi-platform network, including data on operating systems, applications, and whatever other software in your IT infra. Not stopping there, it also distributes the patches to all your network devices and ensures that they are successfully installed.
So, Why is Centralized Patch Management Better?
Centralized PM, when implemented, gives you some game-changing benefits that can transform your organization’s security. Let’s dig deeper into the benefits:
- Improved Security: The obvious benefit of CPM is that you quickly and effectively respond to newly detected security risks. You can easily distribute patches to all affected systems, minimizing the window for a hacker to exploit that vulnerability.
- Improved Patch Deployment & Management: By unifying and centralizing, you deploy and manage all the patches in your network with ease. Furthermore, you can quickly and uniformly apply patches as well.
- Better Resource Efficiency: A key advantage of centralizing your patch management is that you can do more with less. Centralization brings better efficiency and reduces the redundant efforts you make if you use the other alternatives.
- Simplified Compliance: Many, if not most, industries have strict regulatory requirements for cybersecurity (think of CIS, NIST, HIPAA, etc.). You can enforce and maintain compliance with CPM. Due to its centralized nature, you get a single and easily manageable record of all the patching activity you’ve done as well!
Centralized PM vs Decentralized PM: Understanding the Difference
The biggest difference between CPM and decentralized PM, as the name suggests, is how and where the coordination and control of the patching occurs. On the decentralized side, different teams or tools typically handle their section of the patching. This could include different patching schedules, prioritization methods and overall implementation as well.
The main issue with decentralized PM is that it leads to communication issues and an overall lack of uniformity throughout your network.
CPM, on the other hand, solves these issues by centralizing all your network’s patching activities under one roof! You typically implement CPM by creating a dedicated team that handles the A-Z of patching from identifying, testing, and deploying patches across the organization.
With CPM, you get better coordination, consistency, and overall security while efficiently managing your resources.
CPM Strategy for Impactful Patching
Implementing centralized patch management might look like a daunting task at first glance, but it is definitely worth it. Better and efficient patching, reduced risks, and improved posture, who doesn’t want that?
Here are four vital steps that you must follow while implementing CPM in your network for impact patching:
- Visualize Your Infrastructure: The first step in your centralized patching strategy is to get a clear picture of your IT infrastructure. This means mapping out all your devices, applications, and systems. Visualizing your network is a must to understand what needs to be patched and how everything is connected. Your biggest helper here is a good asset management system tool that gives you a complete view of your environment.
- Scan & Scan Again: One scan is never enough. So, the second step in your strategy is to scan your systems regularly for vulnerabilities. Pretty simple, right? Automation significantly reduces your burden, and automated scanners can detect missing patches, outdated software, and potential security risks. So, this proactive approach means you can fix risks faster and lower the risk of attacks.
- Prioritize & De-prioritize: Not all risks are equal, and this logic works for patches, too. Some are critical for security, while others might just fix minor bugs or improve performance. So, it is your decision to patch or not to patch. The rule of thumb here is that critical security updates should be at the top of the list and deployed as soon as possible. Other, less urgent updates can be patched when you need them. By focusing on the most important patches, you make sure your resources are used where they’re needed most.
- It’s time to Patch Now: The final step of your CPM patching strategy is to deploy the patches! Once again, automation is your biggest friend, as it is easy to automate your patching activity in a centralized environment. Further, you also reduce the risk of human error and uniformly deploy patches without inconsistencies.
- Document, Rinse & Repeat: Implementing CPM should never be a one-time process. So, once you set up centralized patching, you must document the entire procedure and repeat it as well. This’ll ensure that the patching process is a recurring task that continuously works to manage patches, reduce risks and improve your network’s security.
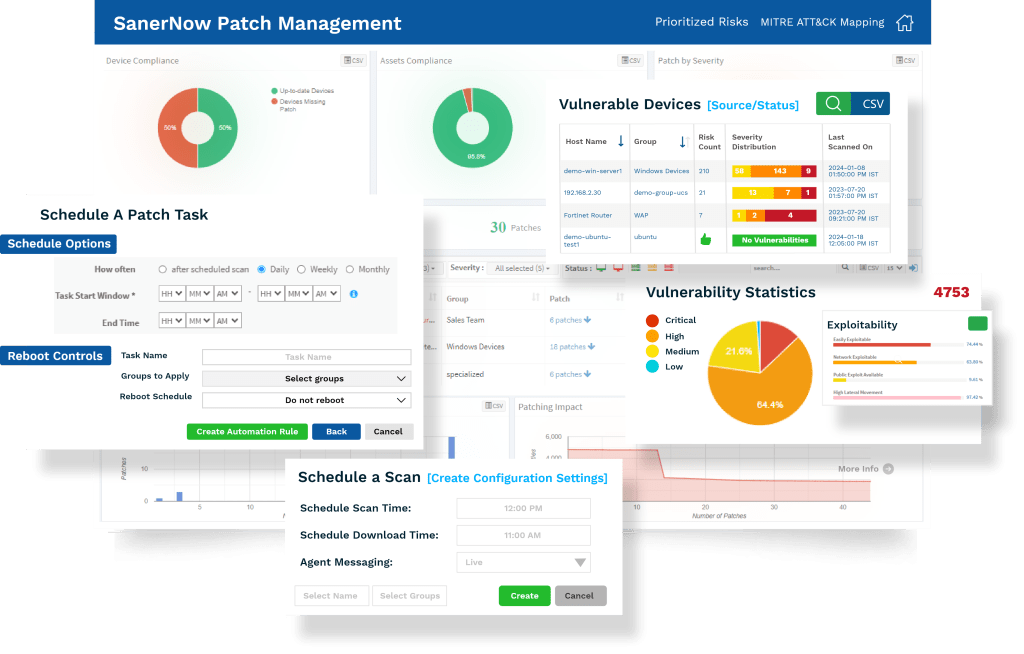
Conclusion
Patching is key, and CPM is the puzzle that can take your patch management to the next level. The centralized, unified, and uniform way of managing your patches provides many benefits and is a must to implement in your network!
SanerNow is your premier patch management solution that scans, detects, prioritizes, and deploys patches to reduce your attack surface.
Schedule a demo and check out how you can centralize and manage your patches!