How can you consistently identify and patch security risks while improving your cybersecurity posture. The answer lies in strong vulnerability management framework. 50% of organizations around the world experienced a breach caused by unpatched vulnerabilities. Without a structured approach to manage and kill vulnerabilities, enterprises tend to struggle. In this blog, we will break down the NIST vulnerability management framework and show you 5 essential steps to building a bulletproof vulnerability management solution.
What is Vulnerability Management Framework?
In simple words, a vulnerability management framework is a structured approach to kill vulnerabilities in your IT infrastructure. This consists of identifying, assessing, prioritizing, and remediating any type of vulnerability to reduce your chance of getting cyber-attacked.
What is NIST Vulnerability Management Framework?
The NIST Cybersecurity Framework (NIST CSF) 2.0 is a recognized vulnerability management framework developed by the National Institute of Standards and Technology (NIST). It provides a flexible and risk-based approach to managing vulnerabilities. The NIST 2.0 consists of five core functions: Identify, Protect, Detect, Respond, and Recover, with the addition of a new core function, Govern, which serves as the foundation for the entire framework.
Why is it Important to Have a Vulnerability Management Framework?
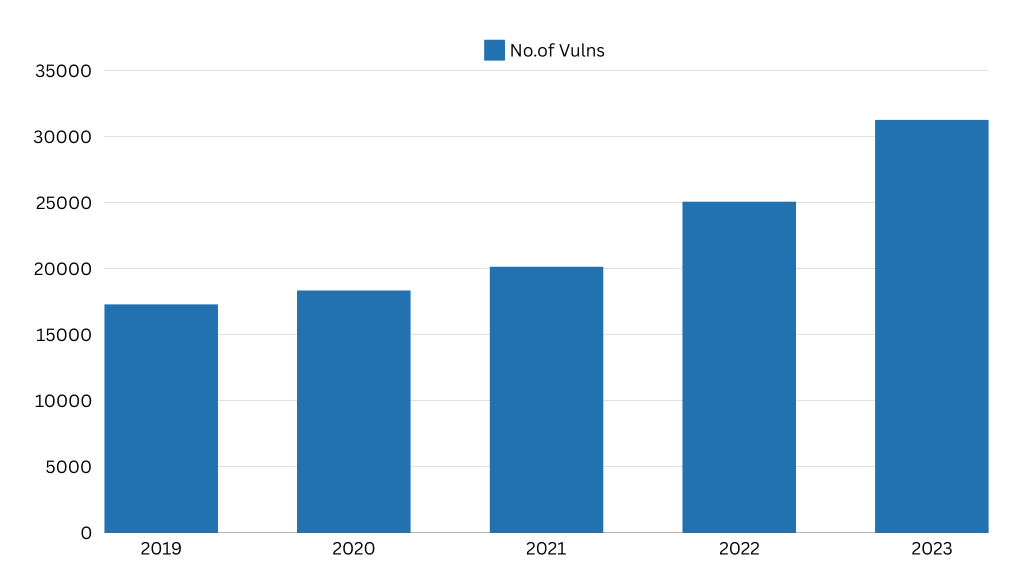
Having a vulnerability management framework has increasingly become important due to the rapid growth of newly detected vulnerabilities. If the frequency of attacks isn’t alarming enough, the number of vulnerabilities being discovered each year should be a wake-up call. In 2023 alone, 31,279 vulnerabilities were discovered. That’s roughly 85 new security flaws exposed every single day.
Say your IT environment has around 1,000 assets, and on average each asset has 50 unpatched vulnerabilities. That’s 50,000 vulnerabilities that need to be patched. A well-defined vulnerability management framework gives your team a structure to manage this task.
5 Steps to Build a Vulnerability Management Framework with SanerNow!
- Visibility – The first and critical step in Continuous vulnerability and exposure management is the discovery of all IT assets, including routers, switches, and other network devices. A thorough inventory and tracking of ALL devices in a network. Cyberattackers often exploit forgotten and outdated devices in a network. And you can’t protect what you can’t see, and missing out on even one device can pose a huge risk. So, having complete visibility is critical to ensure all points of entry are covered.
- Identify – The second step involves identifying vulnerabilities and weak points in your IT infrastructure. This requires conducting comprehensive vulnerability scans across the entire attack surface to determine the total number of vulnerabilities present. Perform regular scans and identify risky vulnerabilities like CISA KEVs (Known Exploited Vulnerabilities). But simply running scans isn’t enough, it’s important to make this process a regular routine.
- Assess – Understanding vulnerabilities and exposures and their potential risk systematically and continuously monitoring the devices is the next step in continuous vulnerability and exposure management. A medium-risk vulnerability might have exploits in the wild, making it very dangerous, or a high-risk vulnerability might be in a rarely used application making it practically ineffective. So, detecting security risks isn’t enough to stop cyberattacks and is critical to assess the detected vulnerabilities before jumping into mitigation.
- Prioritize – Vulnerabilities and exposures might be significant in numbers, and not all vulns require the same effort to remediate. While all vulnerabilities need your attention, some require large amounts of time and provide little value in protecting your network. Efficient sorting of risks and vulnerabilities based on criticality and other metrics to choose “what to remediate first” prioritization should be automatic. With business context, exploitability, and other factors in mind, SSVC based vulnerability prioritization allows you to remediate the most critical ones first.
- Remediate – The most crucial step of continuous vulnerability and exposure management program is quickly remediating the detected vulnerabilities. It is the process of remediating vulnerabilities, exposures, and other security risks by fully fixing or patching them while maintaining compliance. It becomes the most important step of a vulnerability management program. Following this just ensures that cyber-attackers don’t have a backdoor to enter your organization.
Conclusion
Following the vulnerability management framework, does the dream work of yours to defeat vulns in your organization’s IT. The NIST framework of handling a vulnerability should also be considered. Visibility, Identification, Assessment, Prioritizing, and Remediate are all you need to ensure your company is always 10 steps ahead of a cyberattack.


